DumpMe (Memory Image Forensics)
Scenario
One of the SOC analysts took a memory dump from a machine infected with a meterpreter malware. As a Digital Forensicators, your job is to analyze the dump, extract the available indicators of compromise (IOCs) and answer the provided questions.
Given File
Triage-Memory.mem
Tool
Volatility
Challenge Questions
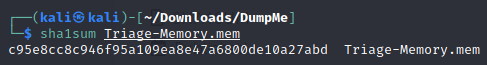
- What is the SHA1 hash of triage.mem (memory dump)?
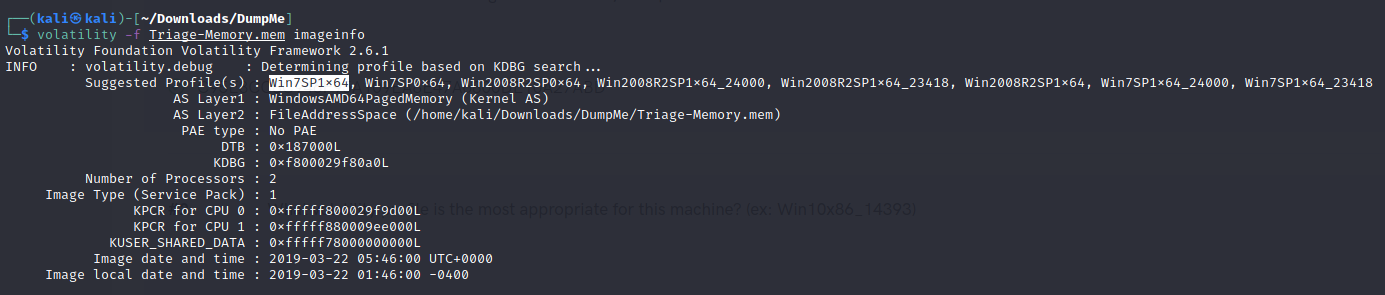
- What volatility profile is the most appropriate for this machine?
- What was the process ID of notepad.exe?
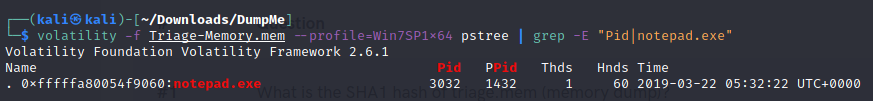
- Name the child process of wscript.exe.
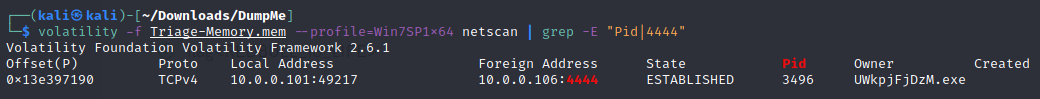
- What was the IP address of the machine at the time the RAM dump was created?
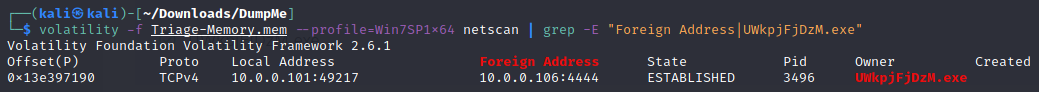
- Based on the answer regarding the infected PID, can you determine the IP of the attacker?
- How many processes are associated with VCRUNTIME140.dll?
