Download a copy of any Facebook Page

Here's the full story of how I discovered a Facebook bug worth $8,000 USD by discovering three (3) different vulnerabilities in a Facebook Page.
Background
Matt Navarra, TheNextWeb's social media director, posted a tweet last January 5, 2016 about a Facebook feature called the "Download Page"
Download your Facebook Page? New or have i just never spotted it before? pic.twitter.com/LvcIn4gIbQ
— Matt Navarra | 🚨 #StayAtHome (@MattNavarra) January 5, 2016
After discovering the new feature, I immediately look for a flaw and quickly found three (3) vulnerabilities:
- Unauthorized Access in General Settings - By default, the Admin can only access this.
- Vertical Privilege Escalation in Download Page feature
- Insecure Direct Object Reference in Download Page feature
Reconnaissance
I conducted some research about Facebook Pages and found this page:
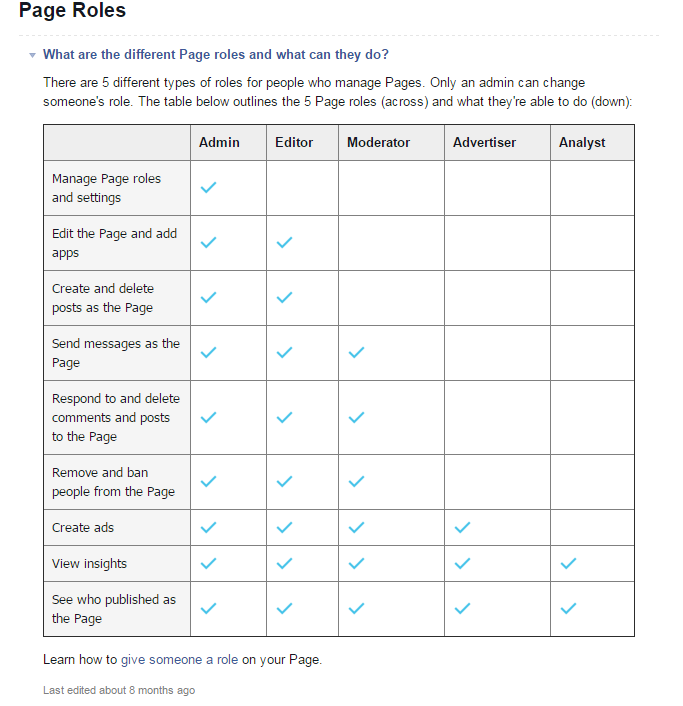
With that, I already knew that there's a security issue because as an Editor of a Facebook page I was able to access the General Settings.
I continued conducting some research and found this another page:
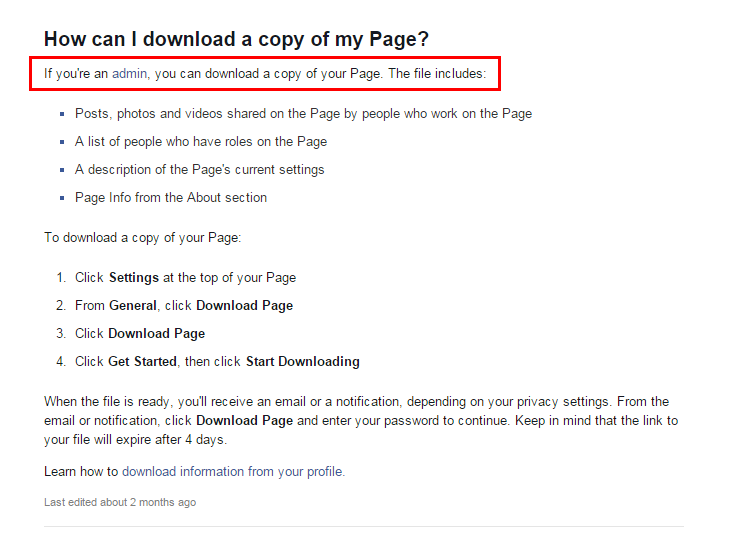
The "Download Page" feature is accessibly to Facebook Page Admin only. If you're not an admin, you are not allowed to download a copy of the page.
Exploitation
Privilege Escalation
Initially, I created two (2) different accounts and one (1) facebook page.
- Account A: Admin
- Account B: Editor
Using the Admin-role account, I downloaded a copy of the Facebook page and captured its request using Burpsuite tool.
The POST requests are like this:
<form action=”/dyp/dispatch/?page_id=12345" method=”post”>
<input type=”hidden” name=”fb_dtsg” value=”AQG21wqhJ0g4" automcomplete=”off”>
<button value=”1" type=”submit”>
Get Started
</button>
</form><form rel=”async” action=”/dyp/download/?page_id=12345" method=”post”>
<input type=”hidden” name=”fb_dtsg” value=”AQHnr-Cvy88k” automcomplete=”off”>
<button value=”1" type=”submit”>
Download Page
</button>
</form>With that kind of request, I immediately think of other possible scenarios like "What if I can also download a copy of other Facebook pages?"
But before that, I continued exploiting the Privilege Escalation. So I sent the POST requests to Repeater Tab of Burp and changed the sessions from Admin account's session to Editor account's session.
Sent the requests back to Facebook and it worked! I was able to download the copy of the Facebook page without having an admin role.
Insecure Direct Object Reference
Going back to other scenario, I used the same POST request and just changed the value of page_id parameter from 12345 to other Page ID of other Facebook pages.
Then I sent the requests back to Facebook and it worked!
Remediation
How did Facebook Security Team fixed these vulnerabilities?
- If you’re an Editor of a Facebook Page, you are no longer access the General Settings anymore and you will be redirected to About Section of the Facebook Page.
- They temporarily took down the new feature to fix the issues internally.
Timeline
| Date and Time | Activity |
|---|---|
| Jan 6, 2016 1:44 AM | Report submitted to Facebook |
| Jan 7, 2016 2:16 AM | Angelo of FB Security Team responded that they will investigate the issue. |
| Jan 9, 2016 3:44 AM | Jimio of FB Security Team responded that they patched the issue. |
| Jan 9, 2016 3:50 AM | I responded that the issue is no longer working on my end. |
| Jan 9, 2016 7:43 AM | Facebook rewarded me $8,000 USD Bug Bounty. |
