ROOTCON - Easter Egg Hunt 2020: Space Challenge
The author gave us this file for this challenge: diwata_satellite_canbus_dump.log
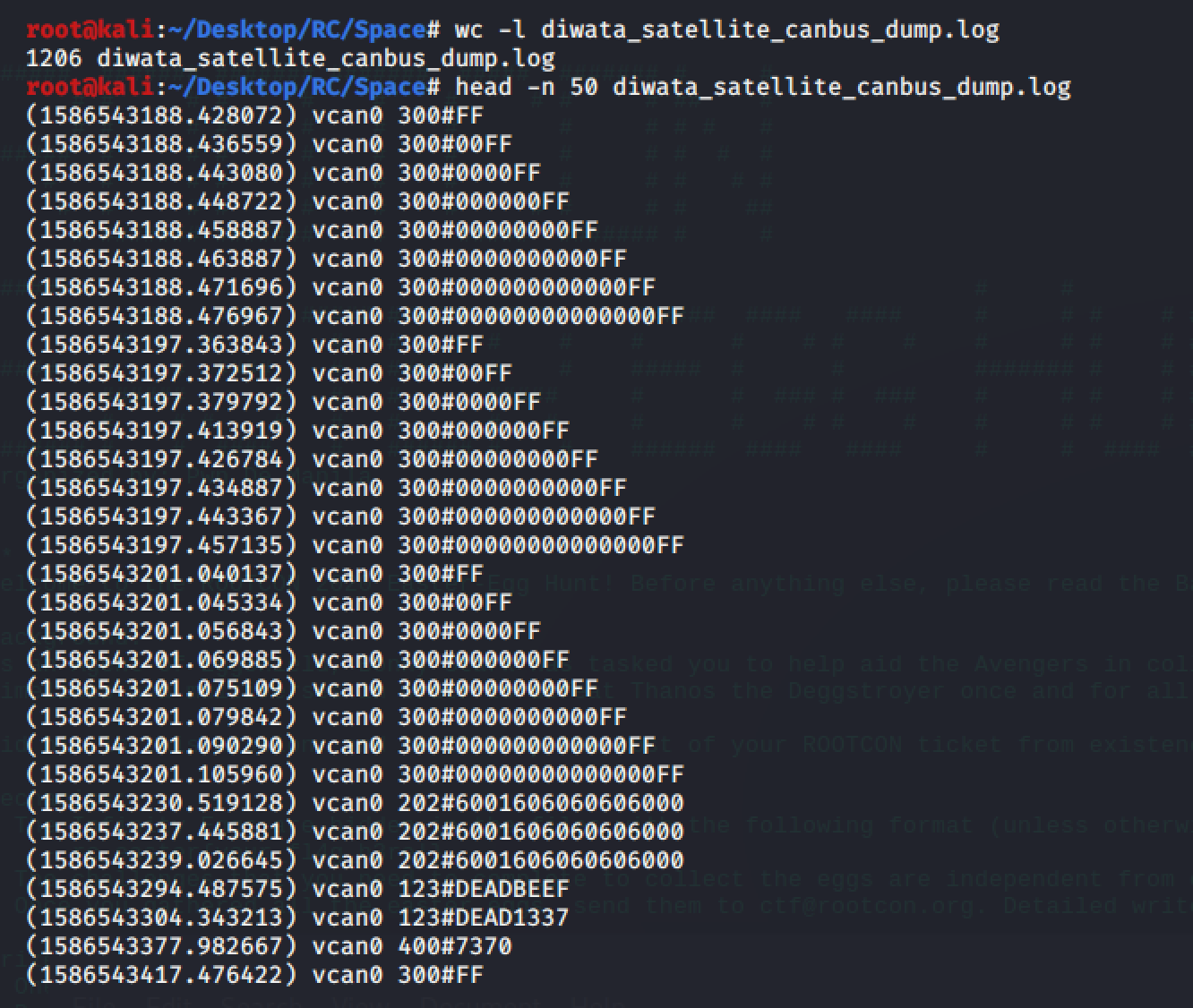
The file contains a canbus dump.
Searching in Google about CANBus led me to these blogs:
After reading the blog, I learned that I need to install a tool called can-utils and clone the Instrument Simulator Cluster from GitHub.
sudo apt-get install can-utils -y
Running the setup_vcan.sh inside the cloned ICSim will help us create a vcan0 interface in order to simulate the car network.
If you’d like to try the simulator, you may run the icsim pointing to vcan0 interface.
./icsim vcan0
You also need to run the controls file which is a controller in order to send traffic on interface vcan0.
But to solve this challenge, you only need the following tools:
- cansniffer
- canplayer
First, I fired up cansniffer to sniff every traffic from the diwata_satellite_canbus_dump.log and I then started running the traffic from the CANbus dump file using canplayer.
The content of the log file is divided into columns. The first column is time, the second one is ID, the third and last columns are data.
During the replay attack, I quickly noticed the first few lines:
0.000000 300 00 00 00 00 00 00 00 FF ........