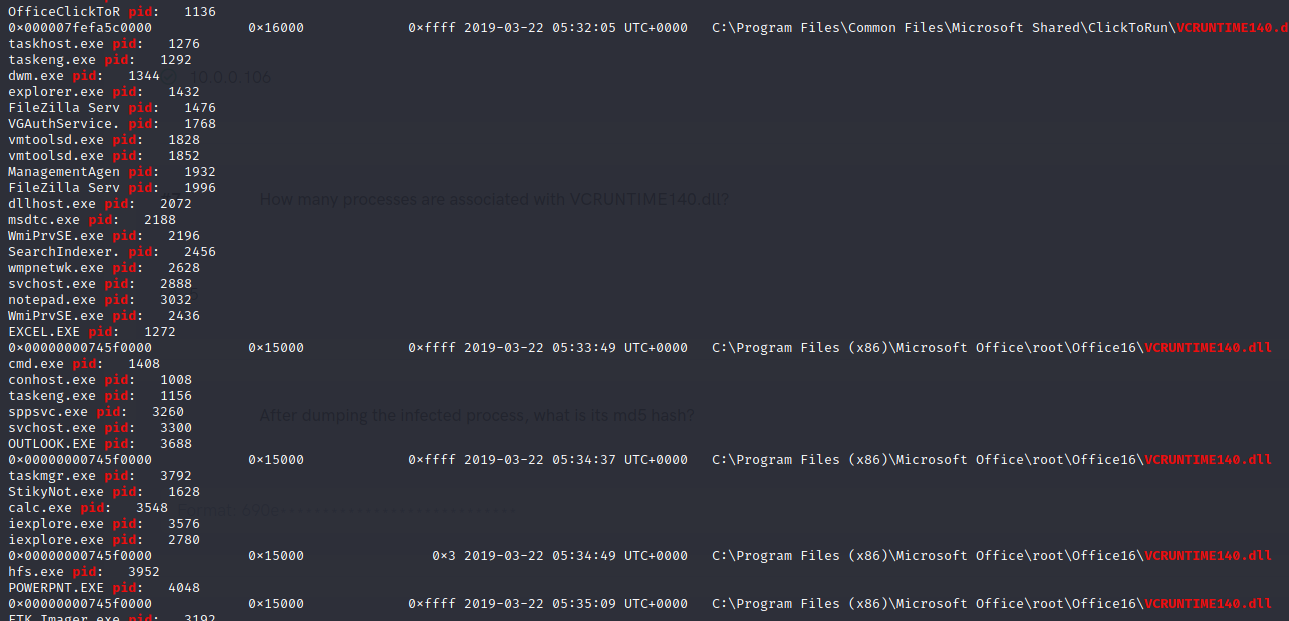
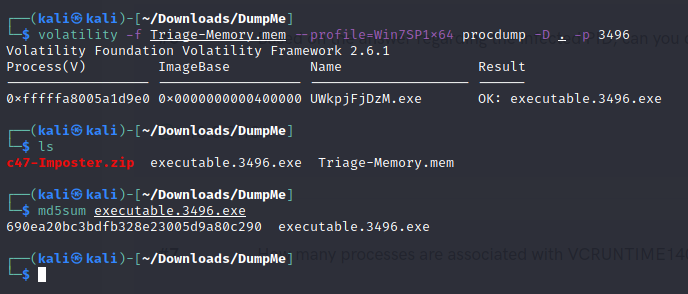
- After dumping the infected process, what is its md5 hash?
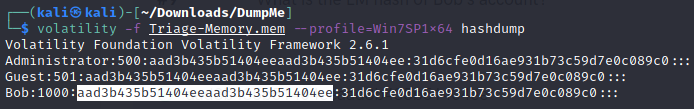
- What is the LM hash of Bob's account?
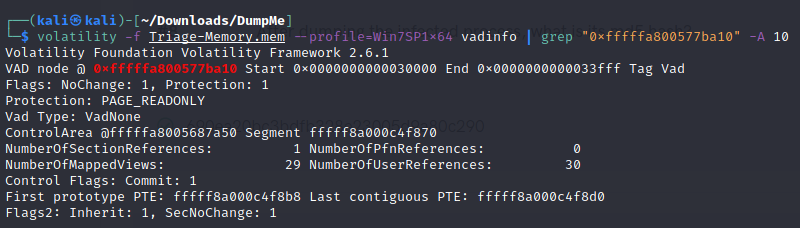
- What memory protection constants does the VAD node at 0xfffffa800577ba10 have?