0.000000 300 00 00 00 00 00 00 00 FF ........
0.000000 300 00 00 00 00 00 00 00 FF ........
0.000000 202 60 01 60 60 60 60 60 00 `.`````.
0.000000 123 DE AD BE EF ....
0.000000 123 DE AD 13 37 ...7
0.000000 400 73 70 sp
0.000000 300 00 00 00 00 00 00 00 FF ........
0.000000 510 10 AD 01 3C F0 48 12 0B ...<.H..
0.000000 401 61 63 65 73 61 74 65 6C acesatel
0.000000 7F1 03 22 F1 90 00 00 00 00 ."......The ID 400 has the sp value and the ID 401 has the value acesatel. If you combine those two values, it will give us spacesatel.
I then look for ID 402 and I found:
0.000000 402 6C 69 74 65 73 68 61 76 liteshavThe updated value is now spacesatelliteshav.
Next ID is 403 and scrolling down to sniffed CANbus logs will give us the last part of flag:
0.000000 403 65 63 61 6E 74 6F 6F ecantoo
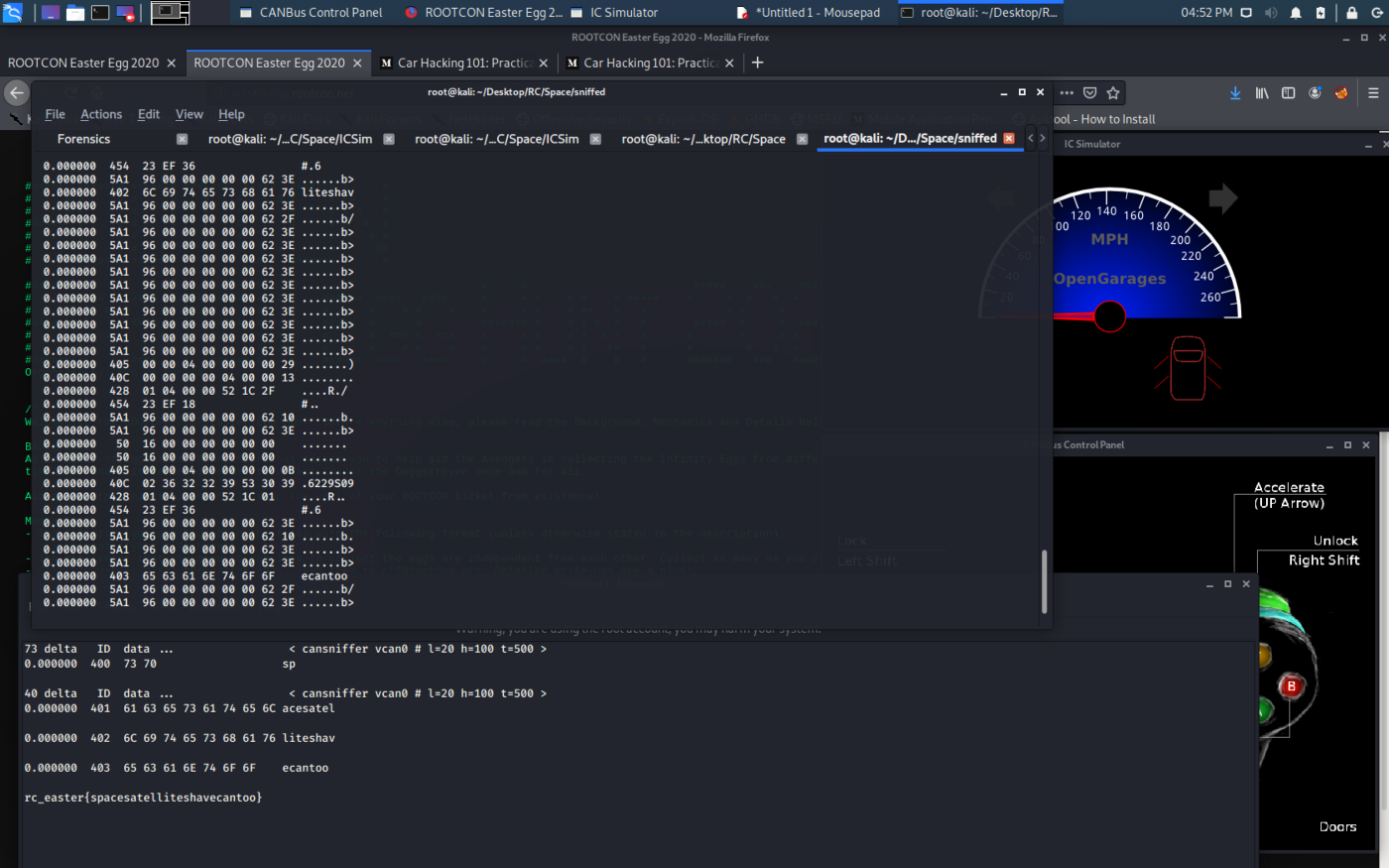
The flag is rc_easter{spacesatelliteshavecantoo}.