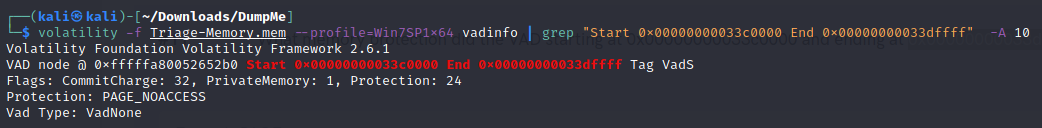
- What memory protection did the VAD starting at 0x00000000033c0000 and ending at 0x00000000033dffff have?
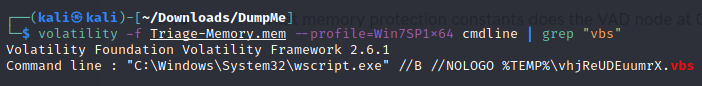
- There was a VBS script that ran on the machine. What is the name of the script? (submit without file extension)
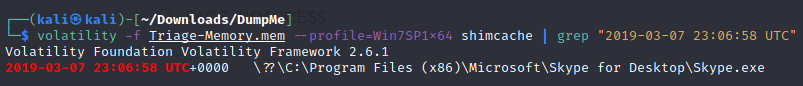
- An application was run at 2019-03-07 23:06:58 UTC. What is the name of the program? (Include extension)
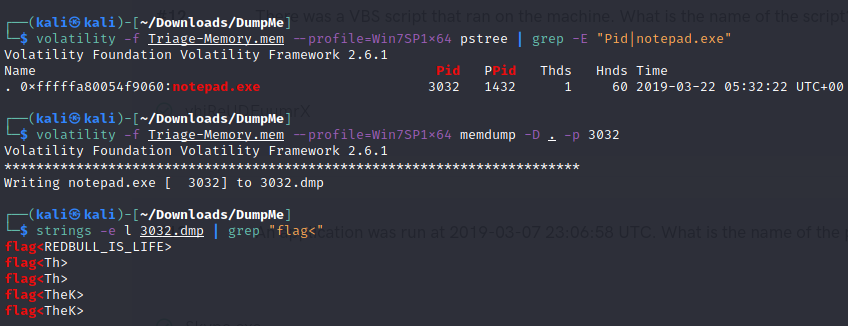
- What was written in notepad.exe at the time when the memory dump was captured?
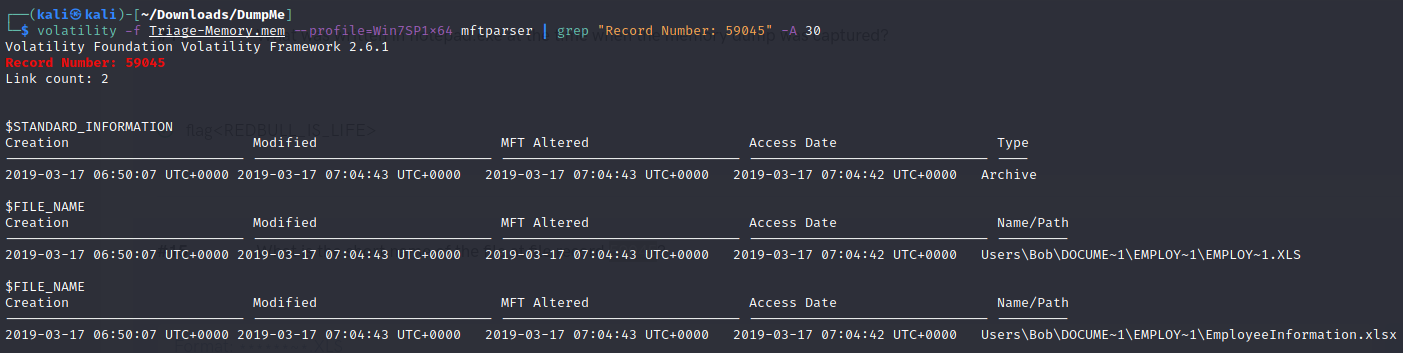
- What is the short name of the file at file record 59045?
- This box was exploited and is running meterpreter. What was the infected PID?